How IP Address Criminal Investigation Helps Track Cybercriminals?
An IP Address criminal investigation is tracking an IP address to uncover the identity or location of the suspect involved in a digital crime.
In today’s hyper-connected world, every action we take online, whether it’s sending an email, browsing a website, doing any kind of transactions, or accessing a network, leaves behind a trail. At the heart of that trail lies something critical, i.e IP address. It’s often the first breadcrumb forensic investigators follow in search for evidence within Emails when a cybercrime takes place.
Whether it’s online fraud, hacking attempts, identifying phishing emails, or tracing the origin of an IP address can help law enforcement agencies connect digital evidence to a physical person or device. But this process isn’t always straightforward. With the rise of VPNs, proxies, and techniques like email spoofing, criminals have gotten smarter about hiding their tracks.
In this comprehensive guide, let’s understand what IP address is, how IP address in criminal investigation work and what is the role of IP address in investigation. You’ll also learn about the current challenges in digital Forensics Investigations that investigators face and how landmark cases were solved using digital forensics techniques and IP tracking techniques.
If you’re a cybersecurity expert, network administrator, or someone in digital forensics, you will surely find this guide helpful that sharpen your investigative skills and understand the real-world applications of IP-based investigations.
What are IP addresses and How It Looks Like?
To understand IP address criminal investigations, you first need to grasp what an IP address is. So, in simple terms, an Internet Protocol (IP) address is a unique set of numbers assigned to every device that connects to the Internet. Think of it like a home address, it tells the network where to send the data, whether it’s a webpage, an email or a video.
Today, there are two main versions of IP addresses in use:
- IPv4 (Internet Protocol version 4)- This is the most common format. It looks like this “192.168.1.1“. This is a four-set of numbers separated by periods. But today due to so many online devices, it’s nearly run out of IPv4 addresses.
- IPv6 (Internet Protocol version 6)- To solve the shortage, IPv6 was introduced. It uses a longer format like 2001:0db8:85a3:0000:0000:8a2e:0370:7334. This allows for billions of unique addresses. It is more than enough for every connected device on the planet.
There is an important distinction between static IP addresses and dynamic IP addresses. Over time, a static IP address remains the same and is often used by the servers or businesses. On the other hand, a dynamic IP charges periodically and is typically assigned by an ISP to regular home users. This difference matters in criminal investigations.
Static IP addresses are easier for IP analysis to a user, while dynamic IP requires investigations to investigate a suspicious email activity occurred to match it to a user.
What is the Role of IP Address in Investigation?
Today in the world of cybercrime investigations, an IP address is often the first clue, just like the same as fingerprints at a crime scene. An IP address helps law enforcement and digital forensic experts trace the origin of a crime, conduct link analysis for illegal activities, and build a timeline analysis in digital forensics.
There are various types of email threats. So, when a cybercrime occurs, whether it’s unauthorized access, DDoS attacks, or data breaches, one of the first things investigators do is analyze URL for malware or logs. Web servers, email systems, firewalls, and even chat applications log IP addresses of users who connect or send data. These logs become crucial digital evidence collection in cybersecurity.
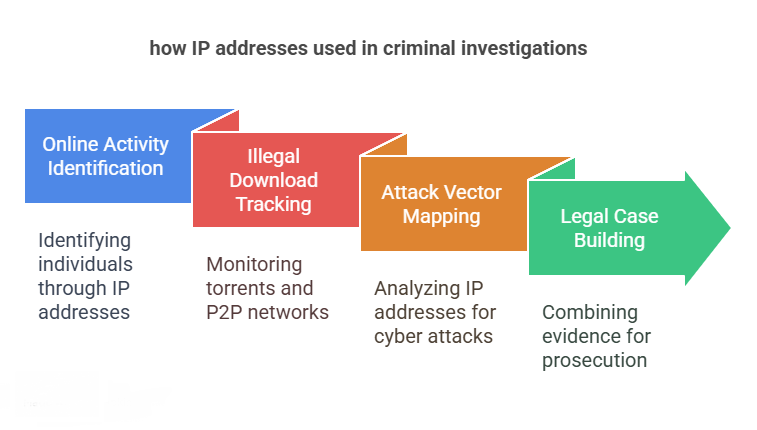
How Law Enforcement Tracks IP Addresses
Tracking an IP address in a criminal investigation isn’t a quick WHOIS lookup for any investigator, whether it’s a law enforcement official or a digital forensic expert. These cyber experts need to follow a strict, structured, legally compliant, and technically sound process to trace email sender digital footprints of suspects.
Here is the process of how the process works in the real world:
1. Linking Online Activity to Individuals
Whenever someone visits a website or sends an email, their device shares its IP address. And here is the first solid evidence investigator got against the suspect. Cyber experts work with the Internet Service Providers (ISPs) to find out which user was assigned that IP at a given time. Performing IP analysis in digital forensics or subpoenas, or warrants carefully, you will be able to obtain the name, address, and contact information of the person behind the IP.
