Office 365 Email Forensics Investigations – Complete 2025 Guide
Even after Office 365 transformation to Microsoft 365, the need to conduct email forensics has not diminished. On the contrary, we can say that more and more organizations are now coming forward with the demand for Office 365 forensics preservations. Moreover, this practice needs external assistance, as administrators alone can’t handle the sheer volume of data present in the Office 365 cloud.
Suppose we begin to list the data points typically searched for in a digital investigation. In that case, we see email content, attachments, header data, sender & recipient information, and much more. This is just the start of what detectives need to find, as the actual email metadata analysis goes much deeper.
Businesses all over the world use the O365 service to conduct communication and collaboration within their organization. This is not a surprise as we are talking about a product that encompasses nearly all workplace demands. All thanks to its library of apps like PowerPoint, Exchange Online, Office Online apps, SharePoint Online, etc. However, the same tools are being used by nefarious entities to target businesses. This is one reason why we saw a rapid increase in the need for Microsoft Teams Forensics as well.
Table of Contents
Therefore, there is a requirement for bulk email investigation to produce it as evidence in court. Here, we introduce Office 365 forensics analysis software.
Such a need arises because of the large number of spam emails that get into the Office 365 profile. With this blog, we will shed light on the importance of Office 365 email forensics in a seamless way.
How to Track the Originality of Unsolicited Microsoft 365 Emails?
Spam emails are responsible for all kinds of attacks or infections that may occur in an organization. To deal wisely with spam emails in an Office 365 profile, it is important to analyze the email headers. The knowledge about email headers helps to investigate officers to know how to trace an Email IP address in Office 365 for investigations.
One can track the source of spam emails, which are also known as unsolicited commercial emails (UCE), by following the steps given below:
- Analyze the email header of the suspected email message
- Examine the received email headers in backward flow with your ISP
- Detect the sender of the last verifiable email handling server
- Check all URLs and email addresses that correspond to the spam email
How Does Office 365 Forensics Analysis Help in Spam Emails Examination?
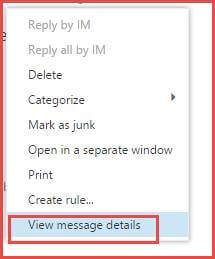
Once the email has been sent by the sender, it will traverse through several systems. As a result, header data is modified at every system whenever it migrates until the point it reaches the designated recipient. The investigators need to know about the details of email headers to clarify whether it is spoofed or not. To analyze the content of the message header in Office 365, the forensics experts have to select the particular message that he/she wants to examine. Following it, select the option “View message details” which reveals the email header details of that specific message.
- DKIM Verification: DKIM (DomainKeys Identified Mail) verifies the digital signature of the suspected email message and checks whether the signature is valid or not. It helps to identify whether it is an original email or a spammed email.
- DKIM Signing: O365 supports DKIM signing for all outgoing emails that help to distinguish the fully hosted customers, hybrid customers, etc.
- Increased URL Filtering Coverage: Currently Exchange Online Protection (EOP) uses 750,000 URLs in its antispam and anti-phishing detection. If the email message contains this URL, then it is considered a heavyweight in the spam filter.
Receiving False Email Message Header
Sometimes Microsoft 365 message headers of the emails are forged to deceive users so that they are not able to trace the originality of the emails. Such types of forgeries are examined in the process of tree format as shown below. A typical email handling process is carried out in a tree-structured format. It is analyzed with the help of message headers and the various subfields that are essentially involved in the email migration.

The tree shown above illustrates that out of 325802 emails arriving at B.net. Most of the emails (325090) come through mail.R.com and the remaining come through mail.H.com. Here, a correlation can be established between B.net, mail.R.com, and mail.H.com.
It can be noticed that some of the emails which arrive at mail.R.com move via mail.H.com and then finally they again go back to mail.R.com before destination B.net. Based on the location of different servers involved, the convolution between the providers may act as evidence in the event of intentional forwarding of emails.
Examining the Spam Header
When Exchange Online Protection (EOP) scans an email message, it places the X-Forefront-Antispam-Report header into each email. These fields present in the header of messages can provide information about the message. Additionally, the X-Microsoft-Antispam header renders detailed information regarding bulk mail and phishing activities.
