Find Credit Card Numbers in Files Tips for Cyber Crime Analysts
During cybercrime investigations, detectives often have to find credit card numbers in files present across multiple digital sources. Moreover, as credit cards can provide lots of insights into the transactions done by cybercriminals, finding them is a key process that can’t be delayed. However, the real challenge in most cases is that these card numbers are not readily available to the investigator.
If cybercriminals are smart, they might use codewords instead of actual names to misguide forensic analysts. As information becomes readily available, even cybercriminals can now use complex file hierarchies and encryption tactics to hide the location of files. That’s why we here have the best available utility for extracting the card numbers with minimal time and effort.
Even with the tool at hand, detectives must have a strategy of their own to prioritize certain data types over others. This is due to the sheer volume of data involved in a cyber investigation. So let’s discuss the files that are most likely to contain the credit card numbers.
Where to Find Credit Card Numbers in Files that are Stolen
The most likely file formats, folders, and software that can contain hidden credit card numbers are as follows:
Text-Based Files: After a data leak or hacking on a secure database, adversaries often put the stolen data in CSV or similar file formats. These files are not used by attackers themselves but rather put on sale on the dark web. In such a case, investigators might find a large CSV or XLSX file as an email attachment.
Email Clients: Cybercriminals more often than not work in teams. Like any other team, they also conduct communication and share information after a digital theft. For that, the most likely tools are desktop-based email clients. So if the electronic devices gathered during an investigation have preinstalled email clients, forensic teams must conduct a thorough investigation of those as well.
Cloud Storage: Investigators might find credit card numbers in files present on the cloud platform (or web-based email clients) linked to the criminal. New and inexperienced fraudsters might use these to keep the data scraped by them.
Digital Images: A cybercrime is less likely to originate from a local source. Especially one that involves a data leak of plastic money. Moreover, sending hardware across state or national borders is time-consuming. Therefore, to speed up the investigation, the cyber police may send a digital image of the device to the forensic analyst for evidence accumulation.
Virtual Photos: Sometimes, instead of direct credit card information, investigators might find images of the items instead. These include PDFs as well.
Compressed Files: Due to the large volume of data involved, criminals often compress the original data in zip format. Investigators should check these files on the criminal’s system to see if they contain the credit card names or numbers.
Best Way to Find Credit Card Numbers by Name In Files
MailXaminer is the go-to utility for email forensic scenarios. It is especially designed to aid cybercrime investigators during the evidence-gathering phase of their case. With an ever-increasing rate of cyber fraud, law enforcement agencies need all the help they can.
That’s why countless agencies have put their trust in using the services of the tool to speed up their ability to prosecute criminals. With dedicated filters for various scenarios, like one where detectives need to find credit card numbers in files, it covers all the bases with minimal effort.
Even with so many features, the tool manages to maintain a user-friendly interface that requires no prior training. This is done so that the tool can be deployed and used directly without much effort.
Case Creation Stage of the Automated Utility for Credit Card Lookup
Step-1. Launch the tool, check the top right corner for a running condition (green tick), and type in the default ID and password (both: administrator). This can be changed post-login. Make sure that the tool is activated prior to its use.

Step-2. Hit “CREATE CASE”, fill in the required fields, and press Save. A new case is added. Click on the title to proceed. Press “ADD NEW EVIDENCE.” From the series of options, pick the most appropriate one as per your choice.
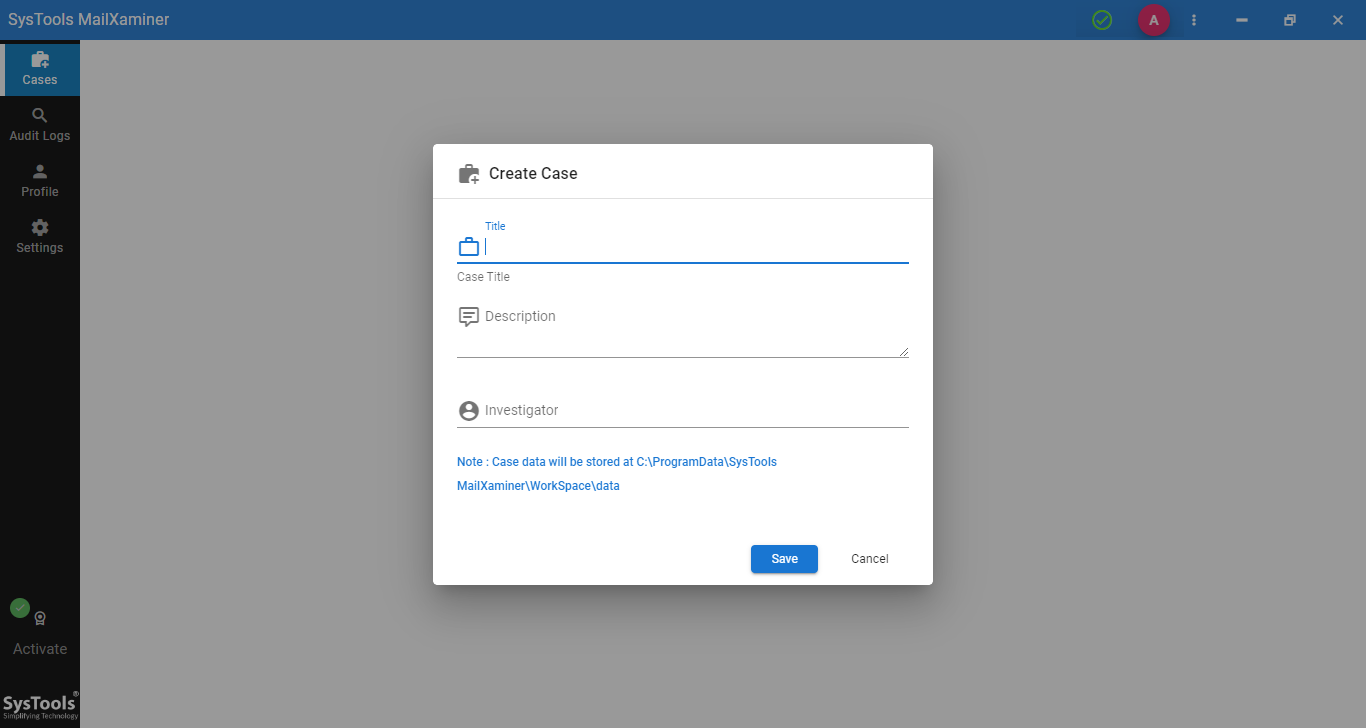
Step-3. Next, apply the Settings (for credit card info “Upload Attachments while Scanning”, “OCR,” and “Image Analysis” are recommended). Users also have the option to remove encryption from files. Once all settings are complete, click Next.
