How to Check Suspicious Email Attachments? Complete Guide
In today’s world, any email investigator must know how to check suspicious email attachments at their fingertips. These files that accompany an email message are the most common attack vectors through which nefarious entities perform their dirty deeds. Opening those suspicious email attachments may result in the introduction of malware into the device, and then you need to detect malware in emails.
When malware is installed on your system, it can result in so much data loss and can gain access to your system as well. Moreover, if users open an attachment that is suspicious and don’t follow the proper protocol, they can unknowingly invite malware, ransomware, and other malicious software onto their devices and network. As these programs are designed to spread, they can lead to significant financial losses and reputational damage.
So we prepared this guide with the sole aim of making you better at identifying the red flags present in a would-be fake email attachment. Let us start by defining what exactly makes an attachment malicious.
What are Suspicious Attachments?
Attachments that arrive in an inbox fall into suspicion when their source is not known. These are the types of files that raise the most concern at the receiver end. A critical aspect of email security is PDF file analysis, as seemingly harmless-looking documents or PDFs often hide malware, viruses, or bots. These unsafe documents can hijack your email account, infiltrate your system, and easily find PII data in emails.
Likelihood of an attachment being termed suspicious has a lot to do with the file type it belongs to. The most well-known culprits include executable files like .exe or .app. Sometimes these files are not directly present but instead a compressed copy in the form of .zip or .rar format. This is mostly due to the email size limit imposed by the providers.
Moreover, there have been instances where Microsoft Office files like .docx or .xls were used as carrier agents. These deploy dangerous macros like in the infamous case in 2015 where the notorious Sandworm team infiltrated the Ukranian Electric power system with help of similar agents.
So now that we know what a suspicious attachment is, the next logical question is how to identify it.
Tips to Check If an Email Attachment is Safe
Emails that contain an attachment that is sent with the wrong intent have all sorts of characteristics. However, keep in mind no single symptom is enough to put an attachment under suspicion so make the decision to flag it only after a thorough investigation.
Double-check who the sender is and if you or the people you know are the only ones on the receiver list. Professional emails, no matter how urgent, don’t appear out of nowhere. There is always a background and context behind a message. If the message is confusing, written in a manner that doesn’t resemble the person, or seems suspicious, it could be a case of email spoofing. If the sender is genuine but the message, then it might indicate that there is an insider who is misusing their company credentials or the ID has been hacked.
A spoofed email address makes it more difficult to be 100% sure. So another important thing to watch out for is whether your email address is in the “To” section or not.
Many email providers flag spam emails into the spam folder. Only the first few characters are visible rest of the content hides behind the continuation … part. Additionally, ensure you don’t open any attachments from those flagged emails as they’re likely to be phishing emails. It’s crucial to identify phishing emails to avoid potential security threats
No worries there is a trick to get the full attachment info just take your cursor over the attachment. A small bubble with appear that contains the full attachment name along with its file type. Use it to your advantage in figuring out if this is an attachment you would open or not.
But not just the attachment, the complete email might be suspicious so its required to investigate a suspicious email completely.
Remember do not click an attachment under any circumstance. Not unless you have ensured that it is safe to do so, or have gotten a green light from the security team.
Which Email Attachments are Safe to Open?
These are some email attachments that are generally safe to open:
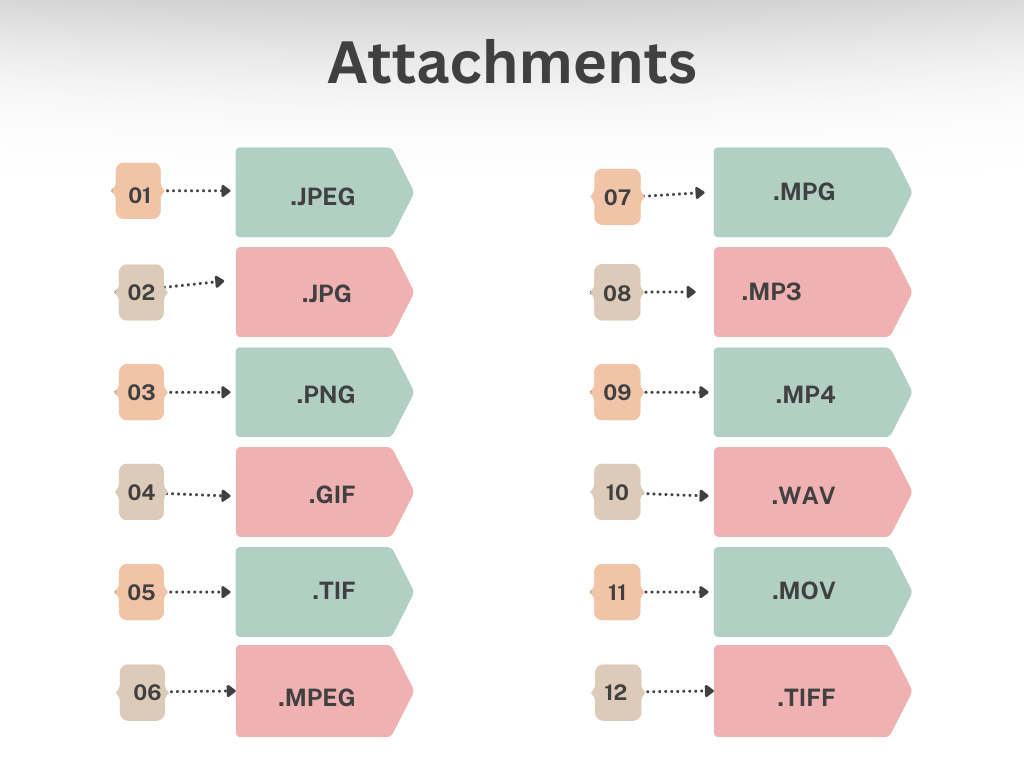
Which Email Attachments are Less Safe to Open?