Microsoft Office 365 EOP employs the SCL (Spam Confidence Level) value to determine if a message should be categorized as spam or not.
Email messages with an SCL value of less than 4 will be transferred to the designated recipient inbox. However, messages with an SCL value of more than 5 are considered inherent spam and they get transferred to the recipient’s Junk folder. Additionally, an SCL of 9 is regarded to be rigorous spam.
Analyze Office 365 Email Headers Via Advanced Office 365 Forensics Analysis Tool
MailXaminer is one of the most professional Email Investigation Software which smoothly helps you to conduct an Office 365 investigation without any difficulty. This software is designed to provide numerous advanced features and can efficiently examine spam emails from Office 365 using its multi-mode preview options. It is a user-friendly software that offers the best set of features in a simplified user interface. So, let’s have to look at the procedure to perform Office 365 email analysis using this remarkable software.
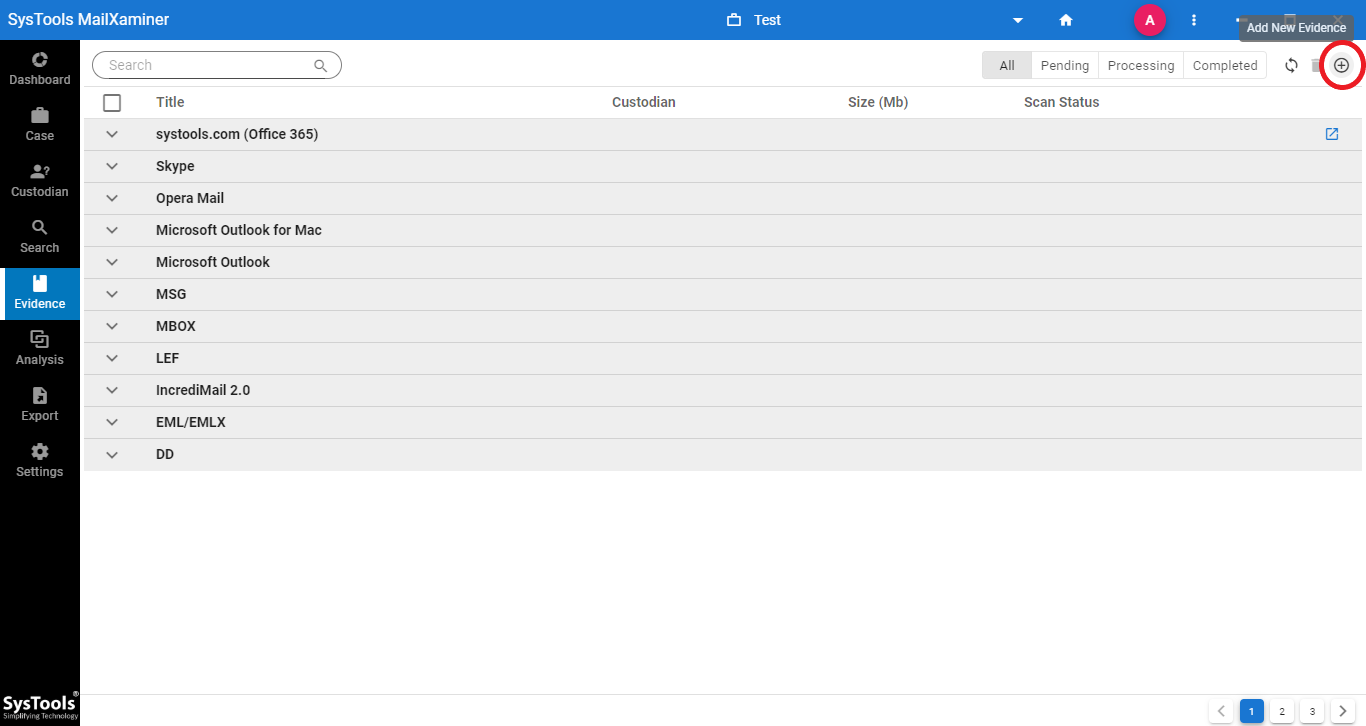
1. Once the software gets launched on your system, click on the Add New Evidence button as shown in the below image.
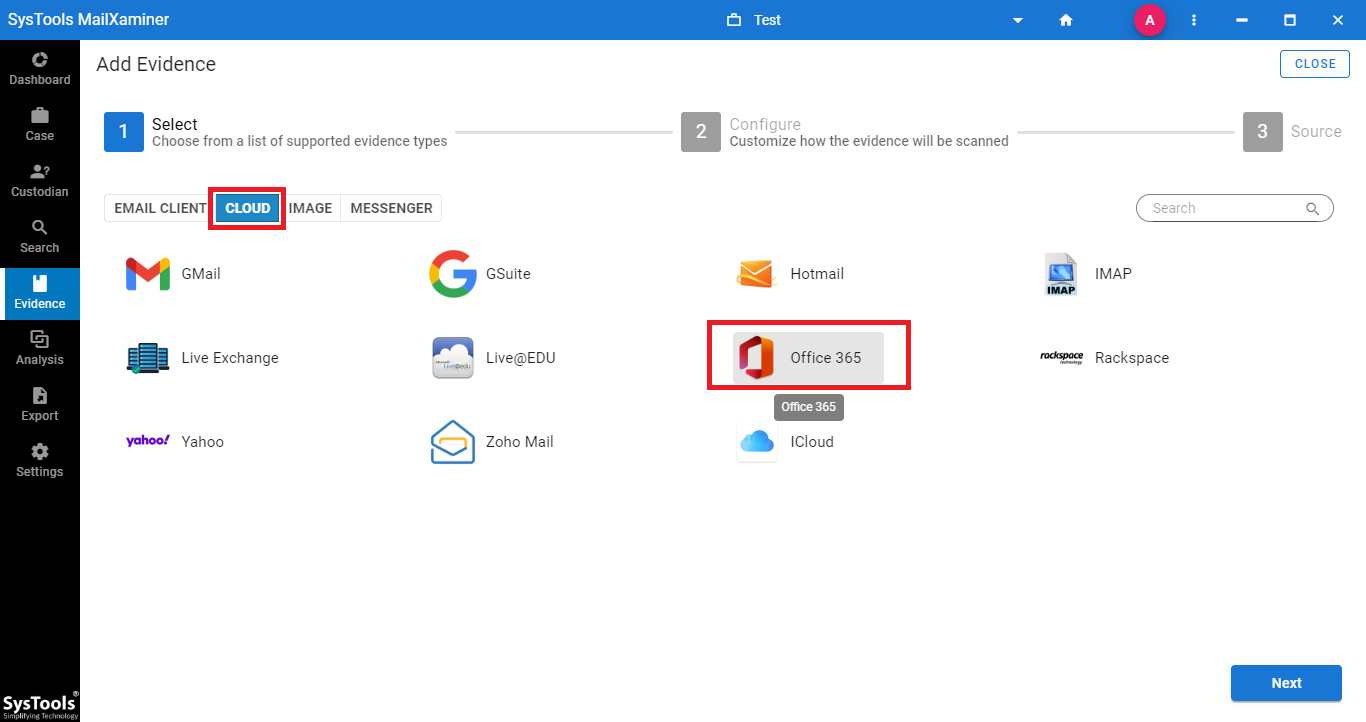
