Smartest Way to Perform IncrediMail Mailbox Forensics
Are you about to investigate IncrediMail emails & looking for IncrediMail mailbox forensics? Undergoing cumbersome time to find the appropriate solution for the same? Do not worry! Read the complete blog and get the analysis of your emails from IncrediMail in no time!
IncrediMail is a desktop-based email client, which is no longer in service from March 20, 2020. As a result, users are not able to access their IncrediMail data after the mentioned date. However, there comes an instance wherein investigating officers may get IMM files of IncrediMail from the crime scene. Now, this can be a piece of solid evidence for investigation purposes. However, the challenging question is how is it possible to access and examine data from IMM files. The answer to this mind-scratching question is there in the upcoming section of the blog.
So folks, read on the blog till the end to instantly perform IncrediMail mailbox forensics!
How IncrediMail Saves Email Data?
IncrediMail stores email messages in the IMM file format. To be precise, it saves raw emails and not the attachments. The index information of the IMM files gets saved into the IMH file i.e., the header file which includes details about the sender, receiver, etc. There is an attachment directory which consists of all the email attachments such as pictures, documents, etc.
The default database file of IncrediMail is being stored in “C:\Users\%username%\Appdata\Local\IM\Identities” folder. The emails of every folder get saved under “Identities\{longstring}\Message Store” folder. In this, messagestore.db file will be available that stores the application metadata (messages) with the relational data model. IncrediMail uses SQLite3 in order to save and manage the database.
Upon checking the SQLite database, we can observe that other than messagestore.db file, there are other directories, which the system creates. While these folders store the actual data, the .db file saves pointers to the data folders for quick access.
IncrediMail Mailbox Forensics – View Email Header
In order to view the header of the IncrediMail email, simply follow the steps mentioned below.
- Launch IncrediMail in your system, then right-click the email message and select Properties option.
- In the upcoming screen, go to the Details tab to view the email header for the chosen email message.
- Under this tab, one can view the different attributes of the header such as Subject, From, To, MIME-Version, X-Priority, etc.
100% Proven Method to Conduct IncrediMail Mailbox Forensics
It is quite challenging to install and examine the proprietary email application to examine the email files. In the case of IncrediMail, forensic experts have to install the email client first to view the data from the IMM files. However, due to time constraints and various other concerning factors, it is best suggested to use the MailXaminerEmail Examiner Software software.
It is an authentic and reliable Email Forensics Tool that provides a deep insight for the suspected email messages. The software is designed to support 20+ email clients, including the IncrediMail IMM file. It is loaded with countless advanced features which makes the tool proficient in comparison to other emails forensic software.
Here’s How to Perform IncrediMail Mailbox Forensics Using Top-Notch Software
The following mentioned steps help the investigator to precisely examine the IMM files with the help of a high quality email investigation software.
So, let’s understand & begin the step-by-step process!
Step-1. Click on Add New Evidence to upload the email data file in which a dialog box will appear to create the case. After the creation of the case, select the IMM file from Add Evidence. Browse the file from the folder and click Add to proceed further.