2. Tracking Illegal Downloads or File Sharing
In cases involving piracy, CSAM detection, or illegal content distribution, authorities monitor torrents or P2P networks. When someone downloads or shares prohibited material, their IP address is exposed and recorded. These IP logs are then collected as part of the evidence.
3. Mapping Attack Vectors
In cyber attacks, investigators analyze incoming IP addresses to determine attack patterns, identify command and control servers. In an IP address criminal investigation, the hacker uses various proxies or a VPN, so it is authorized to perform a careful traffic analysis that will help trace back to the original IP.
4. Building a Legal Case
An IP address alone isn’t always enough to convict someone. The investigator needs to make many efforts and challenges to analyze the case of evidence from every angle. This includes device logs, geolocation data, browsing fingerprints, and email metadata analysis.
Still, challenges exist. Criminals may use IP spoofing, Tor networks, or VPNs to hide their location. That’s why modern investigations require a blend of advanced tools to truly connect the digital dots.
Best Way to Analyze IP Address Criminal Investigation
For digital forensic investigators or cybersecurity professionals, handling IP address criminal investigations is both an art and a science. Here in this, the stakes are high. One single mistake can lead you an entire case or violate someone’s rights.
To avoid any kind of mistakes and handle the complete data smoothly, one must opt for MailXaminer. This is the advanced Email investigation software, which is especially designed for digital examiners to analyze the evidence in the right and effective way.
It is capable enough to detect spam email analysis, correlating timestramps with IP logs or email header analysis. This advanced forensic data analytics software provides powerful features for deep-level investigation. It supports over 25+ email formats, includes advanced features, and helps analysts trace the path of emails back to the originating IP addresses even in complex infrastructures involving proxies, etc.
How Software Helps in IP Address Criminal Investigation
Gone are the days when cyber forensic investigations relied solely on manual analysis of evidence and guesswork. Today, forensic software automates much of the heavy lifting, collecting, correlating, and analyzing data from vast digital sources. Talking about this software, let’s see how the software helps in IP analysis in criminal investigation so smoothly and effectively.
- Step 1. Install the software into your system and a new case.
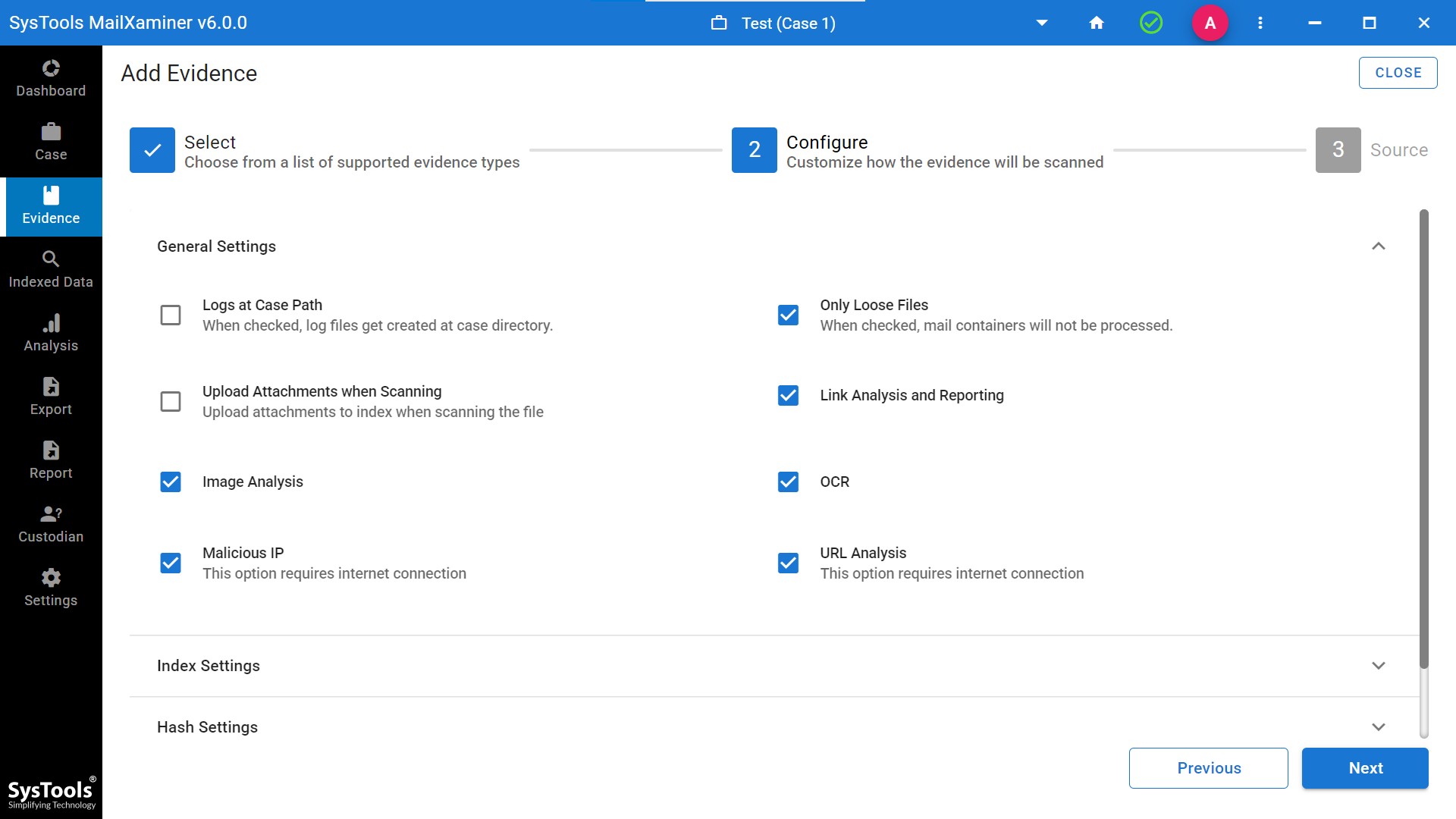
- Step 2. Add evidence as per your requirement. Software provides you with 20+ email clients through which you can add evidence. Tap on Next.