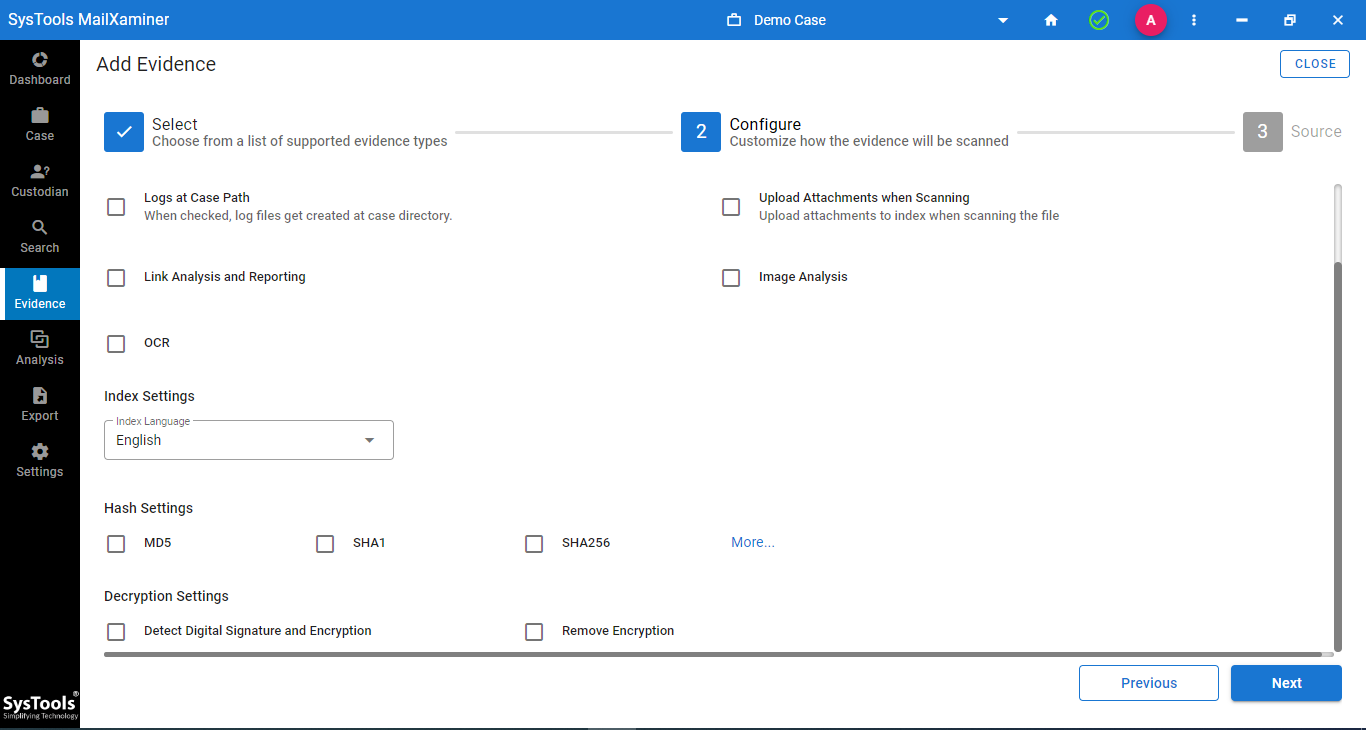
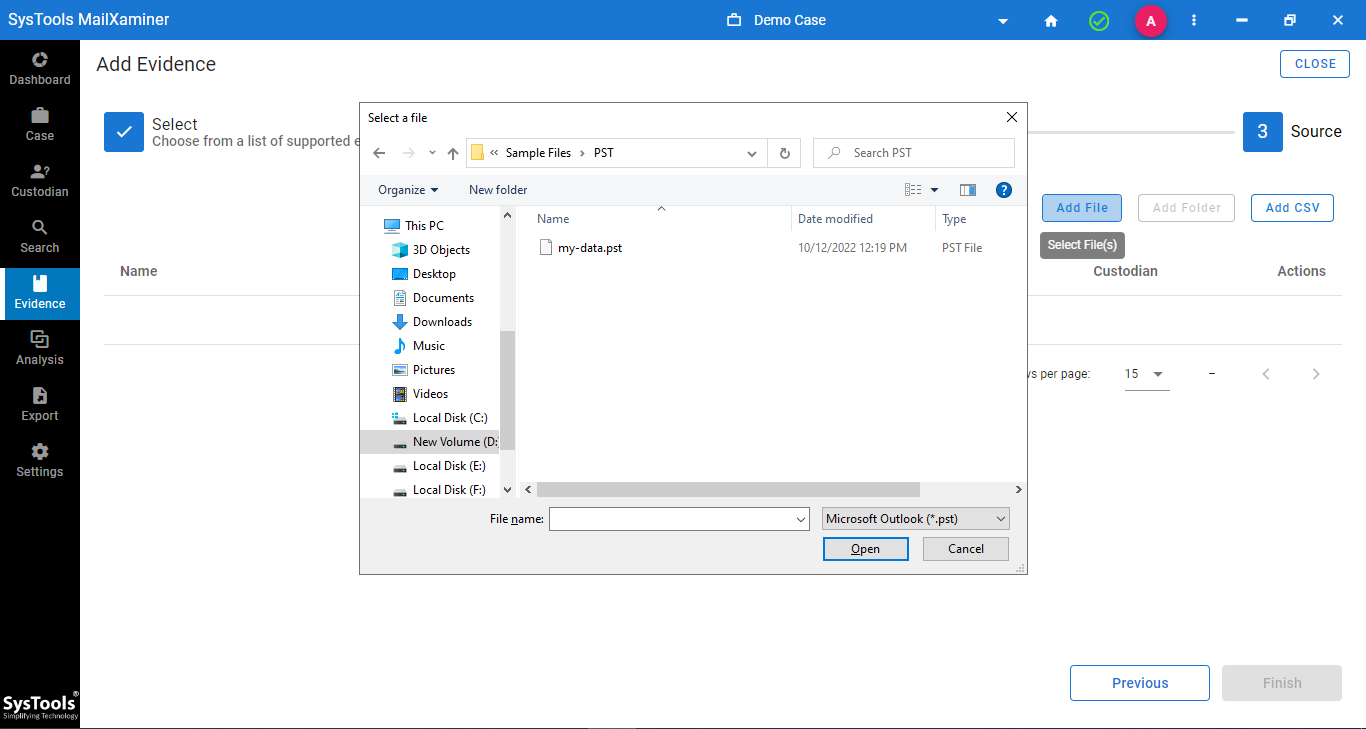
Step-4. Now to find credit card numbers in files, add the source file that contains the stolen credit card data and click Finish.
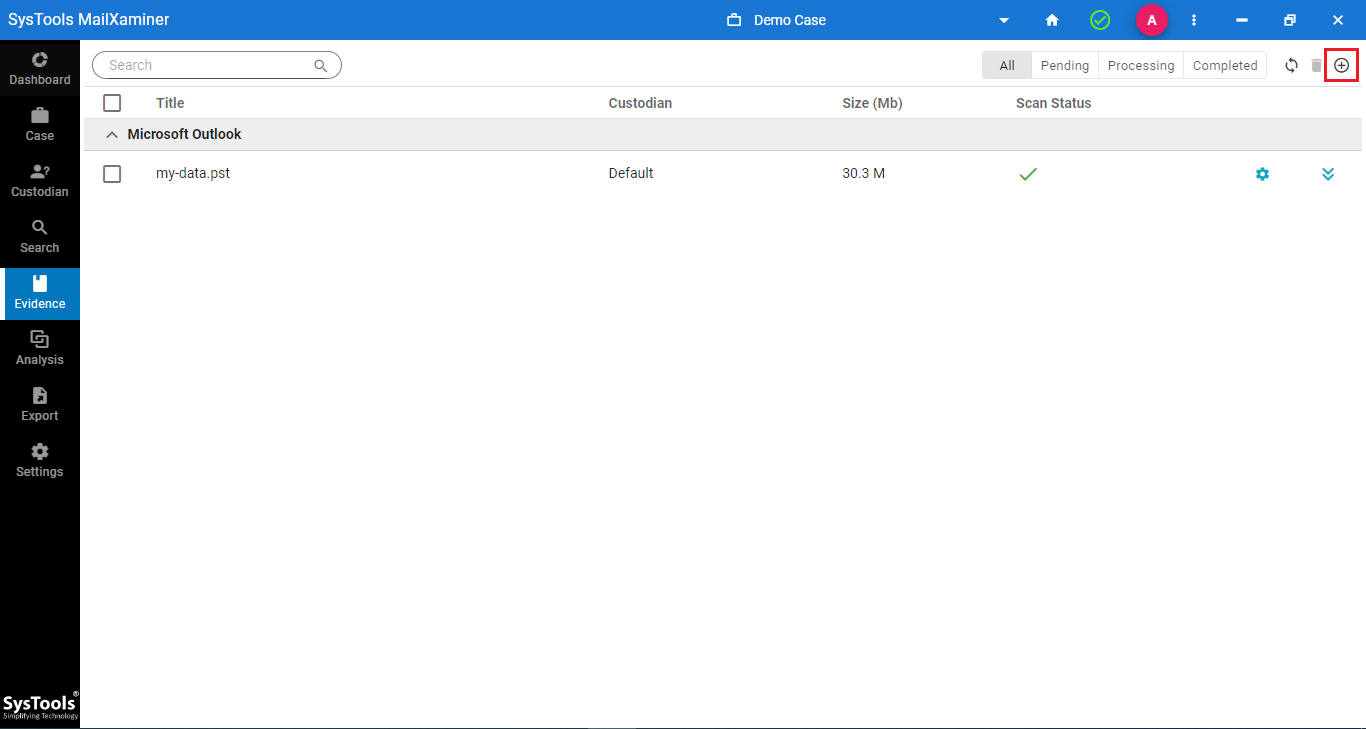
Step-5. The real-time evidence scanning status can be seen on the Pending, Processing, or Completed tab. (New evidence of varying data types can be added during investigation using the plus ”+” icon).
