How to Fight CSAM From Detection to Prosecution? Explained
Child Sexual Abuse Management (CSAM) is the most crucial and challenging matter that is rising today in the fight against exploitation. It is imperative to address this issue proactively.
If we talk about how these CSAM cases are investigated, so this is becoming a global issue now. CSAM investigations can only be achieved with a high level of investigation techniques.
This is because these CSAM investigations demand precision, sensitivity, and advanced software that can effectively detect, analyze, and prosecute offenders in earlier stages.

Today technology is achieving its greatest height in every aspect. Adding technology to legal proceedings related to criminal cases like CSAM is very important. Technology can safeguard children from sexual abuse. Also, it can support those officials who work tirelessly as the front liners in these critical investigations.
The clear purpose of this guide is to inform people worldwide about globally advanced digital forensic software, MailXaminer. The software is now stepping forward from the detection of CSAM to the prosecution of CSAM. This can easily simplify detection and detect the evidence. It can ensure ethical and legal standards. With the advanced features, this software is completely allies in protecting children and bringing perpetrators to justice.
What is CSAM and Its Digital Footprints?
Child Sexual Abuse Material (CSAM) refers to any visual depiction of sexually explicit conduct involving a minor (a person under the age of 18). The term encompasses images, videos, and other material that exploit or abuse children. It can also violate their fundamental rights of safety and dignity. CSAM is a grave criminal offense and a global issue that transcends borders and requires collaborative efforts to combat it effectively.
In the digital stages, such material can be disseminated across various platforms like emails, social media, and encrypted message services. Detecting those digital footprints of CSAM is crucial for investigators. This is so because it involves analysis of email metadata of files, transmission pathways,s, and storage methods employed by perpetrators to conceal their activities.
The Role of Digital Forensics in CSAM Scanning
Digital forensics allows investigators to track the digital footprints of offenders from detection to prosecution in CSAM investigations at a very early stage. It also helps the investigating officials collect evidence to analyze various types of digital evidence. Different digital forensics investigation techniques can help CSAM investigating officers detect, preserve, analyze, and prosecute the electronic evidence.
In CSAM cases, digital forensics is crucial for the forensic recovery of evidence to uncover hidden and lost email evidence, tracing the origin of the illicit material. Effective digital forensics can enable law enforcement to build compelling cases for prosecution and ensure that perpetrators are brought to justice.
This disciplinary approach integrates computer science (technology), law enforcement, and psychology to effectively deliver justice and vulnerable are protected from CSAM.
MailXaminer- Leading a Charge in CSAM From Detection to Prosecution
MailXaminer is the software that is designed with a complete suite to investigate any digital footprints. This software utilizes sophisticated algorithms to analyze and detect CSAM across multiple digital platforms including cloud forensic investigations, hard drives, and mobile devices. MailXaminer supports examination-related content and also supports law enforcement while tackling and examining evidence.
The software has various advanced features and one of the most striking features is to efficiency of handling a variety of email formats. These email formats include Outlook, Gmail, Yahoo, etc. You can simply extract embedded images from Outlook in search of evidence. MailXaminer delivers precisely what’s needed to uncover crucial evidence in the battle against CSAM, where speed, accuracy, and confidentiality are paramount.
How MailXaminer Supports CSAM from Detection to Prosecution
In CSAM investigations, every detail counts. Investigators must sift through large volumes of email data to find key evidence that could lead to the identification of offenders, victims, and networks. This is where MailXaminer’s advanced features become indispensable. Below, we explore how the software aids investigators in this critical process:
In the investigation of CSAM cases, every detail counts. This email forensic software helps investigators sift through large volumes of email data to find key evidence. This could help lead to the detection of offenders, victims, and also networks.
Advanced Features of Software to Detect CSAM Cases
Let’s explore how the software aids investigators in this critical process:
Comprehensive Email data analysis
This software is capable of analyzing emails from over 20 different email formats. This software is worldwide famous for its email header analysis feature. This provides a comprehensive view of communications related to CSAM cases. This allows investigators to uncover hidden messages, attachments, or metadata that might otherwise be missed. By providing full access to email content, including body text, attachments, and metadata, it ensures that no stone is left unturned. It is also highly capable enough to extract email metadata from information like the sender’s location, etc which can play an important role in CSAM investigations.
Advanced Search and Filter Capabilities
It can simplify the investigation task by providing an advanced forensic keyword search feature. Investigating officials can use this feature to filter cases based on date, sender, or subject. It can even search for a specific keyword or phrase in any file type. This can particularly be useful in CSAM cases, where finding specific keywords, patterns, or images that indicate illicit activity is crucial. The ability to quickly isolate relevant data can drastically reduce investigation time.
Image and Document Analysis with OCR Reader
CSAM cases are often graphic material that is shared as an attachment in emails. This software is capable enough to check suspicious email attachments. The software’s built-in OCR forensics feature allows investigators to scan and analyze images, documents, and other non-text content for hidden data. This feature can reveal inappropriate or illegal material to track the perpetrators and victims involved.