- Step 3. Then, select the general settings as per your requirements. Do not forget to select the Malicious IP for the analysis of IP addresses.
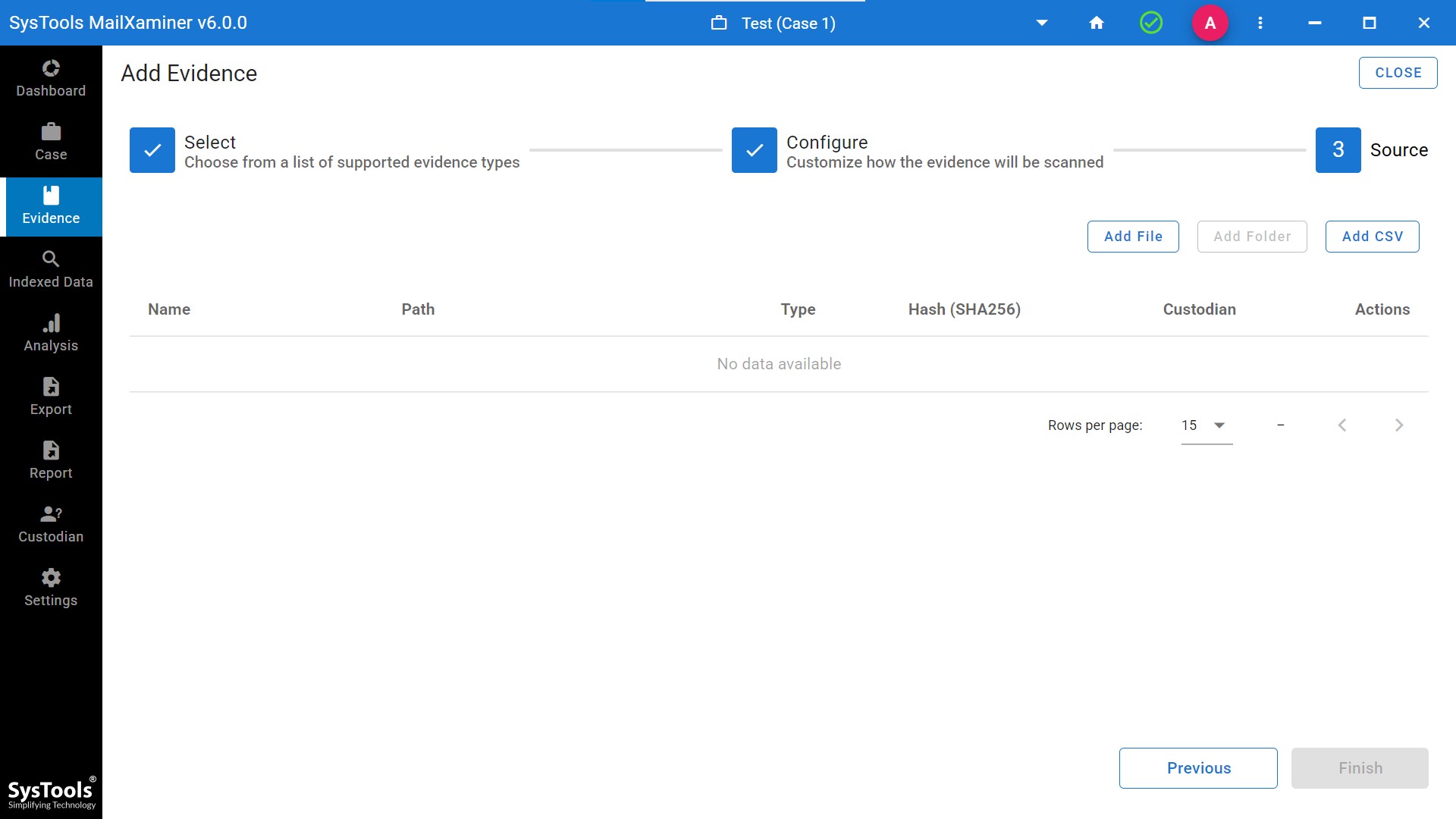
- Step 4. Then, add the file that you want to analyze. It will provide you with an option to add files, or you have the option of adding CSV as well.