Searching and Filtering Operations to be Performed Via the Tool
Step-1. Go to the search tab to preview the data set (multiple viewing options exist for investigators to make sense of their data). Click on the highlighted icon to look at the folder hierarchy.
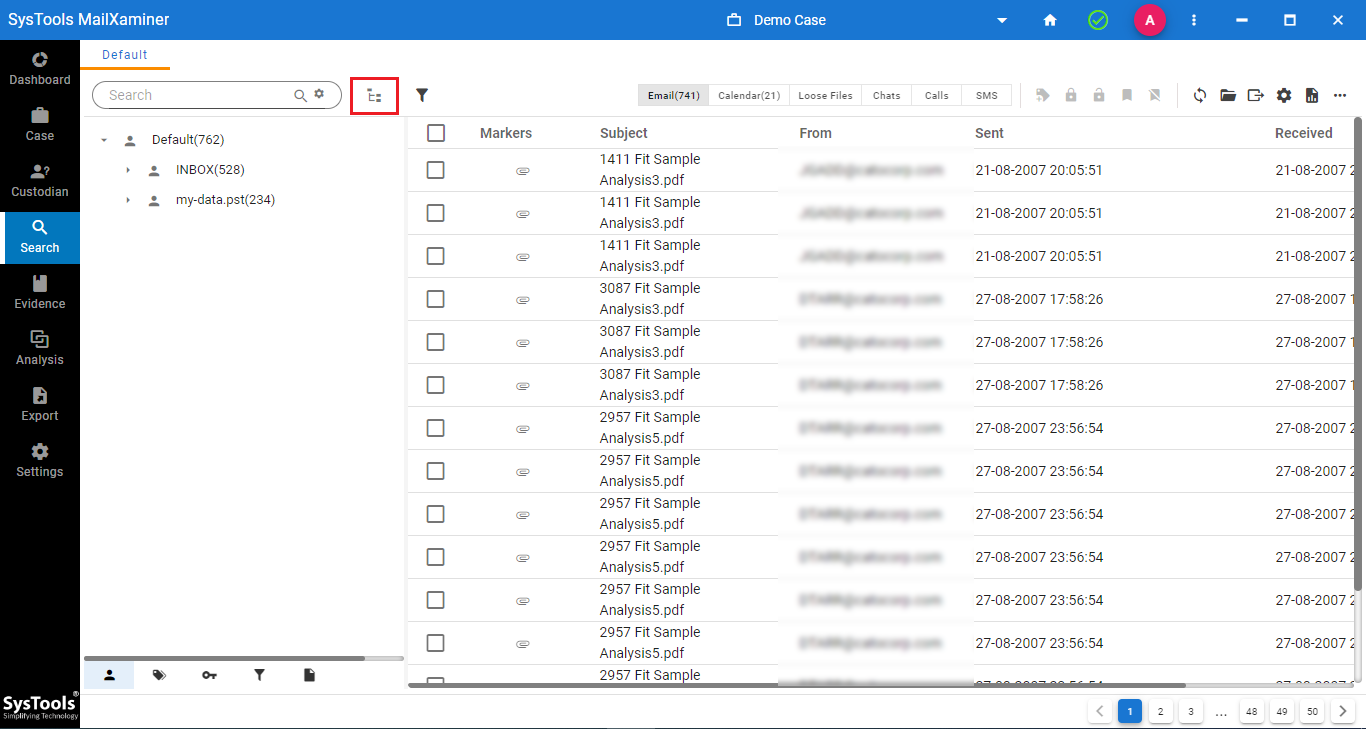
Step-2. In the bottom left corner, there exists a set of filters to modify the data set.
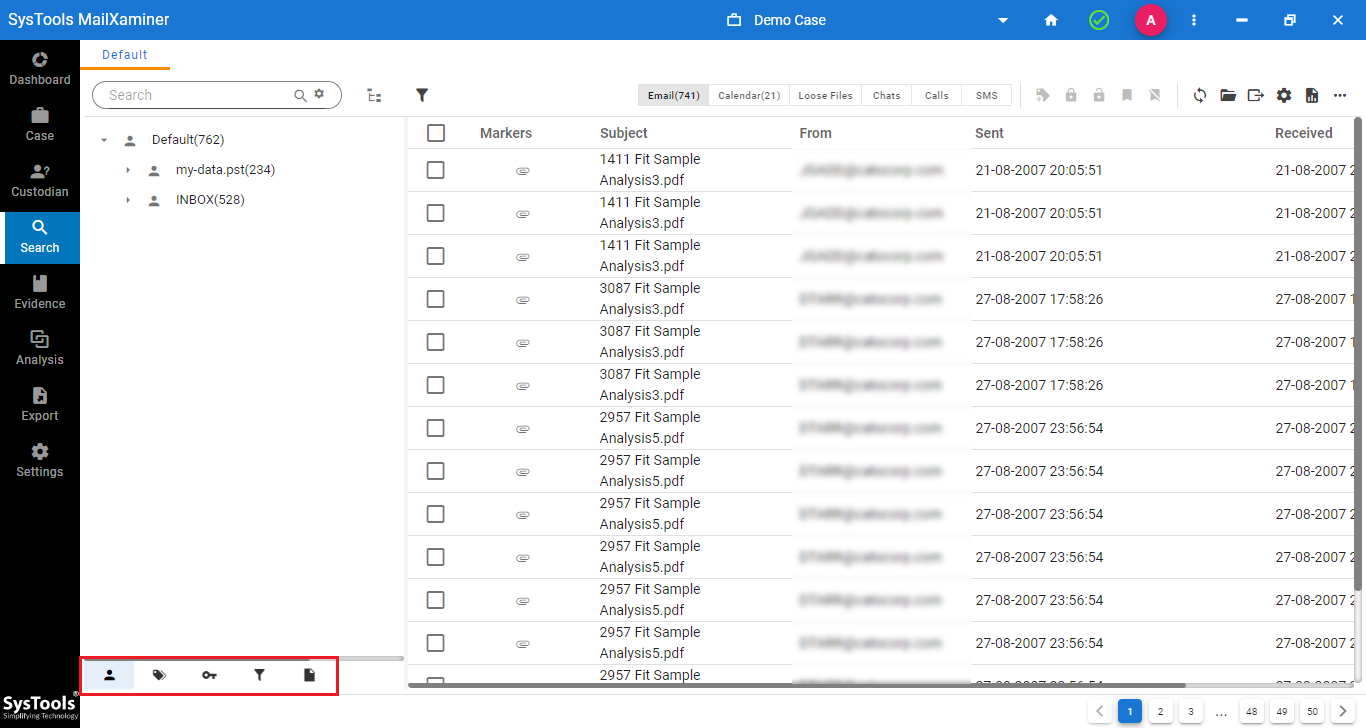
- First is the Tags tab, which contains pre-made tags for the type of evidence. In your case, you need to select the “ID Credit Card” option.
- The key icon provides the option to add custom keywords. Investigators can use it to add specific jargon (either manually or via a CSV file) that is used by the criminals.
- The standard filter is the basic way to use predefined categories that also contain settings to separate out credit cards.
