How can you Identify a Phishing Email? Explore with Examples!
Imagine waking up with an urgent warning email from the bank about unauthorized activity on your account. How dangerous that situation races and out of nowhere you are in a situation where you need to click the attached link. After realizing that email is for phishing, it’s too late. You realized that you are now a victim of phishing scams? Do not know how can you identify a phishing email and avoid phishing scams? Let’s discuss this thoroughly in this guide.
Phishing emails are deceptive messages that are designed by scammers. These are specially designed to trick you into revealing sensitive information or detect malware in Email. These emails often impersonate trusted organizations such as banks, government agencies, or well-known organizations to force you into clicking malicious links or sharing personal details.
This is the most common type of Email Threat that usually targets individuals and large businesses alike. Cybercriminals use advanced tactics like urgency, fear, and curiosity to manipulate the receipts into acting quickly without any verification of the authenticity of the message. Research says that one single phishing email can lead to huge financial loss, identity theft, or even a massive data breach.
So, let’s understand this through this guide what is how can you identify a phishing email or message?
How to Identify Phishing Email and Avoid Phishing Scams?
While identifying phishing emails often contain urgent requests, suspicious email attachments, or links to trick you into revealing sensitive information. Recognizing these characteristics can help you avoid falling victim to scams. Below are the most common signs of phishing emails:
Suspicious Sender Email Address
Cybercriminals often use spoofed email addresses email addresses that closely resemble legitimate ones but contain slight variations.
For example, instead of support@payal.com, a phishing email might come from support@payall.com or secure-payal@xyz.com. Therefore, always check the sender’s address carefully before taking any action further.
Asks for Sensitive Information
All authentic and legitimate users or businesses never ask for sensitive information such as account details or personal information by email. So always check email properties first.
Cybercriminals Often Use Different Domains
While you are identifying a phishing email or message always look after the domains. Many scammers often attempt to impersonate legitimate companies mane. Always make sure the email is received from a verified user or domain.
For example- a message from Amazon will come from @amzon.com.
Phishing Emails is not Personalized
Legitimate companies you’ve done business with will typically address you by name. They will not use even generic phrases like “Dear Valued Member,” “Dear Customer,” or simply “Hello.” If an email from a bank or service provider doesn’t use your real name, treat it with suspicion.
Urgent or Threatening Language
Phishing emails create a sense of urgency to pressure you into acting quickly. Common scare tactics include:
- “Your account will be suspended if you don’t update your details immediately.”
- “Unusual activity detected! Confirm your identity now to avoid account closure.”
- “You’ve won a prize! Claim it within 24 hours before it expires.”
Poor Grammatical Errors, Spelling, or Unprofessional Formatting
All highly certified and reputed companies use professional language and proper grammar. While identifying a phishing email if you get a spelling error or grammatical mistake it’s a clear indication of a phishing attempt.
Some Examples of Phishing Emails
Real-time examples will surely help you to perform spam email analysis. Also helps you spot them more easily in your inbox. Below are a few common types of phishing attempts that many users encounter:
1. How to Detect Fake Bank Alert Email
Example- Subject: “Important: Action Required to Secure Your Account”
“Dear Customer, we’ve detected suspicious activity on your account. To prevent any unauthorized transactions, please confirm your identity by clicking the link below immediately.”
This email creates an urgency for a user to prompt the recipient to click on a link to secure their account. However, the link might redirect to a fake website that looks identical to the bank’s official site, where attackers can steal login credentials.
How to Spot a Phishing Email?
- This shows generic greetings (“Dear Customer”) instead of your name
- It shows a sense of urgency that pressures you to act quickly.
2. How to Spot Fake Invoice or Receipt
Example- Subject: “Invoice #12345 – Your Payment Was Successful!”
“Dear [Your Name], attached is your receipt for the recent transaction of $300. If you did not authorize this payment, please click the link below to dispute the charge.”
This phishing email pretends to be from a retailer or service provider. It claims that the recipient has made a payment, but the link leads to a phishing site designed to steal personal or financial information.
How to Spot the Phishing Email
- Unexpected attachments (invoice or receipt you weren’t expecting).
- Generic language, no specific details about the purchase.
- Inconsistent sender email address or domain.
How Can You Identify a Phishing Email Through Advanced Software?
There are so many purposes to identify emails like phishing email forensics, cybersecurity purposes, etc. There are various manual methods through which you can identify a phishing email. What you can do is simply opt for the best Email Analysis Software for the detect and investigate each emails as a priority for phishing.
