How to Analyze URL for Malware: Detect & Remove Malicious Links
The Internet is great, but it is dangerous too. Most of the websites you visit will be fine, but no one knows who has clicked on a link in the email. Malicious URLs are one of the most frequent tactics cybercriminals employ to make you download malware or expose valuable information. The good news? You can easily analyze URLs for malware to avoid falling victim to various suspicious attacks, scams, and data theft.
This article will instruct on a way to detect malware in email and the significance of being aware of this in terms of internet safety. Of course, if you’re a digital forensics buff, or beyond that maybe a cybersecurity pro or you just wanna protect yourself; recognizing bad URLs is an important skill. Read on for how you can take control of your security online by analyzing links carefully and staying away from bad ones.
What Are Malicious URLs & How to Identify Them?
What do malicious URLs mean when you hear that? A malicious URL, in essence, is a hyperlink to a site that has been crafted with ill will. URLs are usually phishing sites, malicious software download places, or fraud sites going around to swipe personal data.
In emails, these malicious URLs can be disguised to look like legitimate sources. Some of the more common types of malicious URLs include fake bank login pages, phishing sites designed to steal credentials, or websites that automatically download malware to your device once clicked. Spotting these malicious links can be challenging, but link analysis in criminal investigation helps trace their origins. This will detect the cyber-criminal networks and attack patterns.
Spotting these malicious links will be hard if you’re not yet used to seeing them. Yet there are some red flags to watch out for. Such as domains misleading or a weird pattern (e.g. extra letters and/or misspelled) Phishing URLs are also known for looking so legitimate oftentimes an extra letter or two at the end that you might not see as a mouse-over.
Even more importantly, HTTP (and no HTTPS) might mean the site is not secure. Whether that’s a red flag or not, unencrypted sites are much more often home to nasty things like malware and phishing attempts.
To sum up, one of the most critical things to identify URLs for malware is necessary when dealing with email links (the attacker’s goal is prone something on targeted individuals) as it takes place in case you need to be safe in the online world.
Indicators of Compromise (IoC)- First Step Towards Analyzing URL
When it comes to analyzing URLs for malware, one of the first steps is understanding the indicators of compromise (IoC) that could point to a dangerous URL. These are patterns or anomalies that signal that a URL might be compromised and harmful to click. A technique like Timeline analysis in digital forensics can also play a crucial role in tracing when and how a malicious URL was created, distributed, and accessed
- Unfamiliar or misspelled URLs: This is one of the most common red flags. Cybercriminals often create malicious URLs that closely resemble trusted websites but with slight alterations.
- Suspicious-looking redirects: Another sign that a URL may be malicious is if it redirects you unexpectedly.
- Requests for unusual permissions: Websites that ask for permissions beyond what’s necessary are highly suspicious.
- Requests for unusual permissions: Websites that ask for permissions beyond what’s necessary are highly suspicious.
- Lack of HTTPS encryption: If the URL doesn’t begin with “HTTPS” and you see just “HTTP,” there’s a higher chance the website could be insecure.
To properly analyze URLs for malware, it’s important to watch for these IoCs. Using tools like VirusTotal, Google Safe Browsing, or browser extensions can help detect these risks and ensure that you’re not unknowingly clicking on a dangerous URL.
How to Check URLs for Malware Through Advanced Software?
It is important to know how to analyze URLs for malware, but having it is always important to check through advanced techniques. This is so because this technique not only analyzes the URL for malware but also provides you with more advanced features for email forensics examinations.
MailXaminer is an advanced email analysis software that can make your investigation of emails more advanced. This software is designed to make digital investigations by offering powerful email search, analysis, and recovery capabilities. This is specially designed to be equipped with advanced algorithms that enable forensics experts for email metadata analysis.
Advanced URL Analysis Feature to Detect Phishing Attacks
This software allows investigators to thoroughly analyze URLs embedded in emails for phishing email forensics investigations. The software applies multiple layers of analysis.
Step 1. Create a new case and add new email evidence.
Step 2. Then, choose the email source for malware detection.