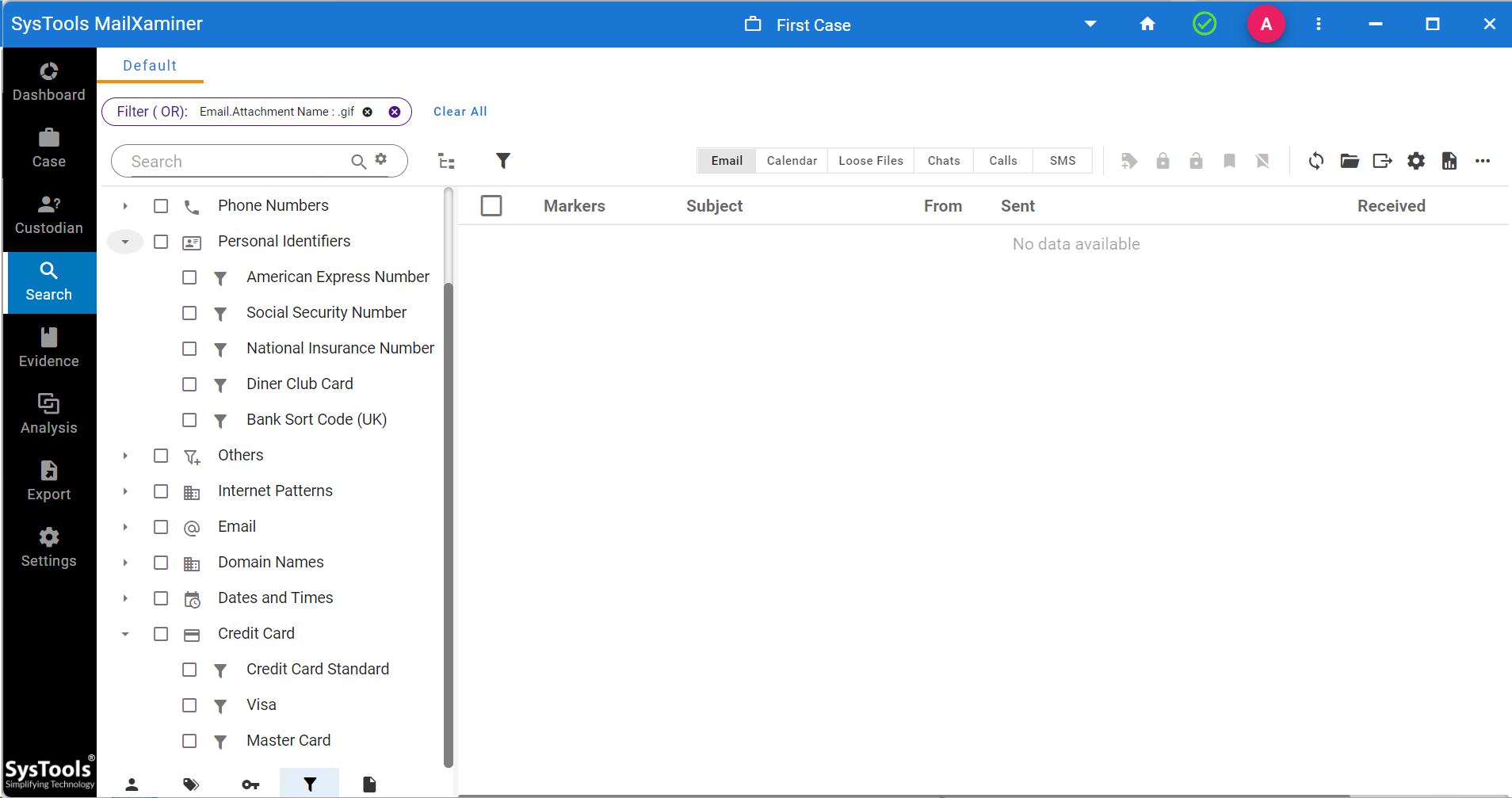
- At last, there is also a media filter for looking into images, compressed files, PDFs, Text files, etc.
Step-3. Once the filtering is complete, there are a variety of ways to search for the specific data. The options include:
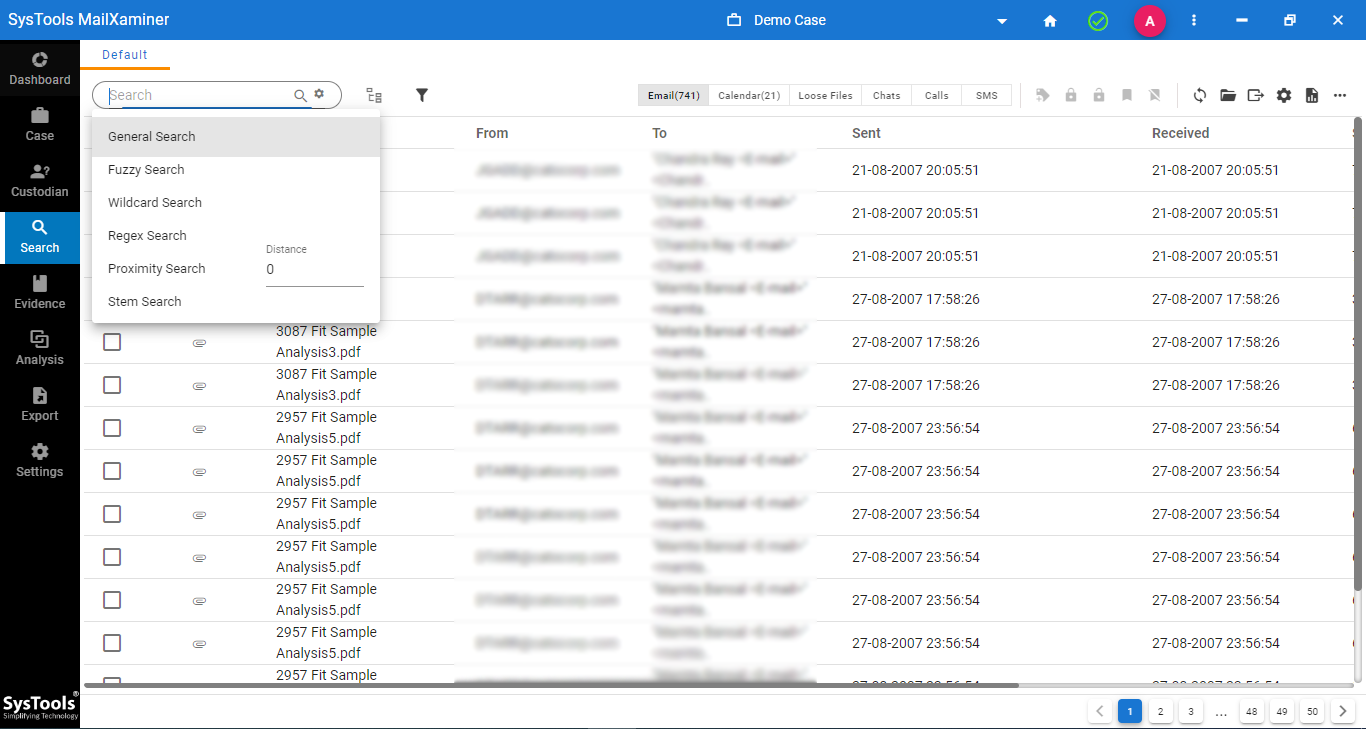
- General Search: If investigators have limited leads, they can start with the basic search option.
- Fuzzy Search: It is typically more effective for textual data than numerical values. Nevertheless, detectives can use it to identify the banks involved in the fraud.
- Wildcard Search: A wildcard search replaces unknown quantities with either the asterisk “*” for multiple characters or “?” for a single character. However, its effectiveness for searching credit card numbers is questionable at best.
- Regex Search: This is the best option for investigators who want to find credit card numbers in files.
- Proximity Search: For cases involving credit card theft, proximity search is not the best option. It is more useful for data that contains words.
- Stem Search: In some specific cases, this searching parameter may help investigators classify the victims.
Use Viewing Options to Find Credit Card Numbers in Files
Here we have the instructions to get insights out of the selected data and how the various features of the tool can help in streamlining this process.
Step-1. If the investigator is not satisfied with the current search parameter, they can create a new search option.