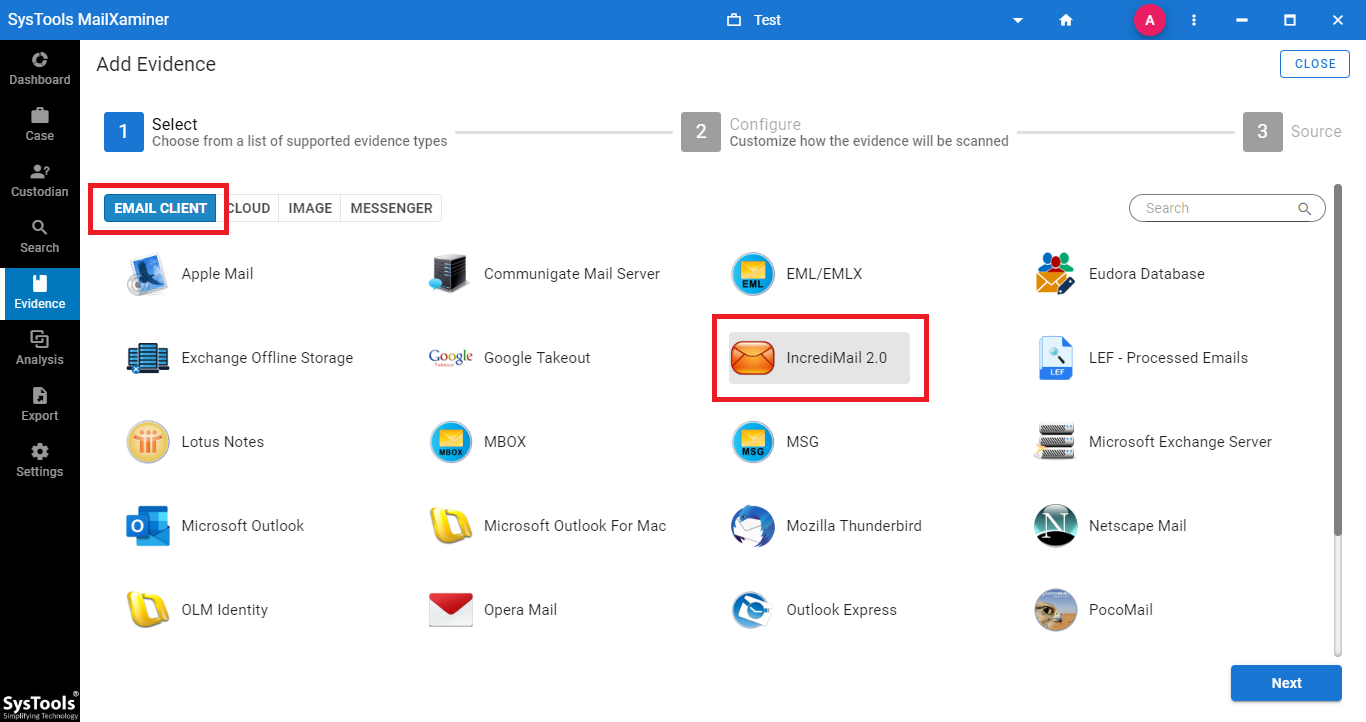
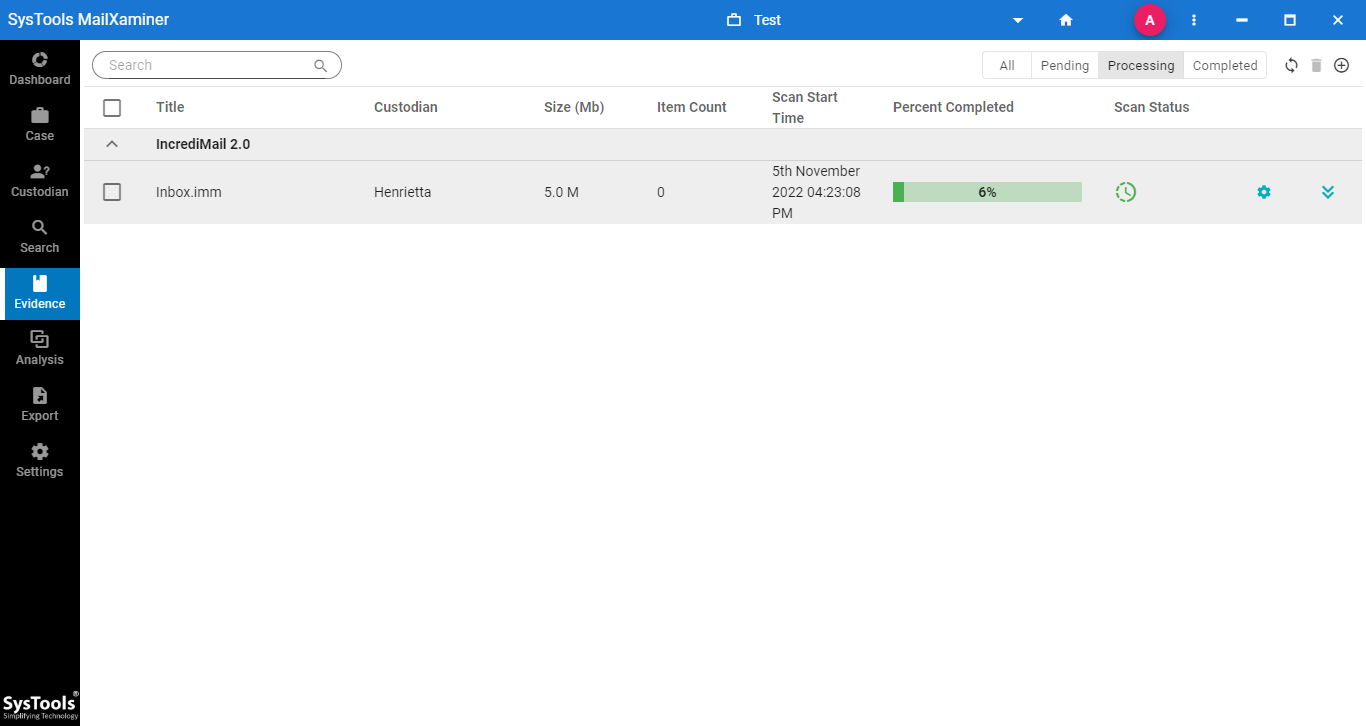
Step-2. After uploading the file on the software to perform IncrediMail mailbox forensics, the software will scan the file which