The less safe email attachments are mentioned below:
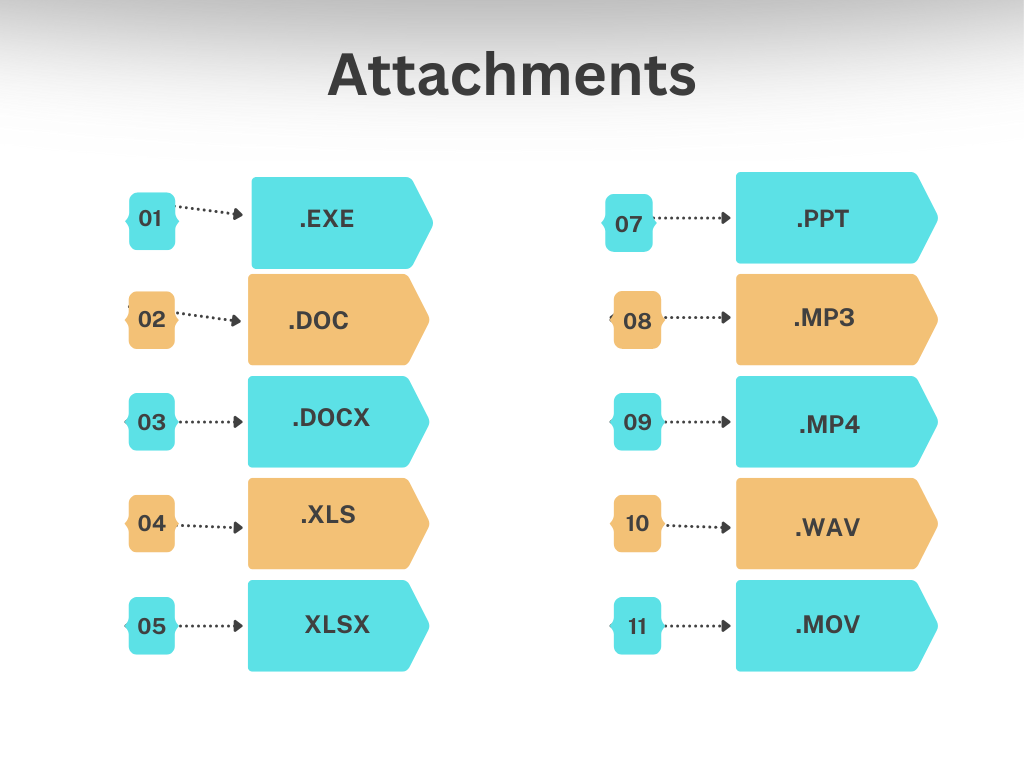
What to Do if You Open a Suspicious Attachment?
If a user accidentally opens a harmful attachment, it can be quite a nerve-wracking experience.
So, if you are someone who has accidentally found yourself with an already opened suspicious attachment, do the following to protect your system and data:
- Disconnect the Internet connection- First, turn off the device from the internet connection asap. Although malware/viruses and other entities are designed to work offline. During the early stages of cyber infection, they communicate with the source and inform it of the successful deployment. They then receive the next set of instructions. So if you disconnect the affected device, you prevent any of this communication from happening. Therefore, turn off wifi router and put your device on aeroplane mode ASAP.
- Start an Antivirus Scan: Use your system installed antivirus program to conduct a full scan of your system. Don’t rely on the quick scan in this emergency. Most of the paid anti-virus software can detect and instruct you on what to do in case a malicious file or activity is found on your machine. To make sure you are not caught off guard keep your antivirus up-to-date at all times. This is because there is always a new form of virus that older versions may not be able to recognize.