- Step 5. Then, the software will provide you with complete data of markers, Tags of malicious IP or not, subjects of emails, details of the sender, time of email send and received, and also the size of the file.
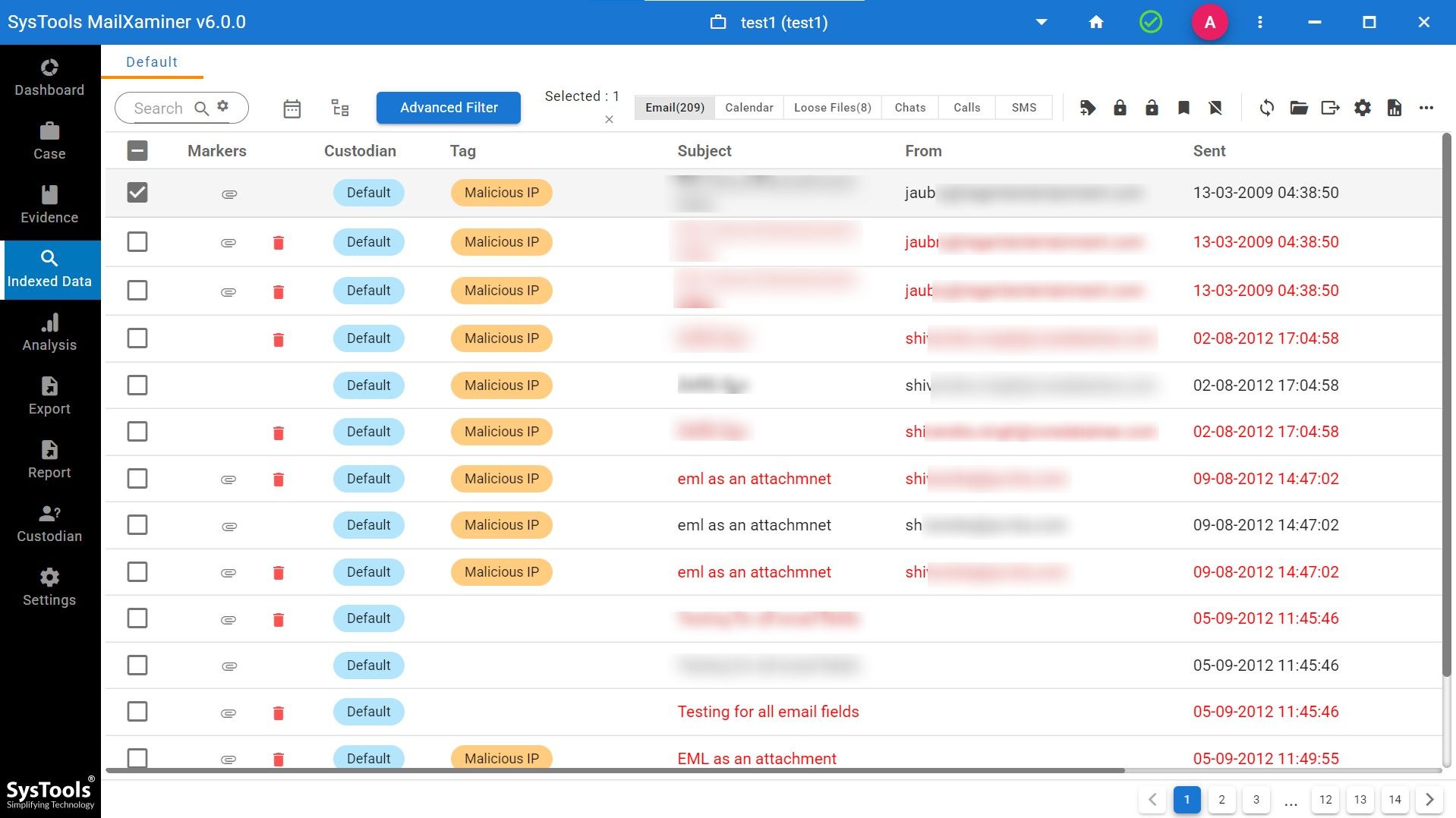
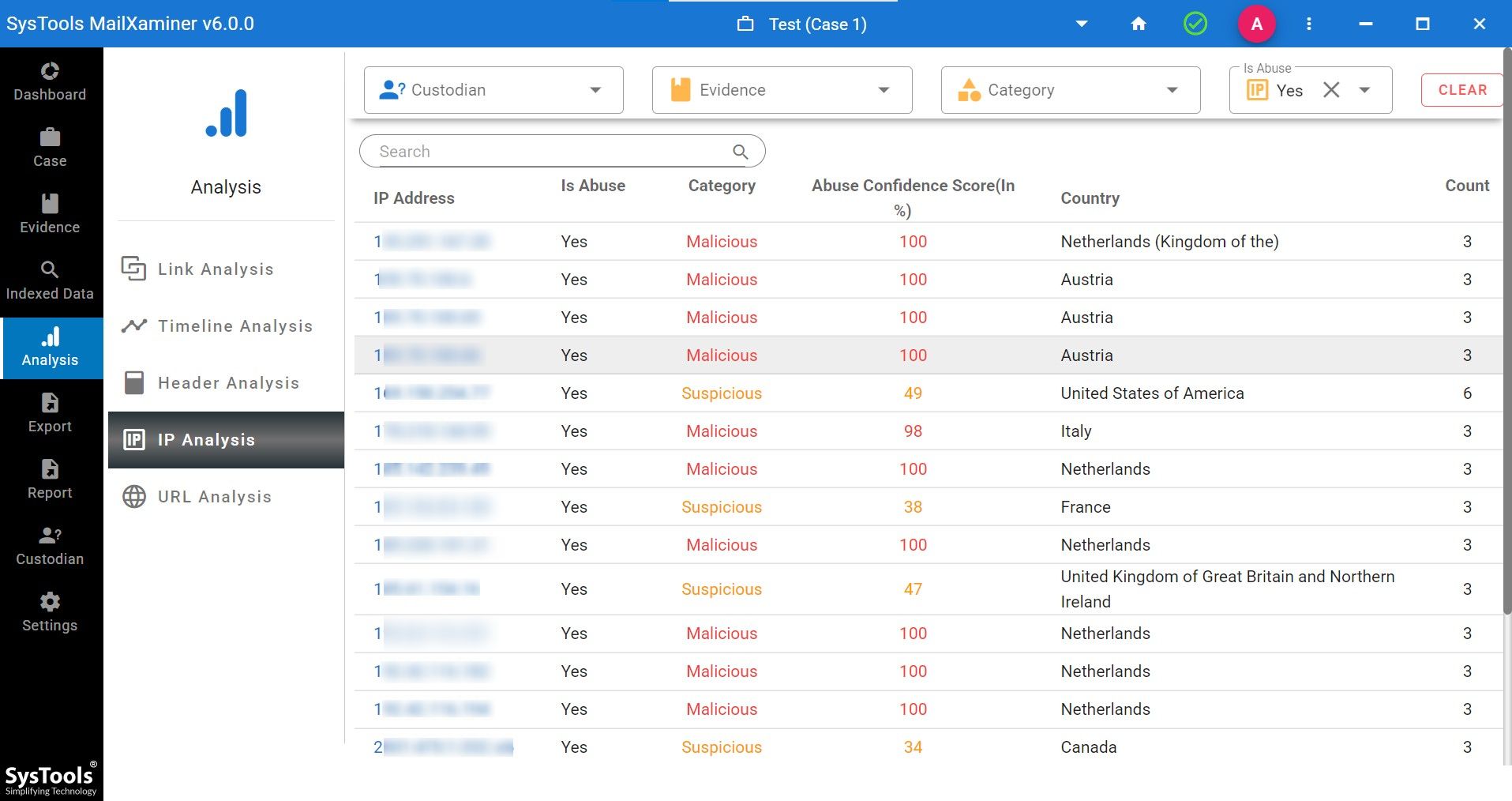
- Step 6. Then comes the major part, the IP analysis one. Though software will