Proper Tagging and Labeling of Evidence in Digital Forensics
Often times, the investigators during the analysis process get innumerable thoughts with regards to the crime scene. However, after some days, they tend to forget those things because later thoughts clash the previous. Proper tagging and labeling of evidence in digital forensics require less effort of evidence examiner in data analysis. It also helps them to connect a series of evidential facts systematically.
“EXTRAORDINARY CLAIM DEMAND EXTRAORDINARY EVIDENCIAL FACTS”
Often times, the investigators during the analysis process get innumerable thoughts with regards to the crime scene. However, after some days, they tend to forget those things because later thoughts clash the previous. In digital forensics, tag and label the evidential items during the analysis process will help the forensics examiners in further investigation. It also helps them to connect a series of evidential facts systematically.
Therefore, in this article, you will get to know the need for email tagging and labeling during the investigation process. Here, we will also give you the best techniques and tips to do proper email evidence labeling and tagging to mark evidence.
Need for Proper Tagging and Labeling of Evidence
In the digital forensics investigation process, the investigators can have a large amount of email data. It is not easy to remember the facts and information related to each file. Then, the situation leads to the demand for labeling and tagging the files. By proper tagging and labeling of the evidential documents, investigators make their work easy as they will be able to identify the facts corresponding to each item at any time in the future.
What is Chain of Custody in Computer Forensics?
In the field of digital forensics, a chain of custody refers to the forensic links of electronic evidence that includes the chronological documentation, etc. It usually indicates the collection of information, the sequence of control and transfer of data, and track pieces of evidence. It also used to document the date/time, collected and transferred information, etc.
Simply, the chain of custody creates when investigators pick out some important facts and tagging that facts with data. After it, connect the series of that facts to find the pieces of evidence.