- Change the Password: another major step which you need to take before the malware hampers your system, kindly change your password. Also, turn on the MFA
- Keep an Eye on Suspicious Activity: Drag and drop it into the junk folder or right-click and delete.
Do any one of these, and it will ensure that this particular email, along with it, no longer appears inside your inbox. Moreover, after a preset time (30 Days). This will be permanently removed on its own. if you believe that this was a mistake or want to perform hard deletion of suspicious mail manually, go to the junk/delete folder/bin on the email platform you are using and perform the required steps.
Best Practices to Protect Yourself from Suspicious Attachments
An informed workspace environment is the best prevention tactic for any organization. So hold regular webinars, and knowledge sessions, and keep the staff up to date with the latest email attachment attacks.
To ensure that your data remains accessible after you check suspicious email attachments, you need to keep a secure backup of all email conversations. Build a separate isolated and, if possible, offline environment. Also, make sure that you schedule the backup regularly. Only open attachments from the people you expect at the time you expect.
Keep an eye on the messaging, look for red flags, and make a logical decision instead of an emotional one. Don’t register your email addresses on shady websites; use temporary mail or other online tools instead.
Additionally, the best practice you can do is simply choose the best email forensic solution to completely check email properties in one place. MailXaminer is the one true utility that can perform this job most simply. It contains all sorts of media filters to identify and segregate email attachments by type correctly.
Steps to Analyze the Suspicious Email Attachments
Step 1. Launch the software and create a case to check unsolicited email attachments.
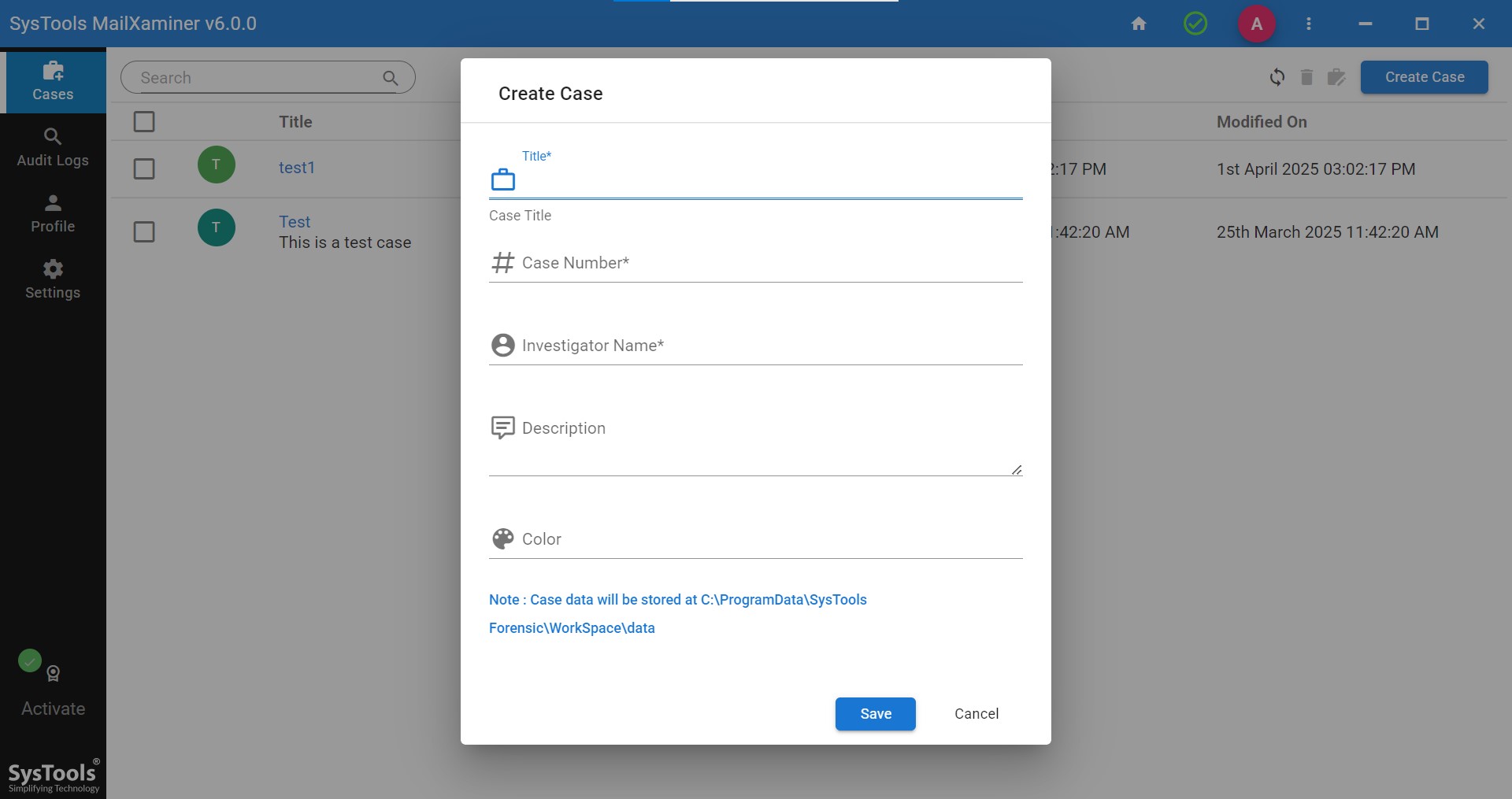
Step 2. After the case is created, add suspicious emails as evidence into the software.