provide you with various options but here we will proceed to analyze the IP addresses. Tap on the IP analysis feature and software will show you all the malicious IP addresses, status of IP, category, country and score of abuse confidential.
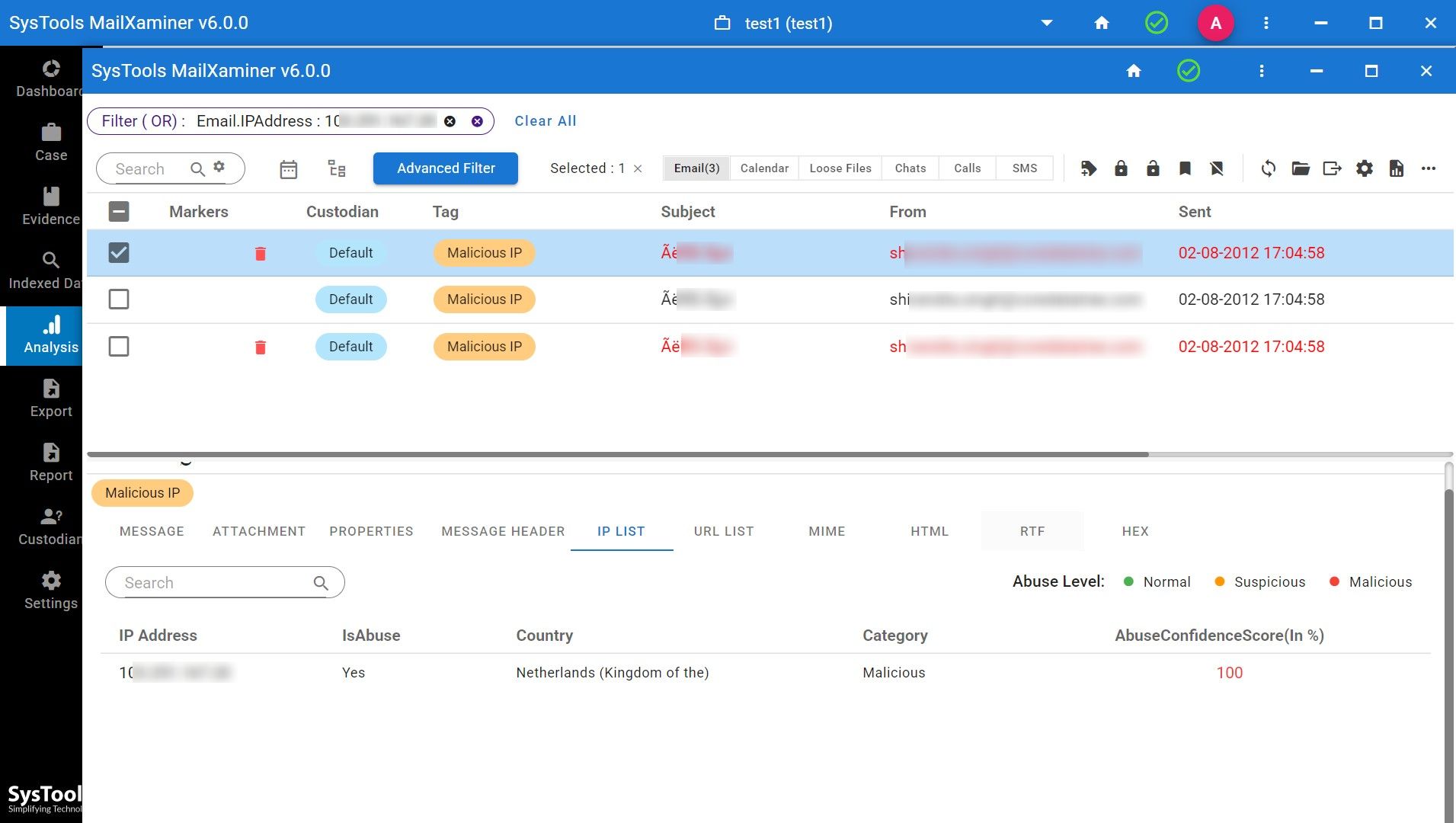
- Step 7. Through this analysis, one will be able to check the IP’s individually by selecting