might take some time based on the file size.
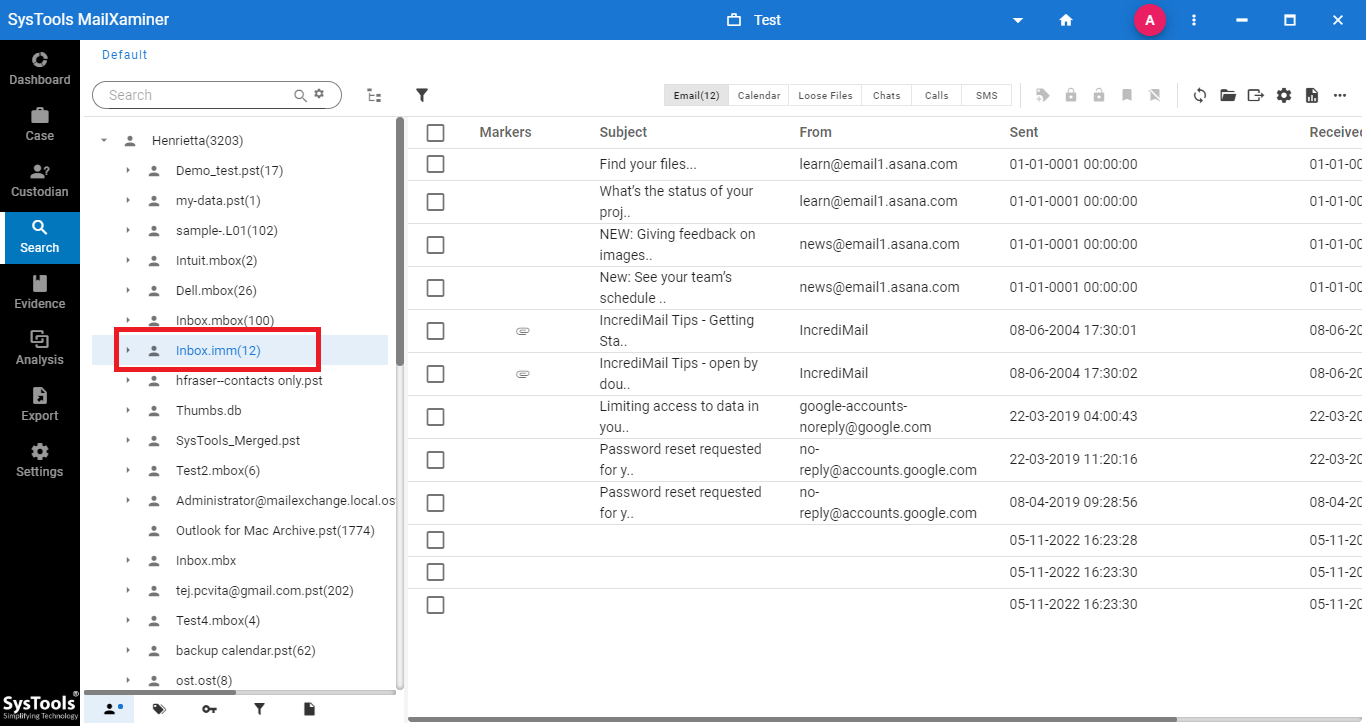
Step-3. In the Search tab, the software will provide a preview of all the files and folders as shown in the below image.