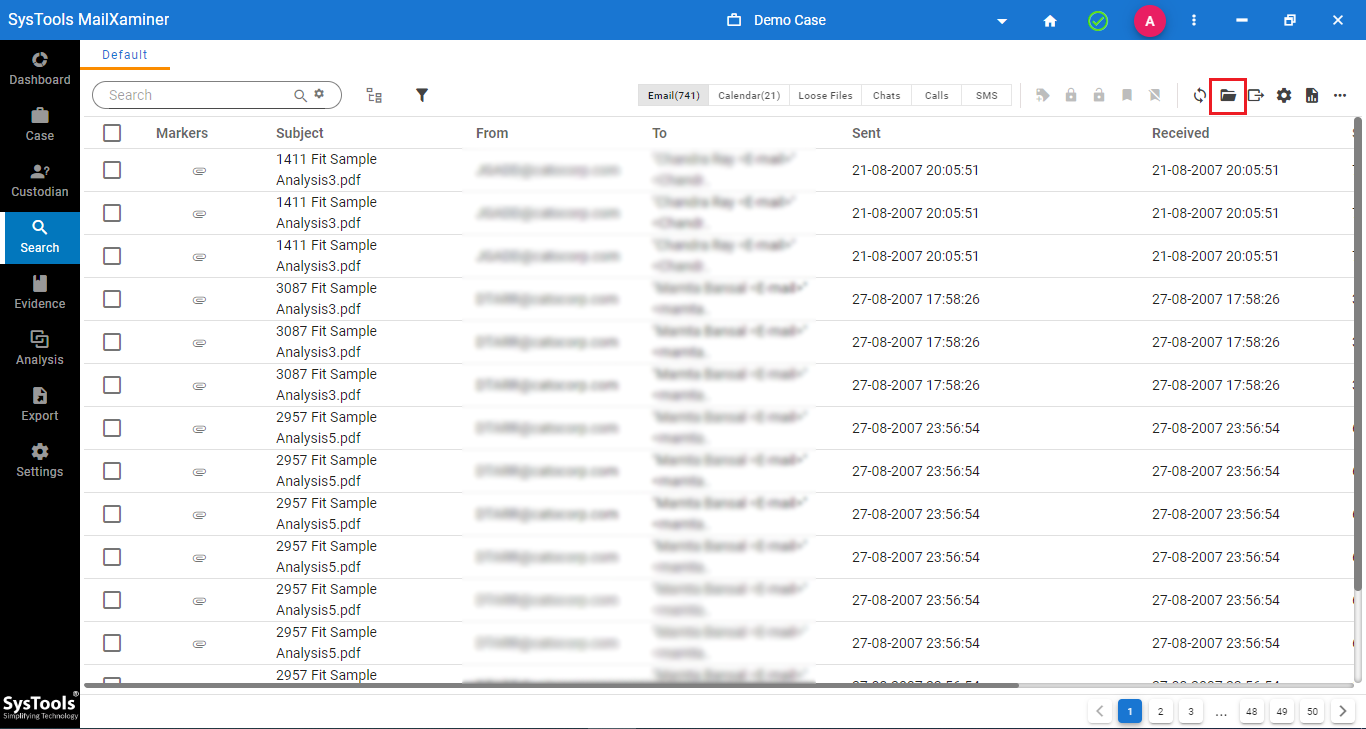
Step-2. Click on folder icon >> In the window, hit “+” >> Type name, description >> Press Ok
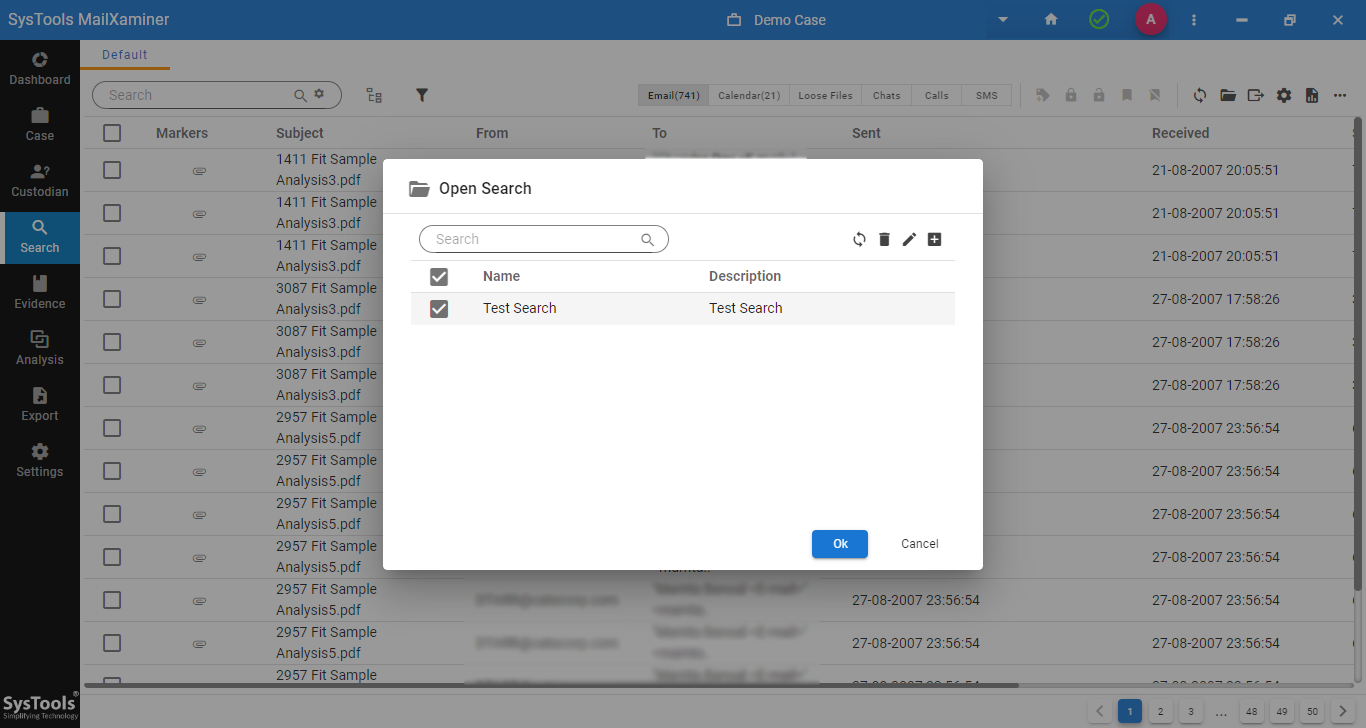
Step-3. If the search results align with the requirements, export them in the desired manner (selected items only, complete folder export, export only the search results).