2. From the Add Evidence screen, go to Cloud >> Office 365 and input the credentials of the Office 365 account.
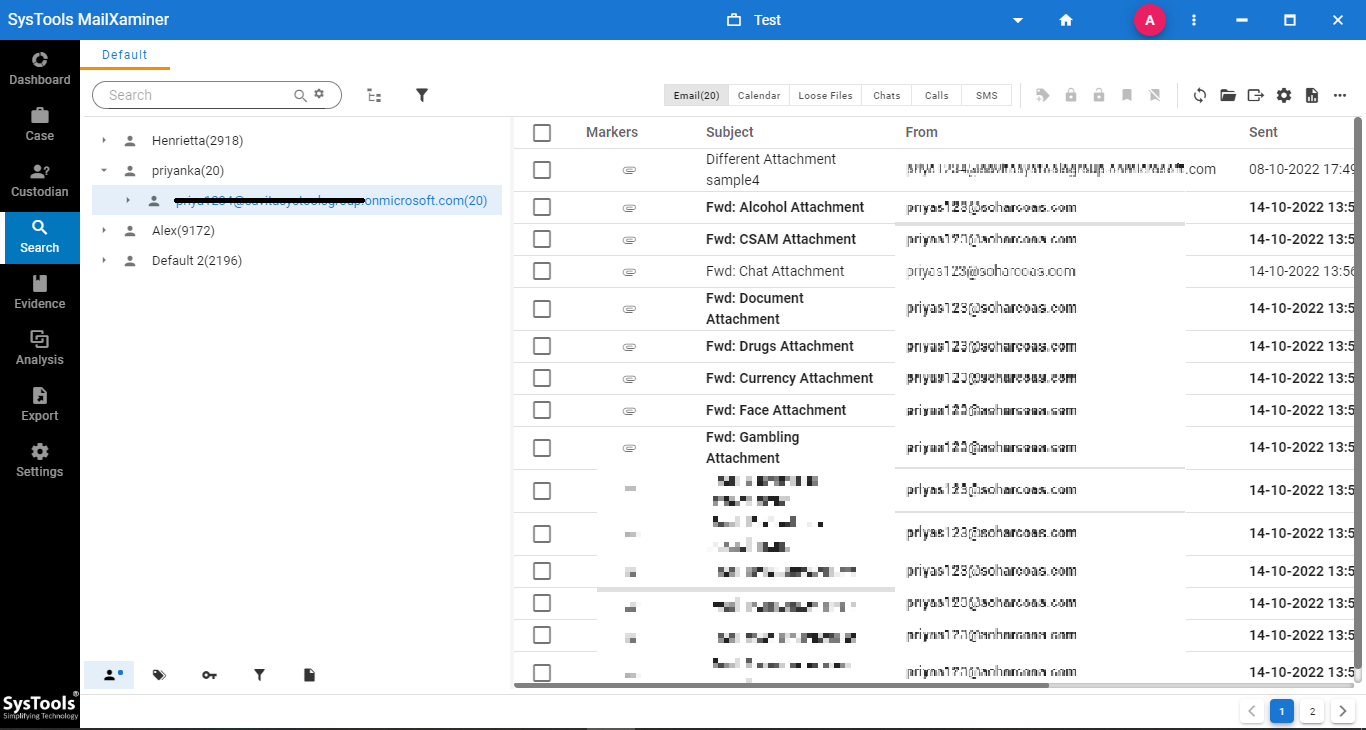
3. Once the file is loaded on the software panel, it provides a preview of all folders in a tree structure. Moreover, the emails can also be viewed by selecting the respective folders.
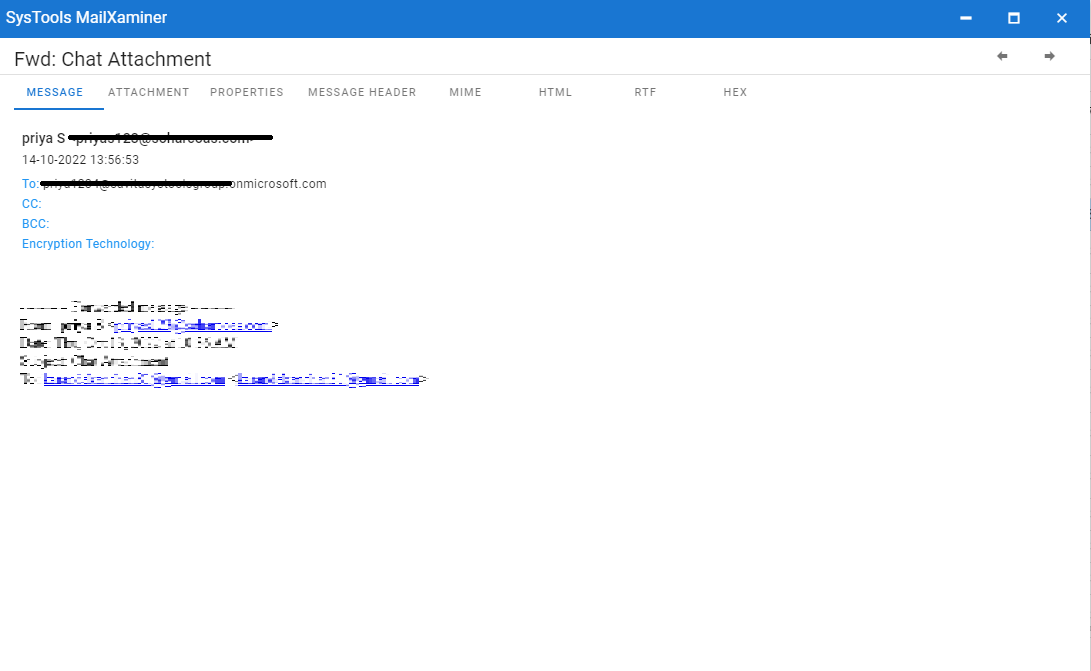
 4. To preview the emails in different views such as Message, Hex, Properties, Message Header, MIME, HTML, RTF, etc. Simply click the email to be viewed. From the below image, investigators can examine the emails in different views in a thorough manner