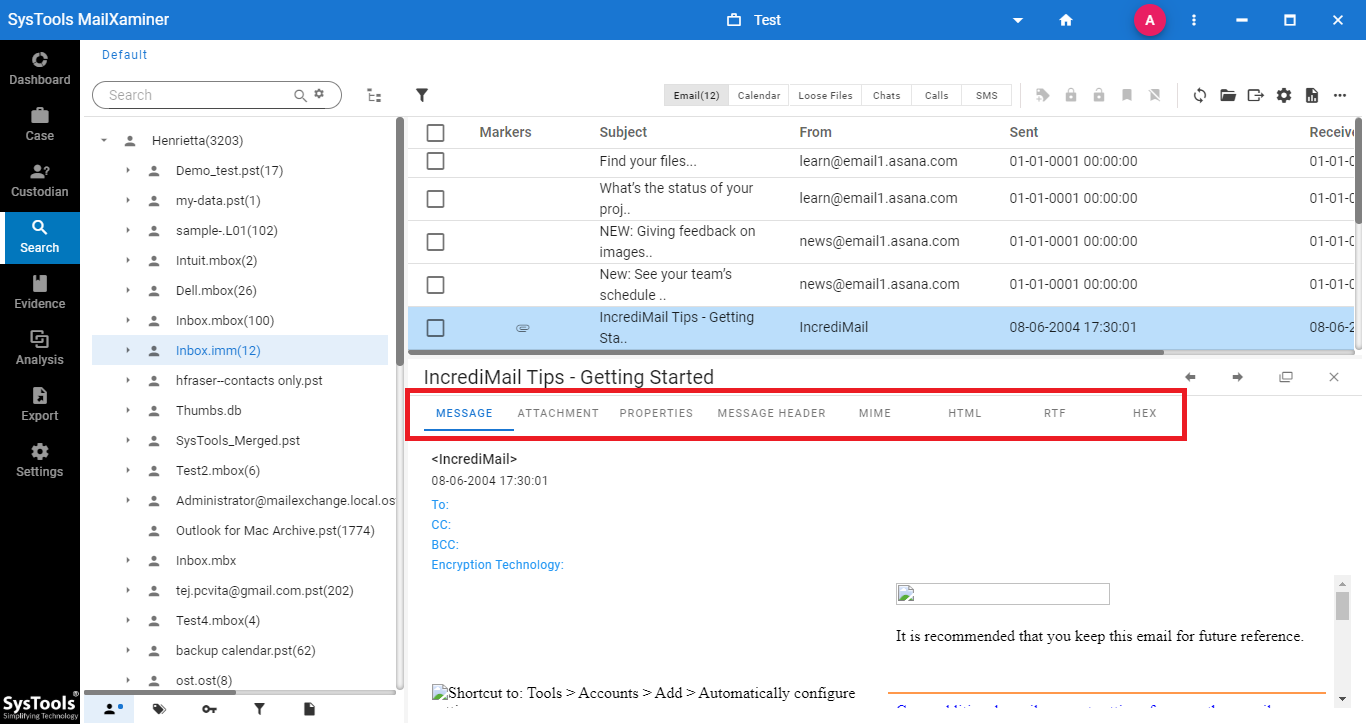
Step-4. In order to examine the emails diligently, simply select the suspected email message and a new wizard pops up. With this, one can make use of 7+ preview modes such as Mail, HEX, Properties, Message Header, etc. Each view option provides a broader picture showcasing the different attributes of the email message.