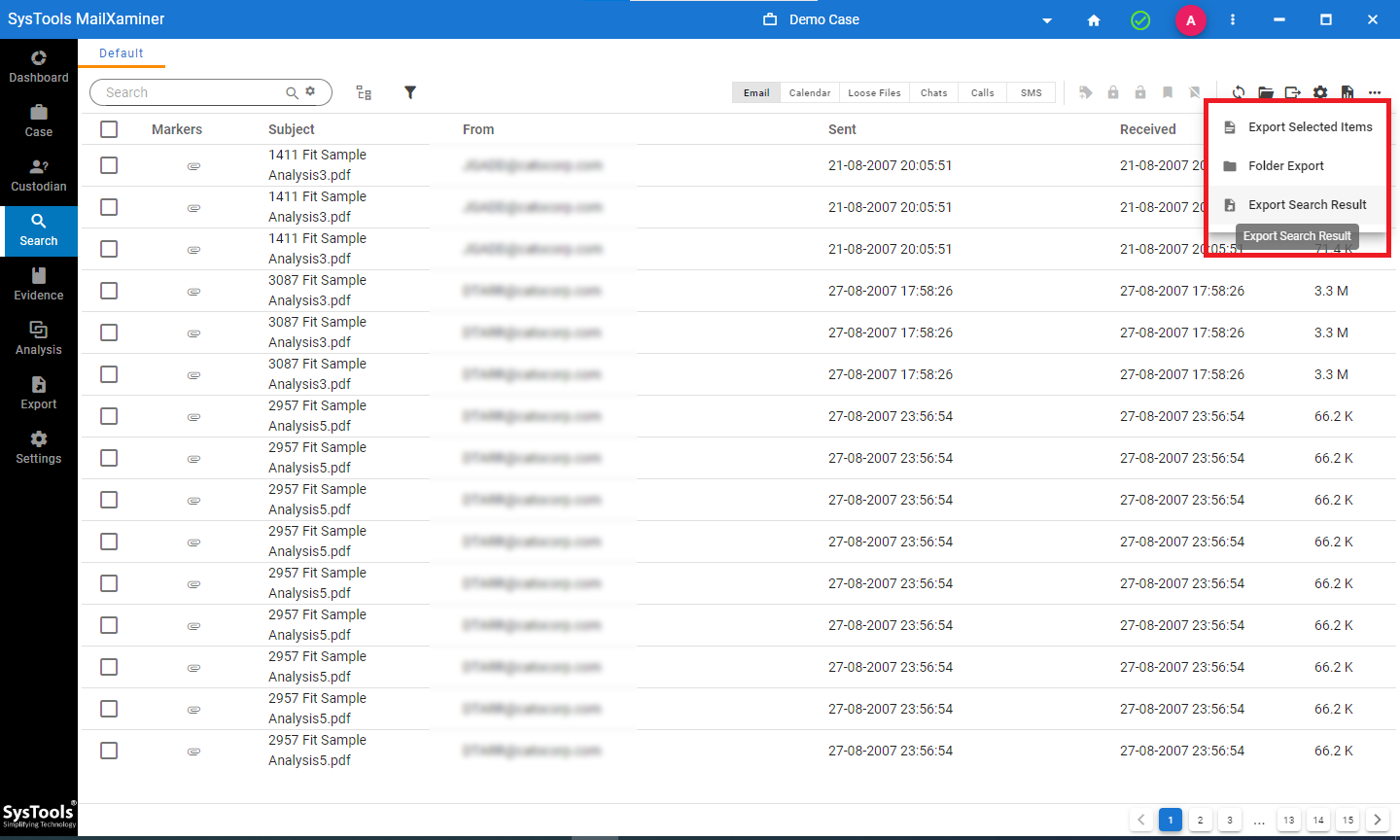
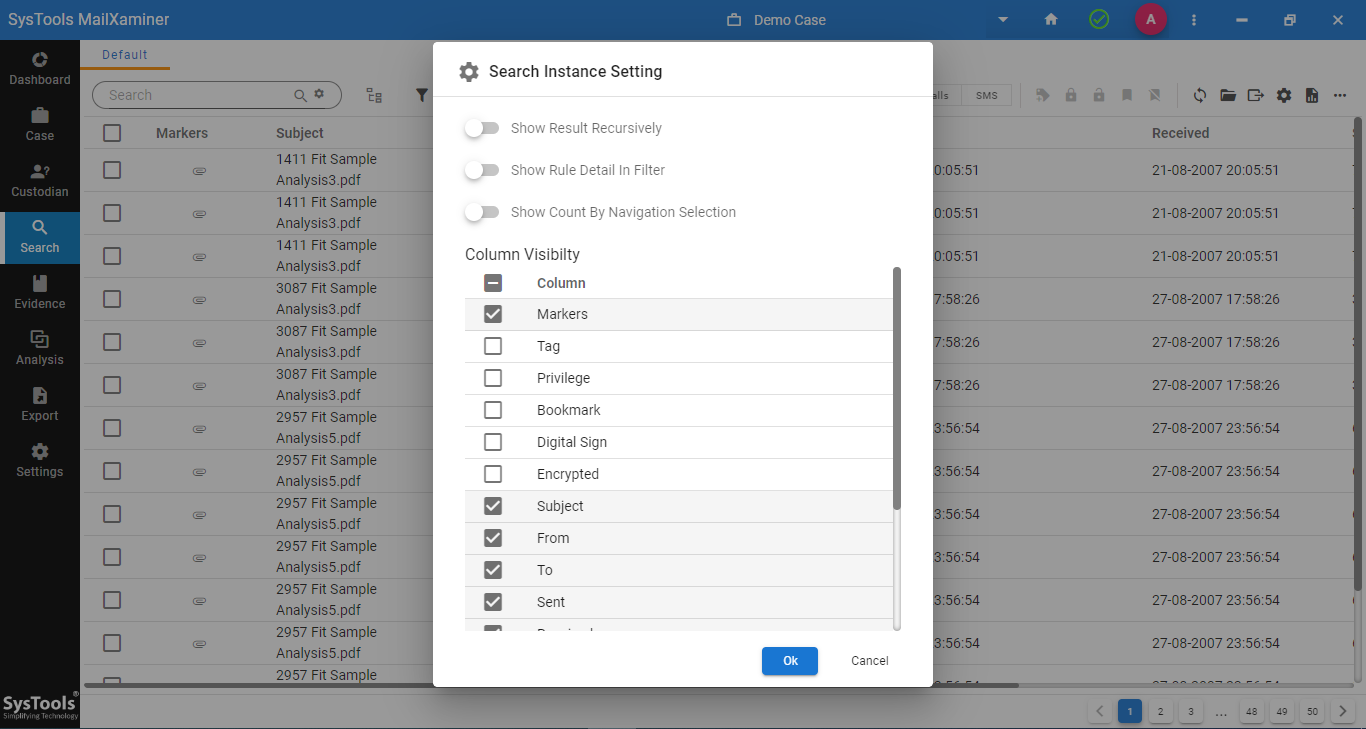
Step-4. From the gear icon, the detective can fine-tune their result to see only the required parameters.
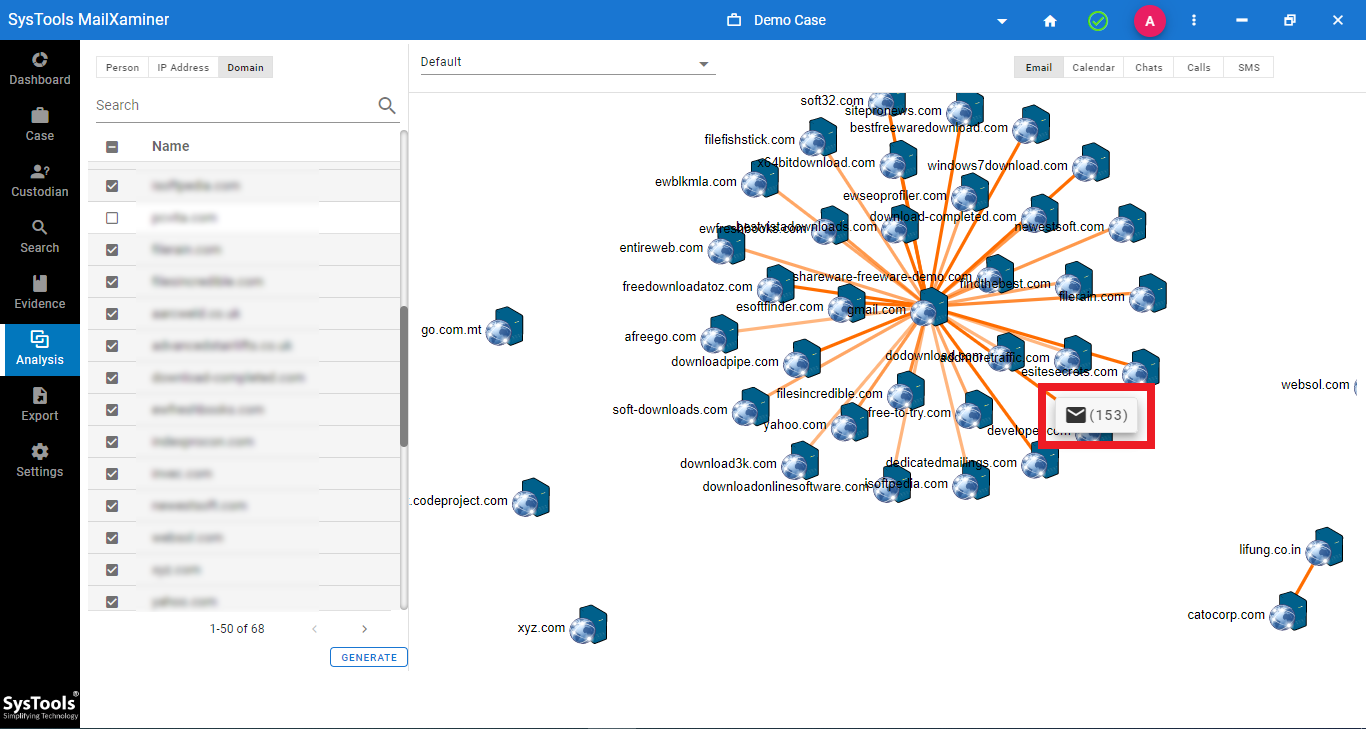
Step-5. In the analysis section, investigators get a visual indication of the connection that exists between the suspected entities. Moreover, there are three separate subdivisions within the link analysis itself.