the options. It will show you various options like message, attachments, message header etc.
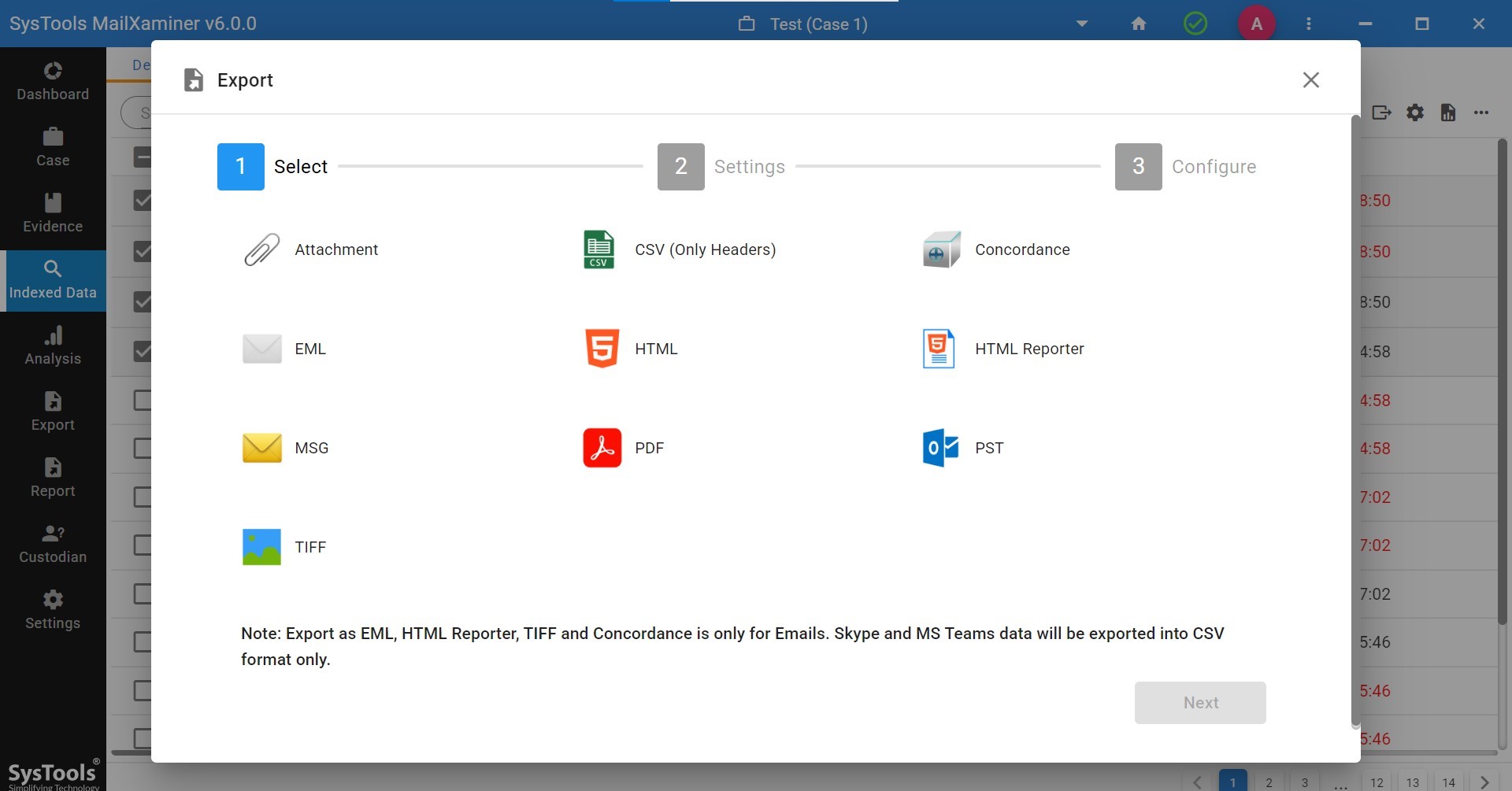
- Step 8. Lastly, export the selected files as per your requirements, which involves all the suspicious or malicious IP addresses.
Note- Here we will process with PDF file format option. You can opt for any export option as per your preferences.