4. To preview the emails in different views such as Message, Hex, Properties, Message Header, MIME, HTML, RTF, etc. Simply click the email to be viewed. From the below image, investigators can examine the emails in different views in a thorough manner
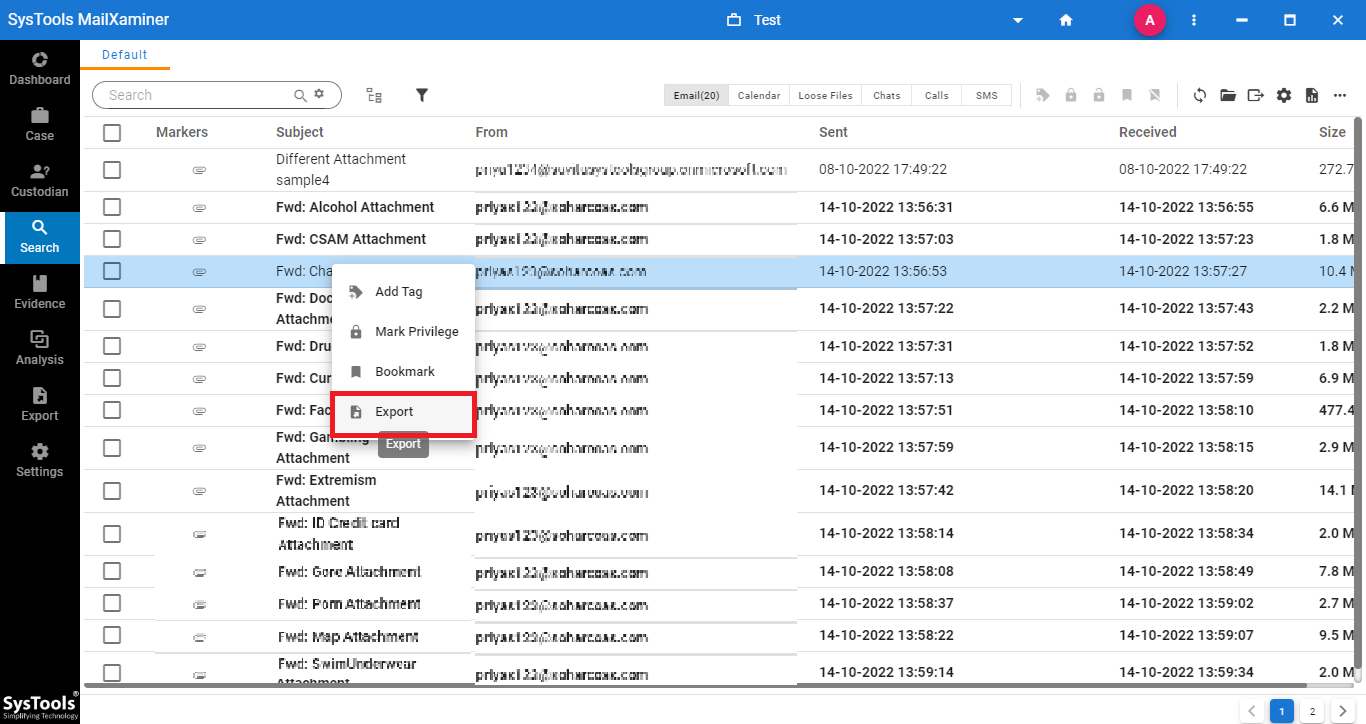
5. The software allows us to export Microsft 365 email forensics output in different file formats. For that, select the desired emails to export and click the Export option. One can also export bulk emails by selecting the respective folder to transfer from the software panel.