- Person
- IP
- Domain
Step-5. If you move your cursor and click on the orange bar, you get the number of emails exchanged between the two endpoints. This can be helpful in determining who has access to the stolen credit card details.
Step-6. Then there is a dashboard screen, which paints an even clearer picture of the data through a series of graphs and charts.
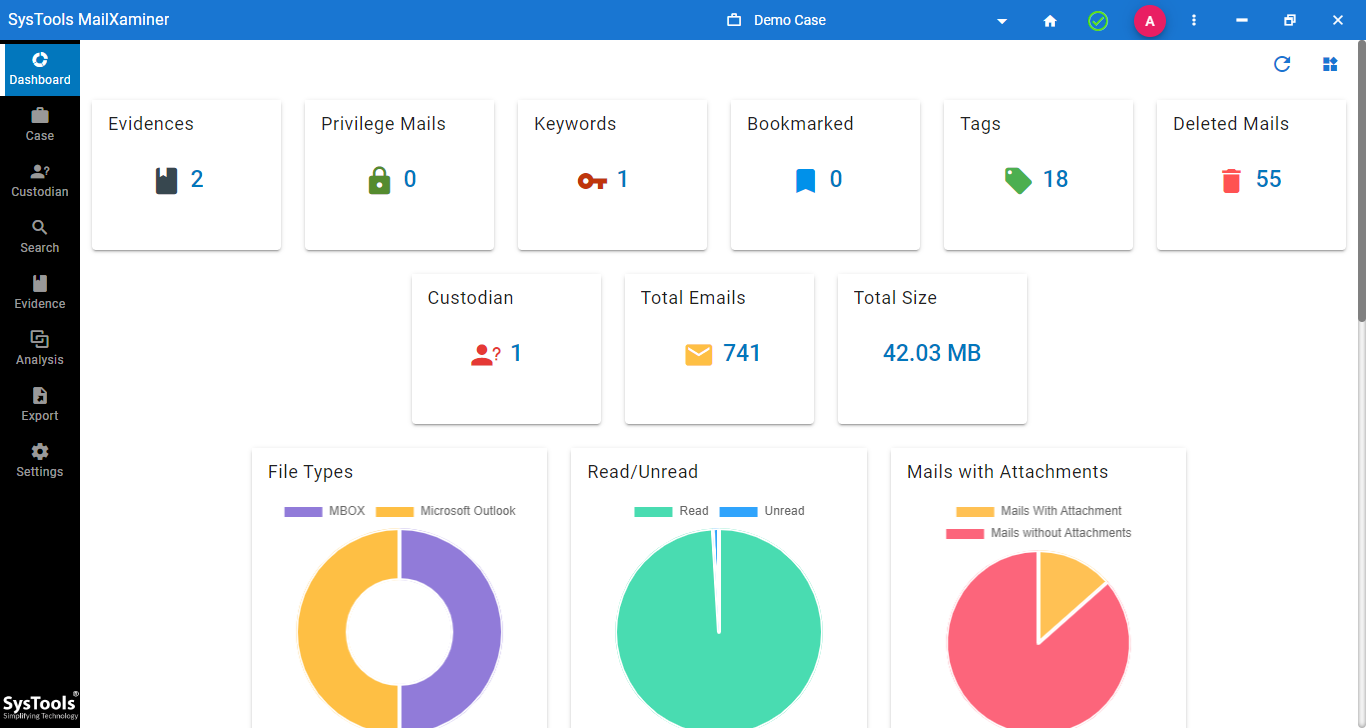
Step-7. These include a complete overview of all the key parameters searched, pie charts for emails, and a histogram for a timeline of the entire event.
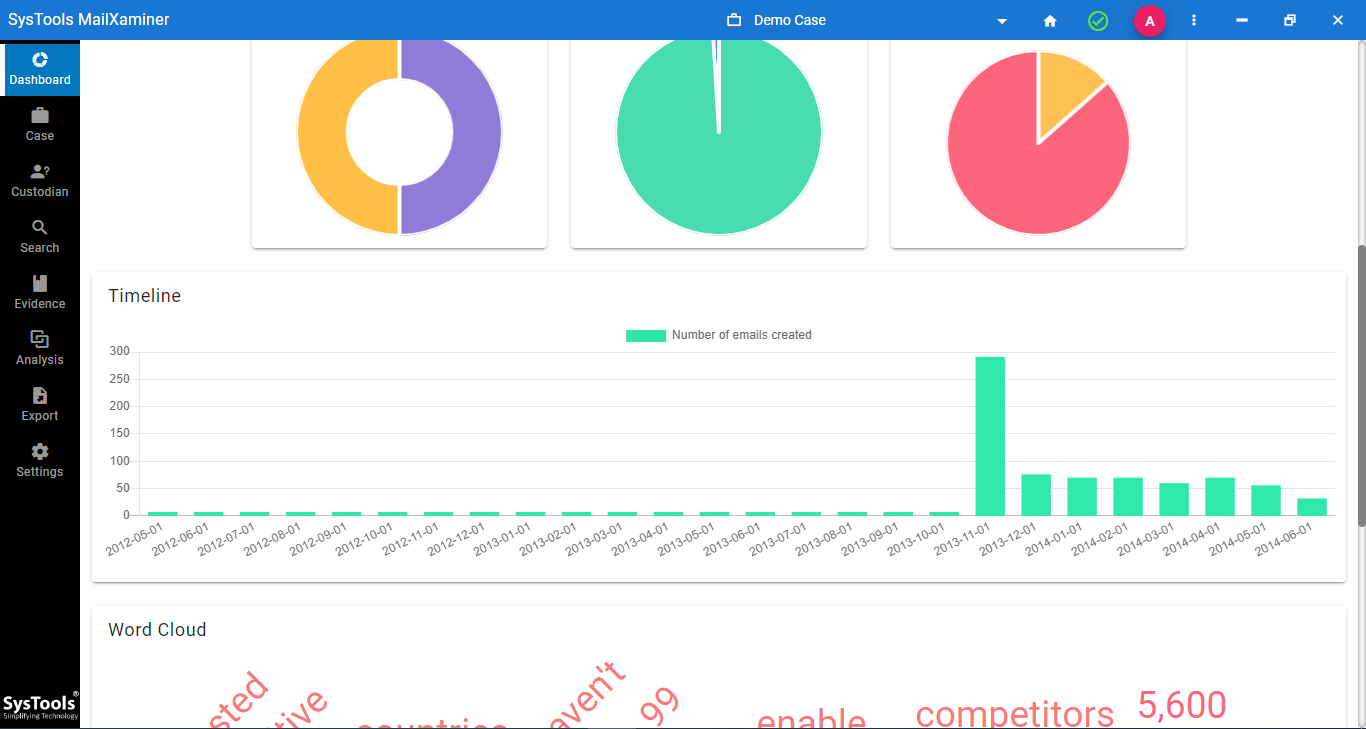
Step-8. Investigators can get the gist of the conversation by looking at the word cloud. It contains the most commonly used terms in the conversation between the suspects.