Step-5. After performing Incredimail mailbox forensics the investigator can export the emails into different file formats. Simply, right-click the email and choose the Export option.
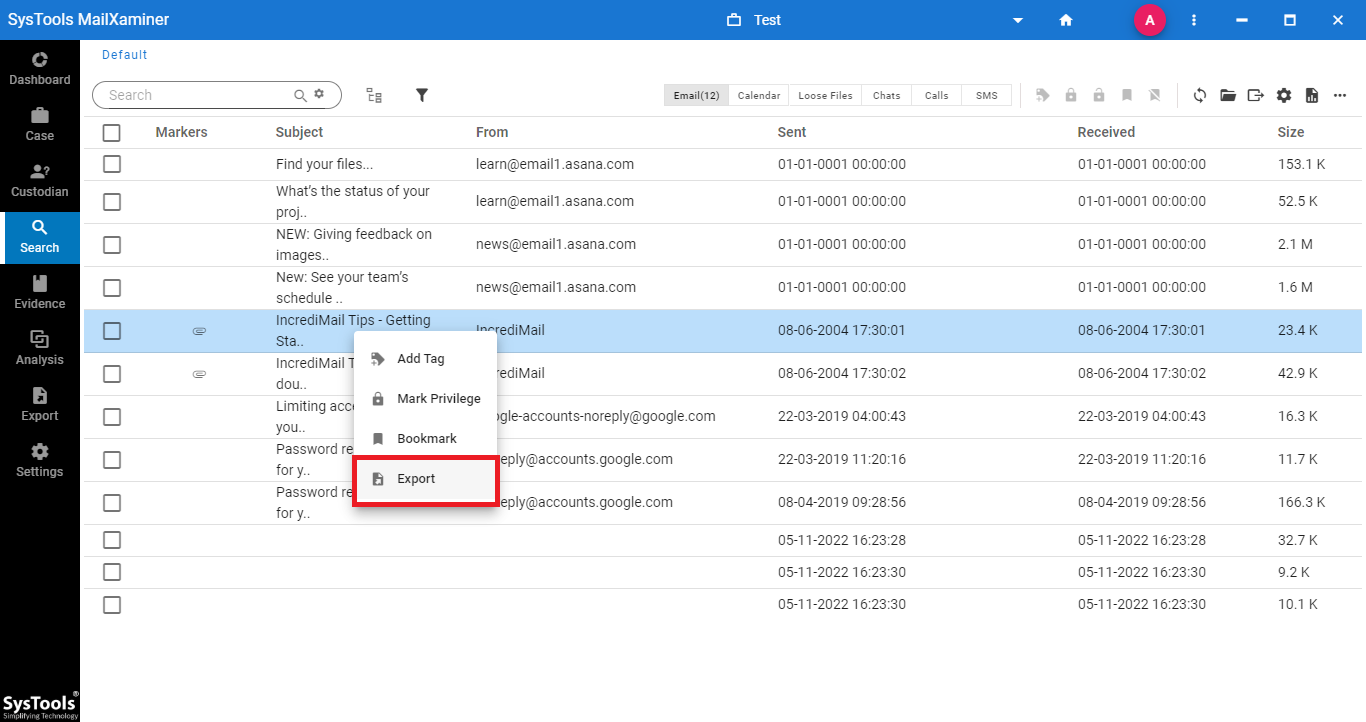
Step-6. From the Export Options window, investigators can avail the desired export file format such as EML, HTML, PDF, MSG, etc. as per their requirement.