MailXaminer is a global leader that easily detects suspicious emails with not just the data but clearly shows different angles of the emails that make it suspicious. Here’s how can you identify a phishing email or message through this software professionally.
With the help of this software, you can perform email header analysis that contains detailed email metadata. A phishing email might have a manipulated or forged “From” address, and this tool can reveal discrepancies in the sending path that would be impossible to identify manually. This includes detecting “spoofed” email addresses and unusual routing information that indicates the email was sent from a suspicious source.
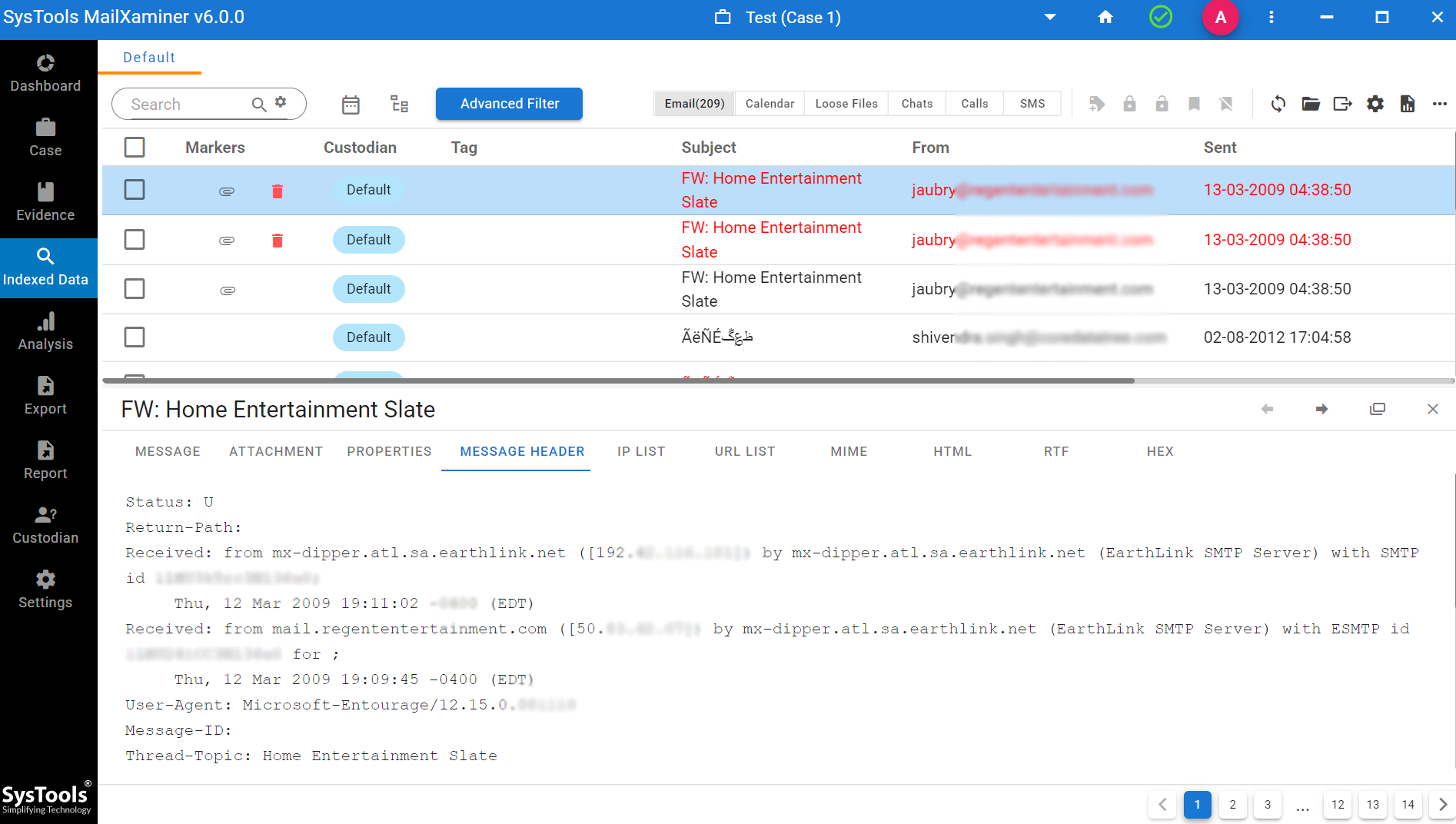