Importance of Labeling and Tagging Items of Evidence
In digital forensics, labeling forensic evidence is not a protocol to follow, it is involved in the process of investigation to organize the facts of a case. By proper tagging and labeling of evidence, investigators reduce the risk to tamper the evidence thereby enables to easily identify the evidence for further investigation in the near future. While tagging the email files, make sure that the content and chain of custody information should be mentioned understandably. Proper evidence tagging to mark evidence is an important part of the investigation process helps eliminate the confusion within the department.
Labeling Forensic Evidence in a Right Way!
The process of labeling forensic evidence is now added to the known forensic tool MailXaminer. The software provides this feature to effortlessly label forensic evidence in the email files to ease out the investigation process. By this, it becomes easy to analyze the data and add or remove labels with each file.
This is a result-oriented email forensics tool that can be used not only by tech-savvy users but also by users having less technical expertise. All because of its simplified user interface and countless features. This tool allows the investigation officers to diligently examine the crime scene and simplify the process.
Here’s How to Tag Email Files
While undergoing the investigation process, digital data classification is done by proper tagging and labeling of evidence. This software provides the functionality to add or remove evidence labels, tags from the data files. Follow the procedure for evidence tagging with any of the processed files:
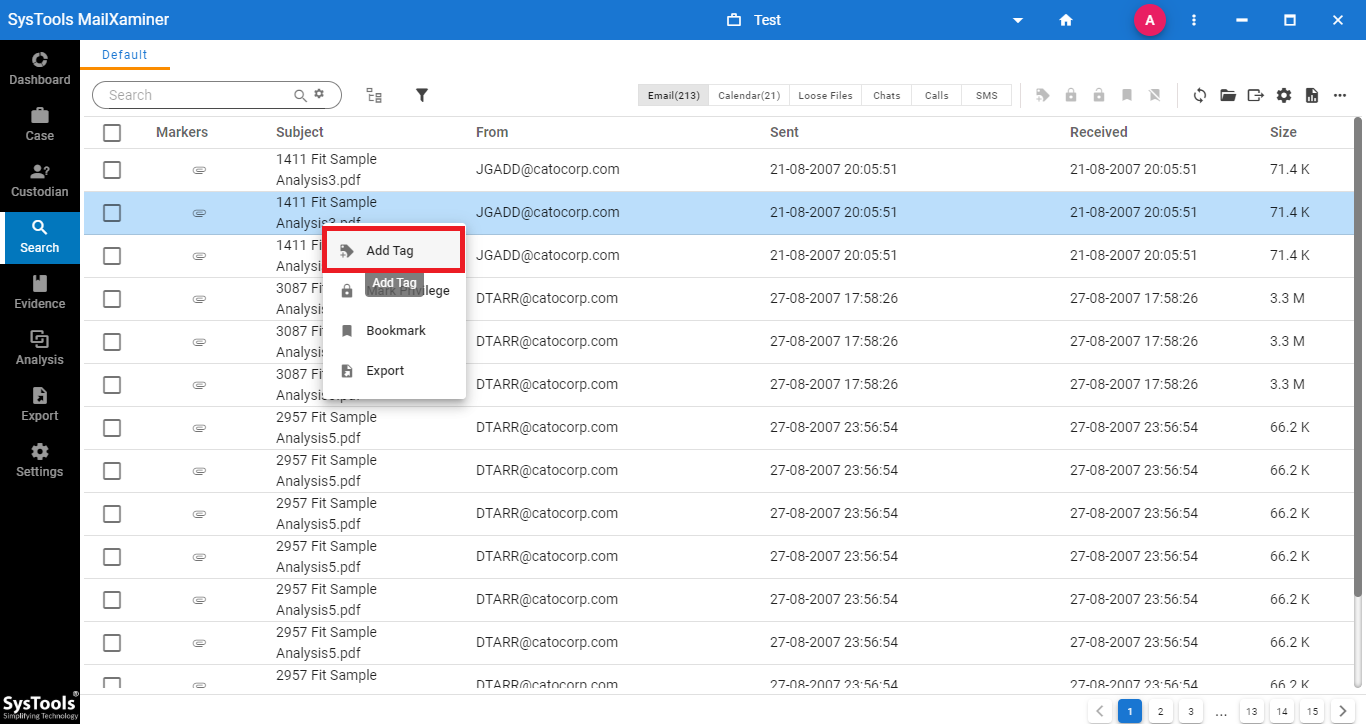
- When a user opens the file into the software, it will get the data files on the screen. Just mark the files to which the user wants to add the information. Then, right-click and choose to Add Tag for labeling forensic evidence.
ADD TAG: – It provides the facility to add a new tag to the data file.
- This tool also allows us to remove or delete the existing tag from the data files.
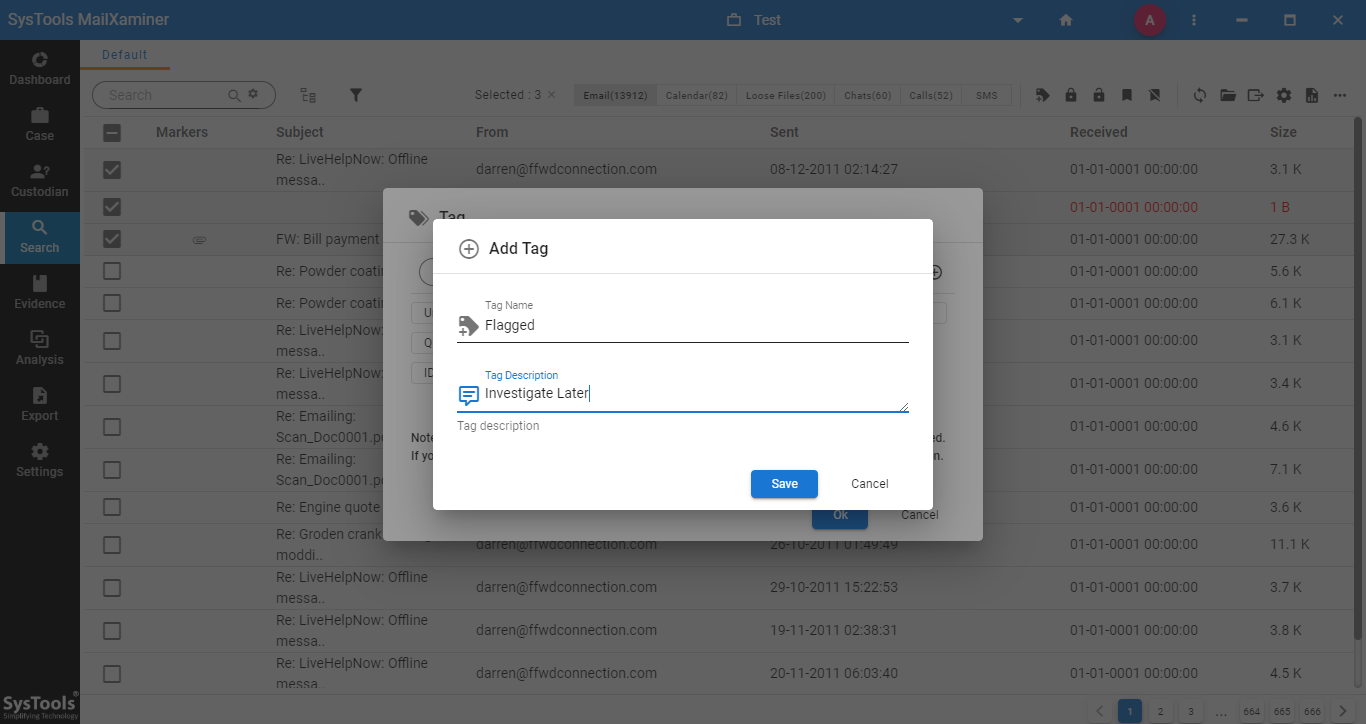
- In proper tagging and labeling of evidence, software allows to add new tag by clicking on Add Tag option. A pop-up window will display having the following fields i.e. Tag Name and Tag Description.