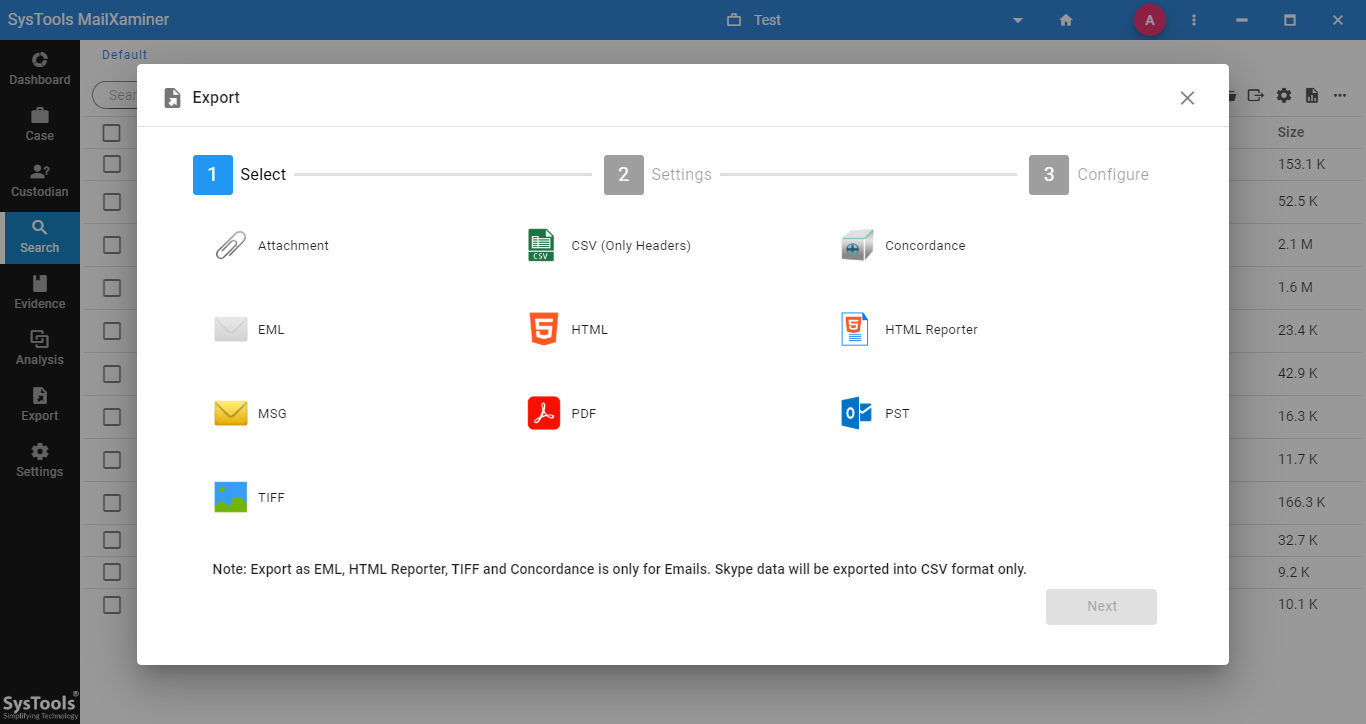
That’s it! Isn’t the software worthwhile to analyze IncrediMail files?
The End Note
In order to perform IncrediMail mailbox forensics, users need to examine IMM files, which is the default file format of IncrediMail. Hence, the investigating officers make use of reliable and proven professional utility to examine the IncrediMail emails in a hassle-free way.
This is because it is not feasible every time to install the default email application to analyze the gathered email data file from the cybercrime location. Using this remarkable email forensic software, there is no worry of examining email files. As it is capable enough to analyze 20+ email files, including the IncrediMail IMM file without the need for installing any external application.