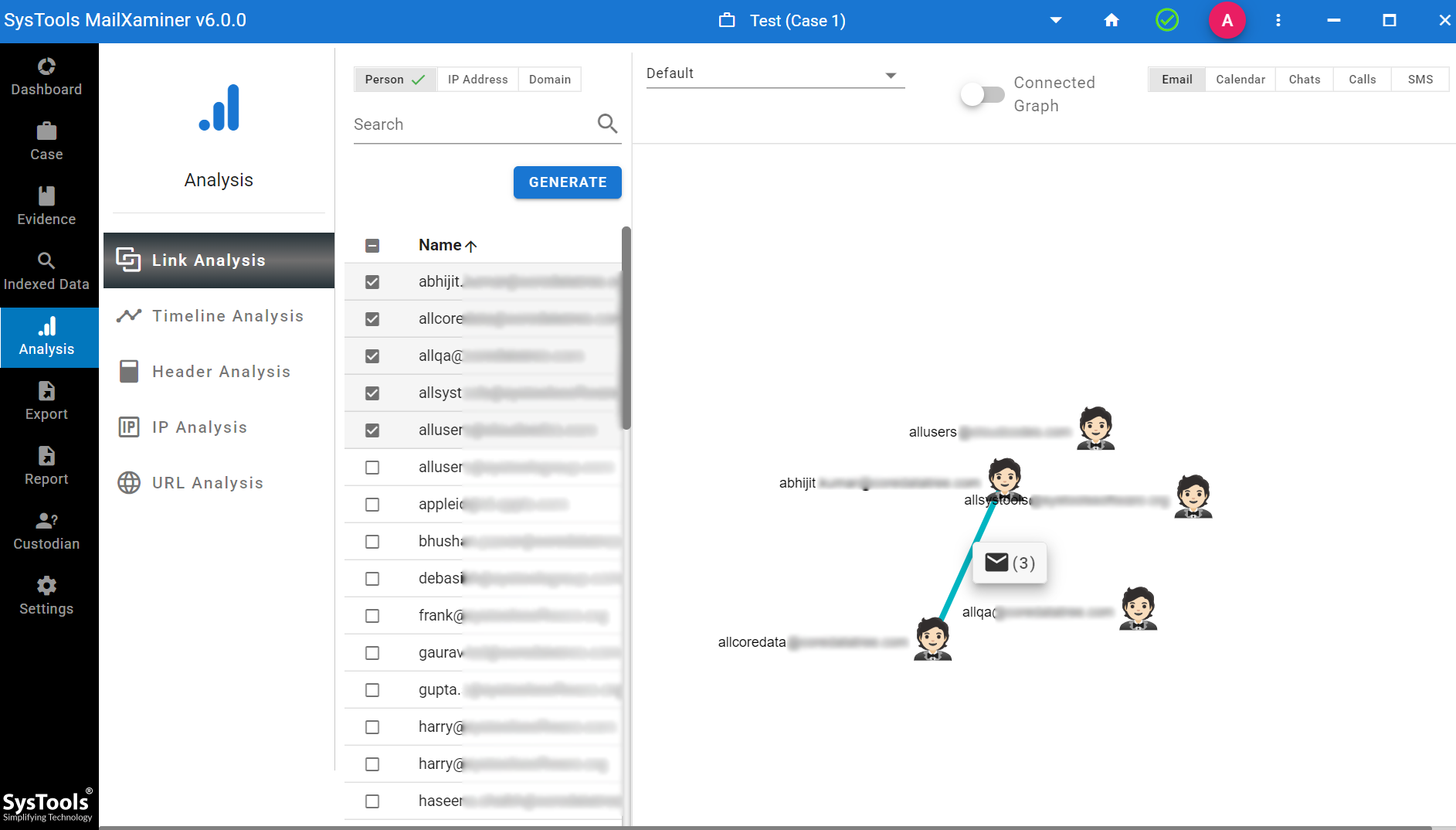
Not only this you can also provide the option to check the link analysis to know the communications between the email addresses.
Conclusion
Every organization has to face different challenges which may also include email scams and phishing attacks. “how can you identify a phishing email?” is one of the common queries among users these days. Finally, this blog states the necessary preventive steps that should be taken to avoid phishing scams. Besides this, users can also use suggested software to investigate the scenario. However, by recognizing and avoiding phishing scams and cybercrime, a user can protect the organization from being attacked soon.