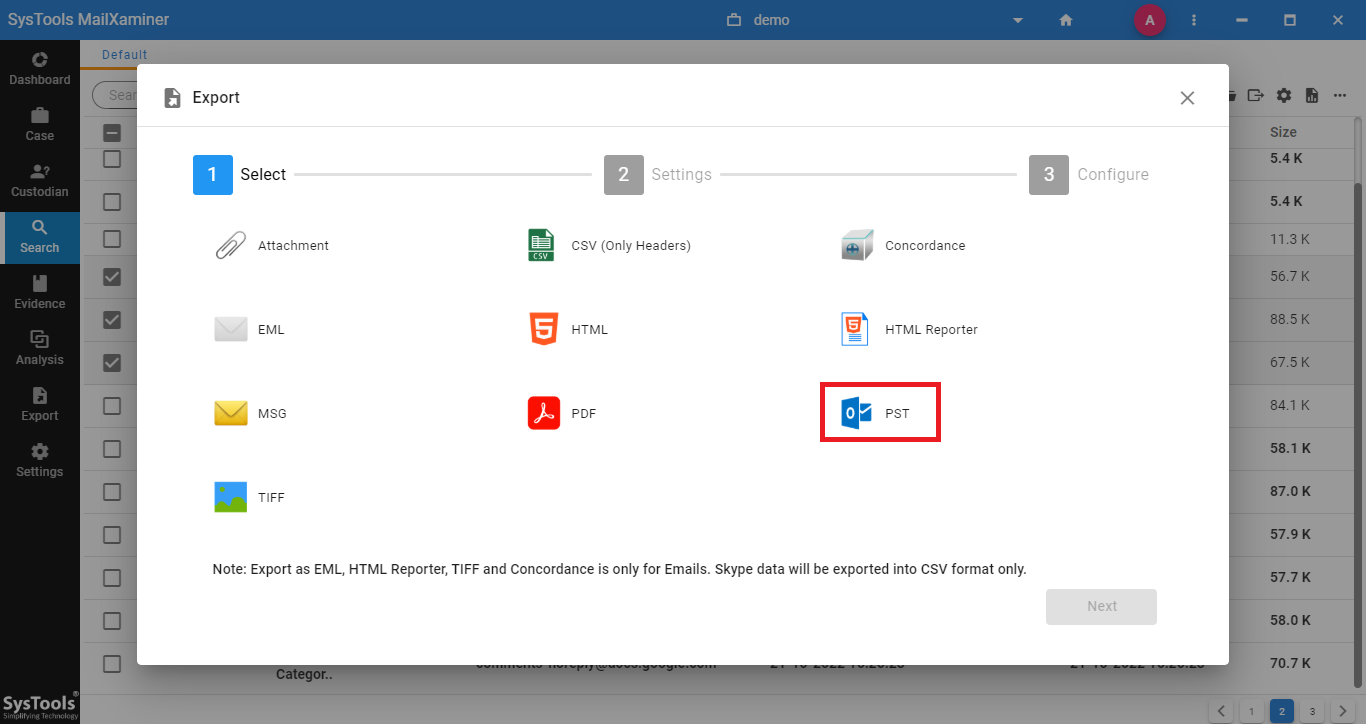
6. Under Export screen, one can choose the required file format wherein the emails will be converted into the chosen file format. The different file formats offered by the software include HTML, MSG, PDF, EML, CSV, etc.
The Bottom Line
With the advanced functionalities rendered by Office 365, a majority of the users prefer to avail the same. However, concerning the spam emails, it is important to perform an in-depth analysis using specialized email forensics software. With its best-in-class features, one can smartly track the source behind the spam emails in a sophisticated way.