Tag Name:- Specify the name for the Tag.
Tag Description:- Describe the information related to the email content.
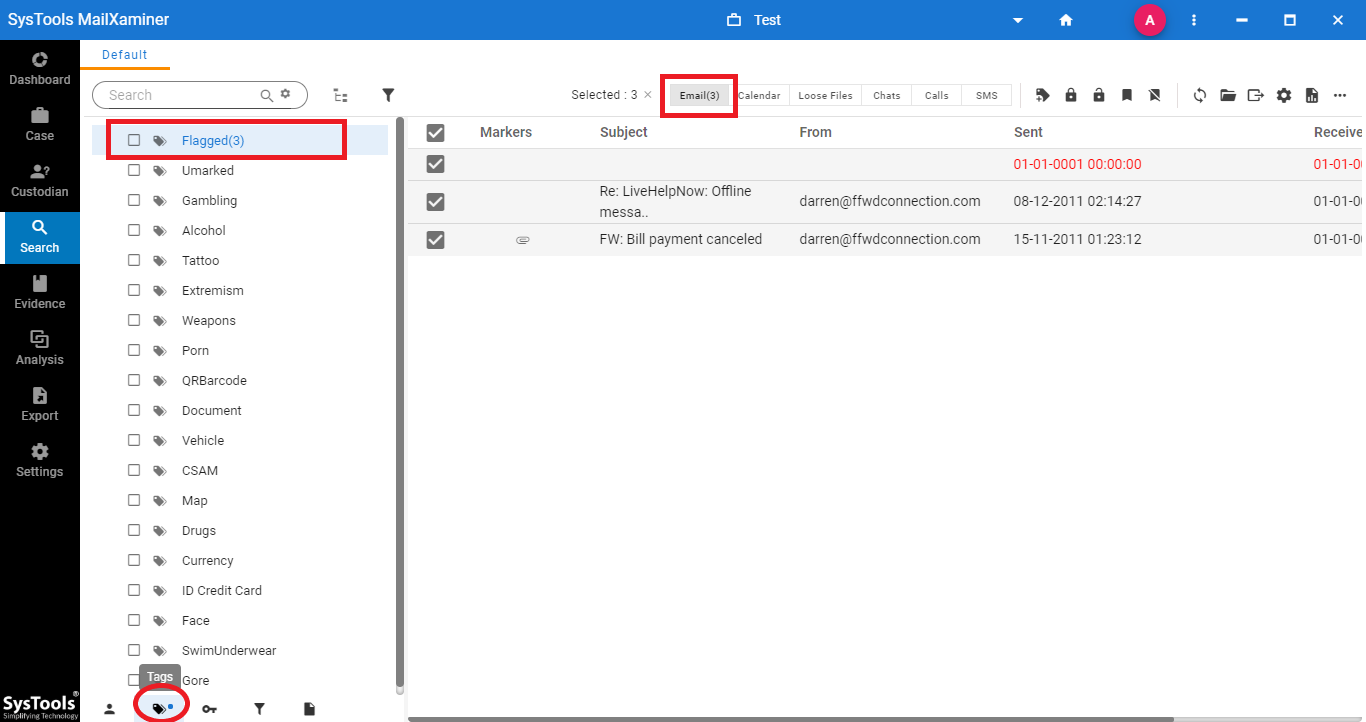
- In order to search the tagged information, opens the Tags tab. The screen will display the tagged data with specified tags and information. It allows to easily search of specific information to the investigators. To see evidence under any particular tag, just find the tag from the list and click on it.
Final Words
In the systematic approach of digital forensics investigation, the digital forensic experts may have numerous reasons for tagging and labeling items of evidence data systematically. To fulfill these requirements, we have described proper tagging and labeling of evidence to create a chain of custody in computer forensics using the aforementioned software. It is trustworthy and widely using forensics software, which has recently added the functionality to tag the data with unrevealed facts and information. To conclude, tag and label the evidential information out of the bulk digital forensic data will help the investigators to conclude a digital crime with ease.