- Step 9. Then select the IP settings. Software will provide you with the option to maintain the folder hierarchy or exclude malicious URL items.
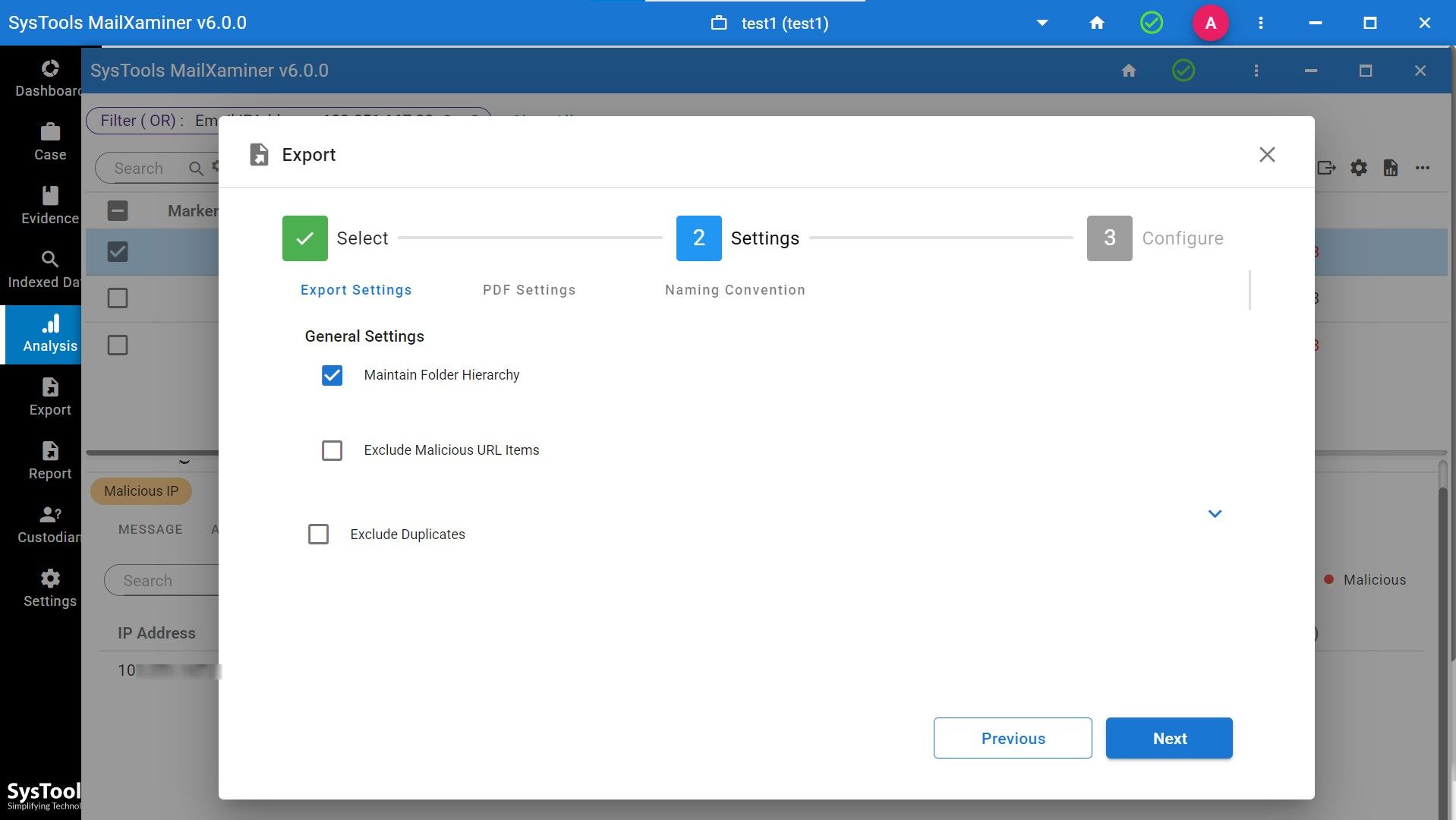
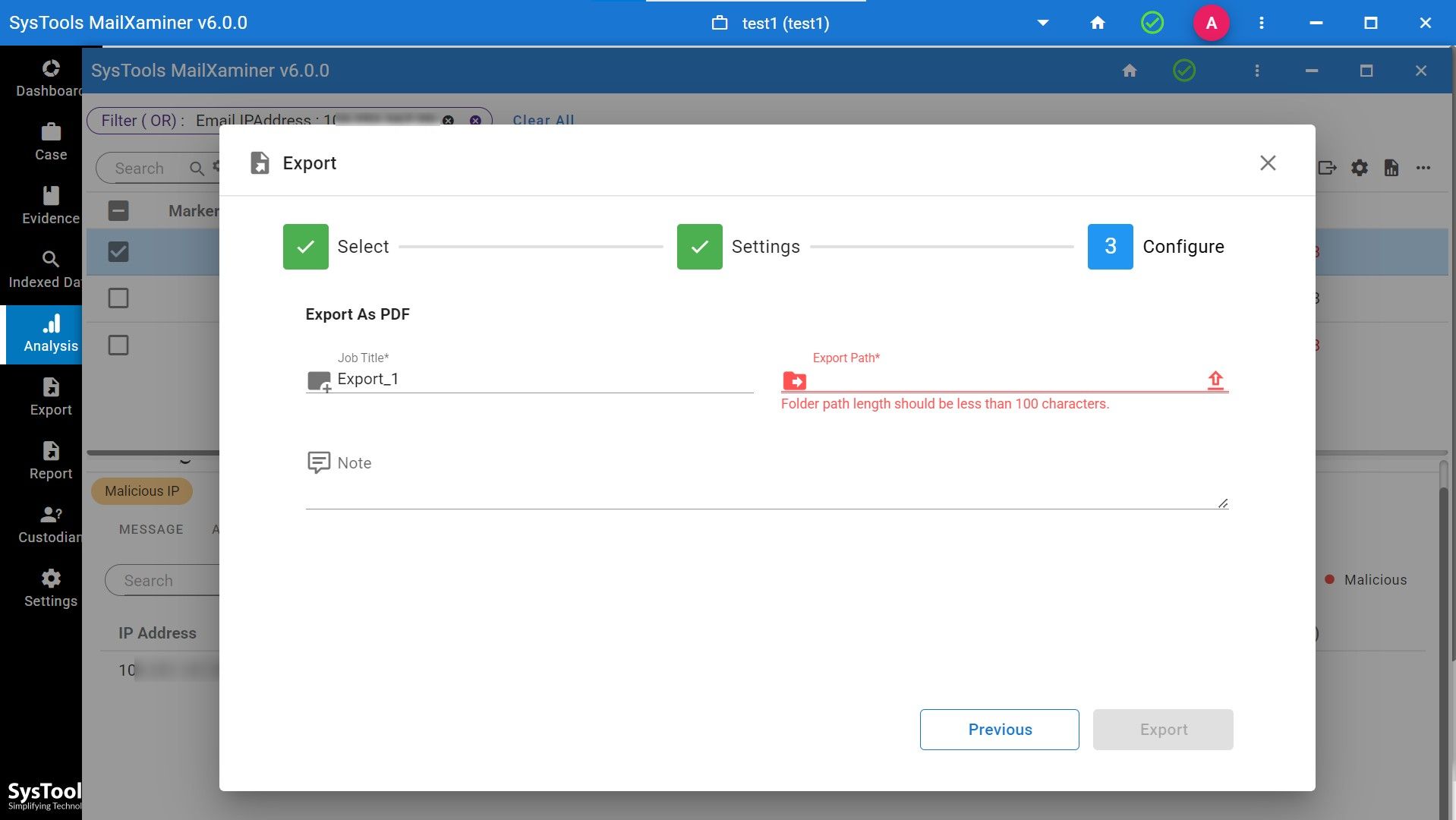
- Step 10. Lastly, select the job title and export path where you want to save your file.
Final Thoughts
IP addresses are crucial tools in the digital forensic toolbox. But they’re just one piece of a much larger puzzle. From cybercrime attribution to legal admissibility, understanding both the power and limits of IP tracking is essential for professionals in cybersecurity and digital investigations. Therefore, it is crucial for the same side for the investigator to perform IP address criminal investigation.