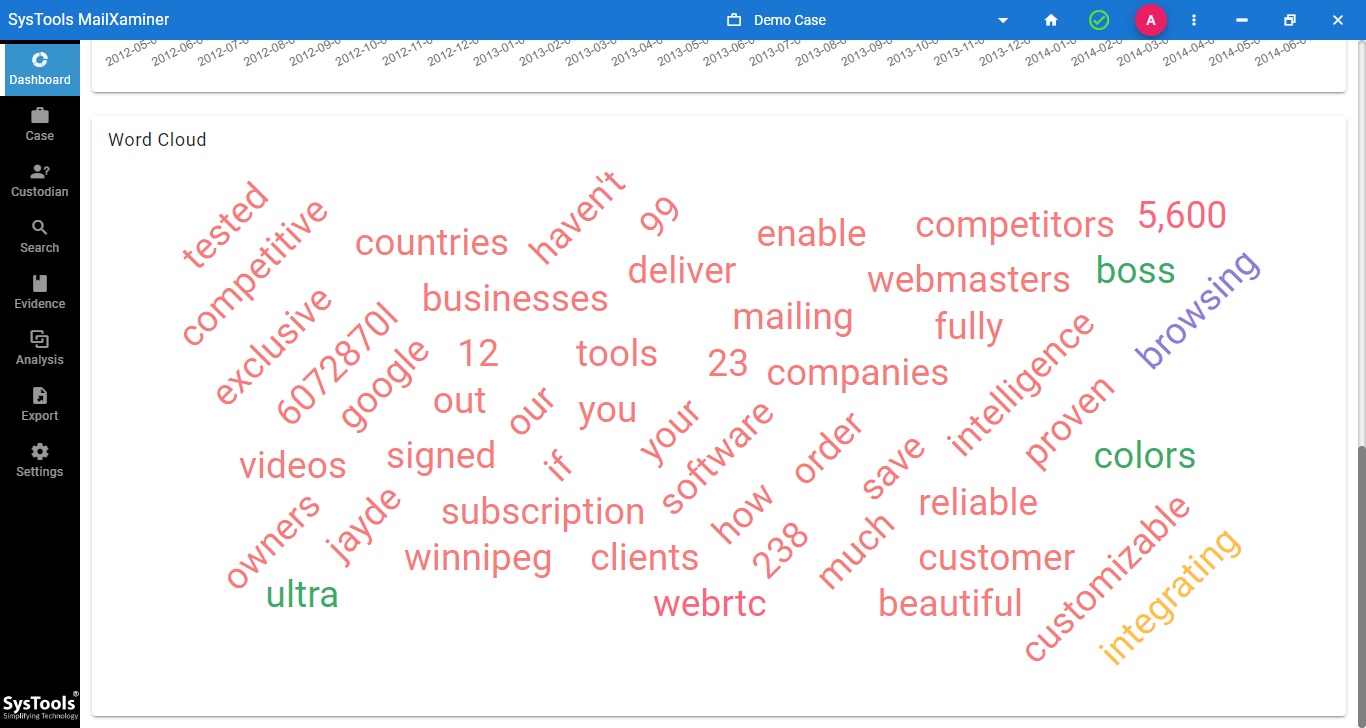
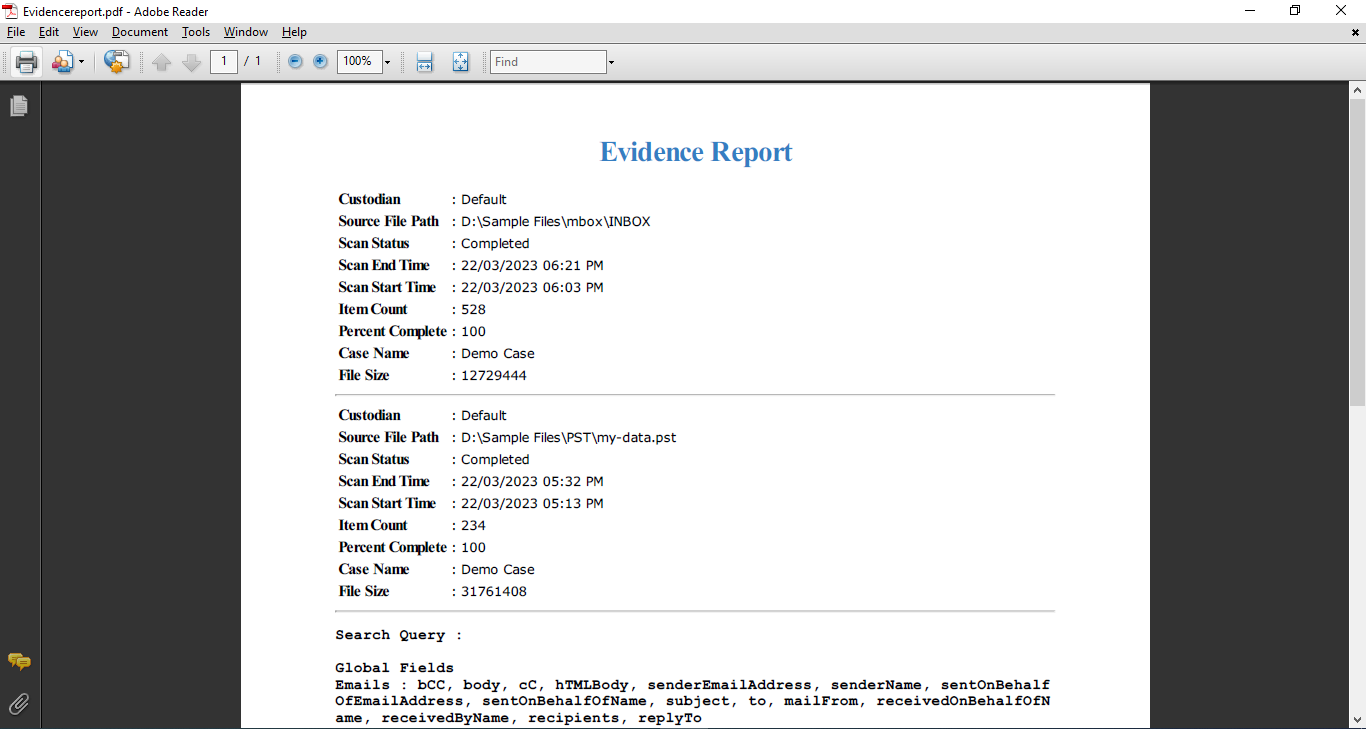
Step-9. Configure all the export options as per your understanding and generate an evidence report as well.
Why the Tool is Renowned in the Field of Digital Forensic Investigation
The following list of useful features explains why the tool has a rich legacy of successfully aiding law enforcement agencies in tracking down perpetrators of digital crime:
- Support for more than 80 different email clients and file types as evidence.
- Inbuilt OCR scanner to convert physical files to electronically readable items.
- A collaborative environment for teams to combine their findings into a single report.
- Get smart features like Word Cloud combined with graphical analysis.
- Separate filter to find credit card numbers in files uploaded within the tool.
- Use a variety of search options to trim down the data to a more usable size.
- Analyze data in bulk and get real-time tracking on the status of the operations.
- Link analysis to map the domains and IP addresses involved in the crime.
For an in-depth discussion of the software, feel free to contact the support staff. They are always ready to answer all your queries regarding the tool’s functionality.
Conclusion
In this guide on how to find credit card numbers in files, we discuss the best possible approach for digital forensic investigators. Using the advanced utility during evidence gathering, law enforcement agencies can save critical time and reduce their effort. This allows them to shift their focus to prosecuting criminals for their crimes.
Frequently Asked Questions
Q. How do criminals illegally obtain credit card data?
Despite having so many security checks, losing credit card information is not rare. So let’s look at some of the most common strategies that criminals employ to steal the data.
- Phishing and email fraud
- Skimming and card-cloning
- Data leaks and cyberattacks
Q. What methods are employed to identify credit card numbers in digital files or folders?
- Using a regular expression to find the 16-digit credit card numbers.
- Converting images to an electronically readable format via OCR.
- Tracking emails between criminals to pinpoint the source of data leakage.
Q. When does an investigation into credit card theft begin?
- Report filed via the bank, individuals, or other concerned authority
- Sudden uptick in the frequency of transactions for no apparent reason.
- Fraud prevention is a reason to proactively monitor the transactions done via plastic money.
Q. Where do criminals store the stolen credit card information?
- They might steal it and publish it on the dark web via private servers and VPNs.
- Criminals can place it on the cloud storage facilities.
- Send it to their collaborators using email.
- Place it on an external hard drive or other physical storage.
Q. Why are credit cards such vulnerable targets?
Credit cards are widely used and have relatively few security measures built into them. Furthermore, features like tap-to-pay, result in criminals finding new methods to exploit these systems.