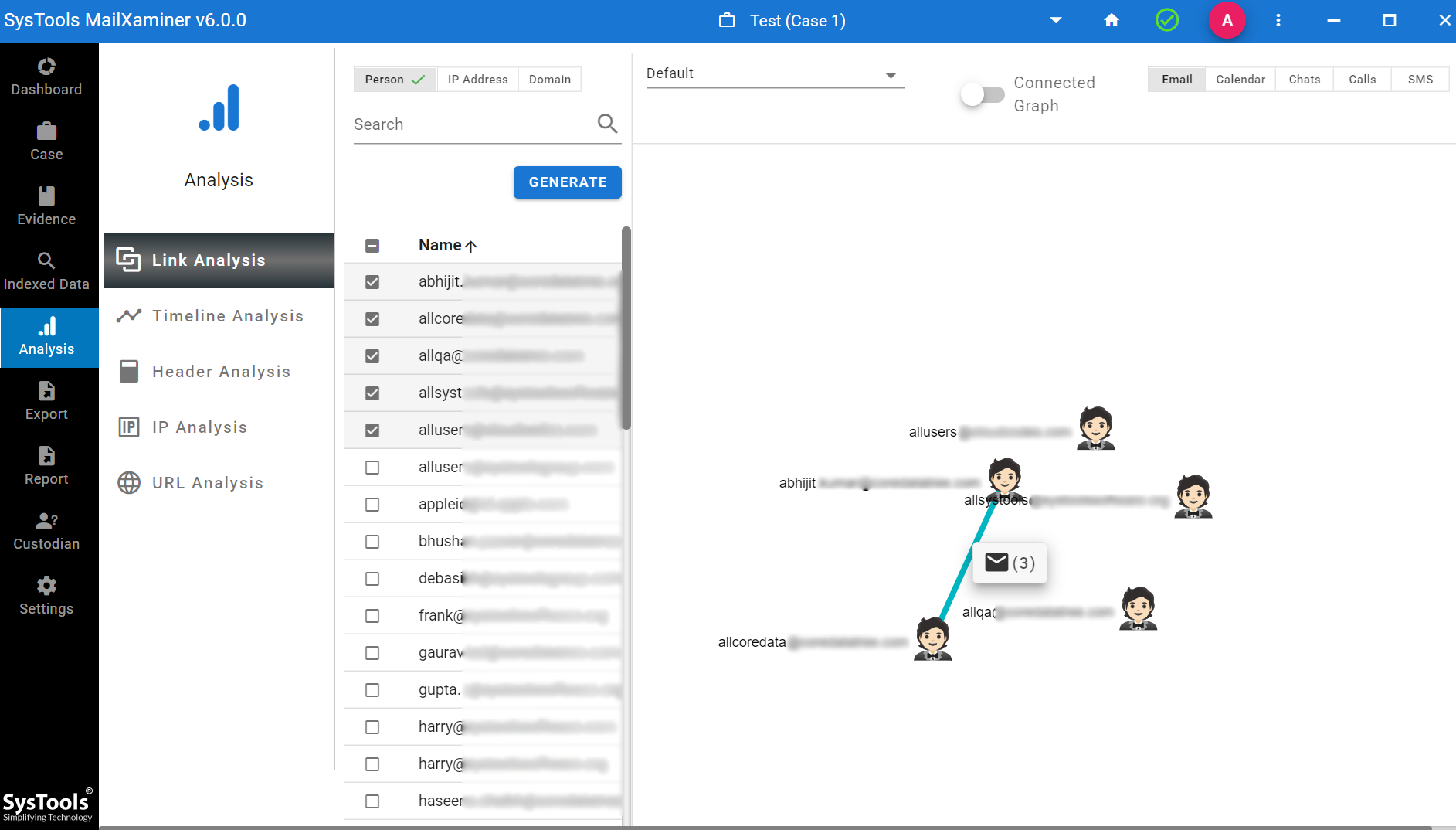
Analysing Link Connections Between Prosecutions
While investigating CSAM cases, a feature of link analysis allows the investigator to visualize the relationship between individuals or groups involved in CSAM networks. This feature of the software is especially important in CSAM cases where case perpetrators operate in organized groups or networks.
Maintaining Chain of Custody and Legal Compliance
In CSAM investigations, this software is capable enough to maintaining the integrity of the evidence. This also ensures that the evidence is admissible in court. The tool automatically logs every action performed during the investigation. It can preserve the chain of custody and ensure that no data is tampered with or lost during the analysis process.
Conclusion
The fight against today’s most emerging topic CSAM is a complex and urgent endeavor. It requires strict actions to protect our youth and the coming generations from fraud against sexuality. Highly advanced technological support can truly prevent CSAM from detection to prosecution. This powerful software is designed to detect, investigate, and prosecute offenders effectively.
CSAM investigators should integrate this type of advanced technology into the workflow to investigate cases and enhance their capabilities. After using this software the results will ensure that justice is served and victims are protected.