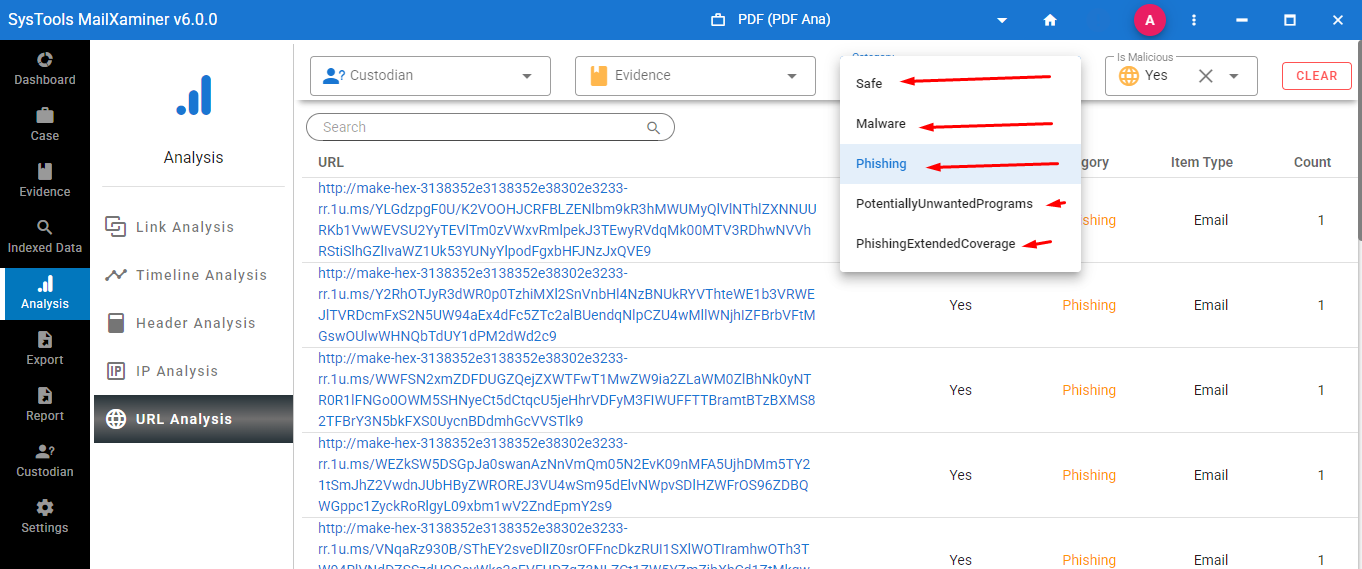
Step 3. After adding various cases software analyzes and detects the categories mentioning malicious, category, item type, and total cases count.
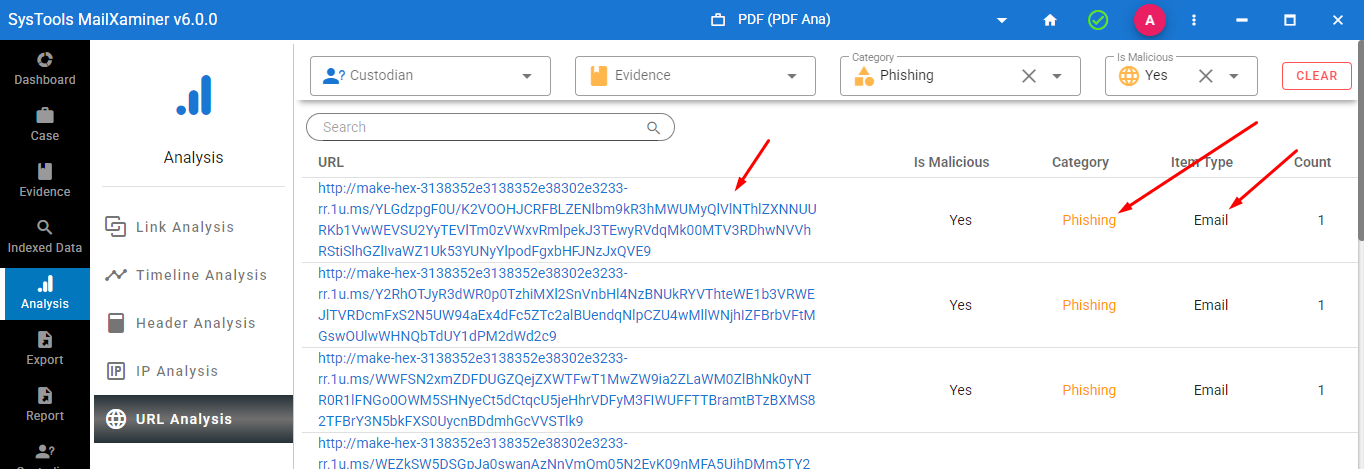
Step 4. Through this URL analysis feature, you will get a complete report of all the malicious URLs.
Conclusion
In this modern age of technology, defending your personal information requires understanding how to check URLs for malware. To trick recipients into downloading dangerous files or disclosing private information, cybercriminals frequently hide malicious links in emails. Identity theft, financial damages, or even an entire system compromise may result from these threats. You need to check emails and also frequently check suspicious email attachments.
Thus, maintain yourself against online threats by following the instructions in this guide and utilizing legitimate techniques. It should be a habit to regularly check links for malware, regardless of your level of expertise in digital forensics, interest in cybersecurity, or desire to stay safe online.