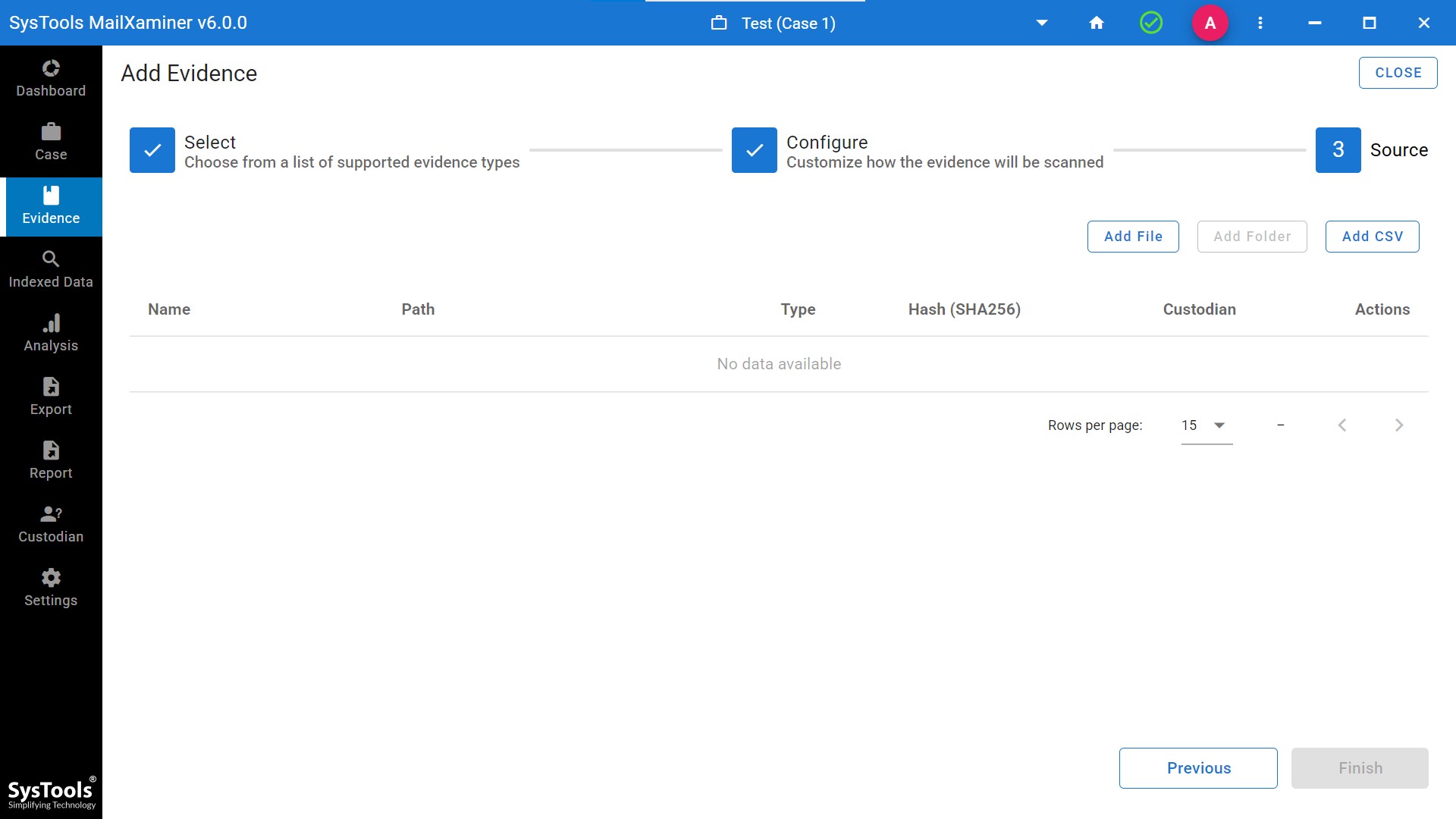
Step 3. Afterthat, the software dashboard will show you all the files added as evidence into to software.
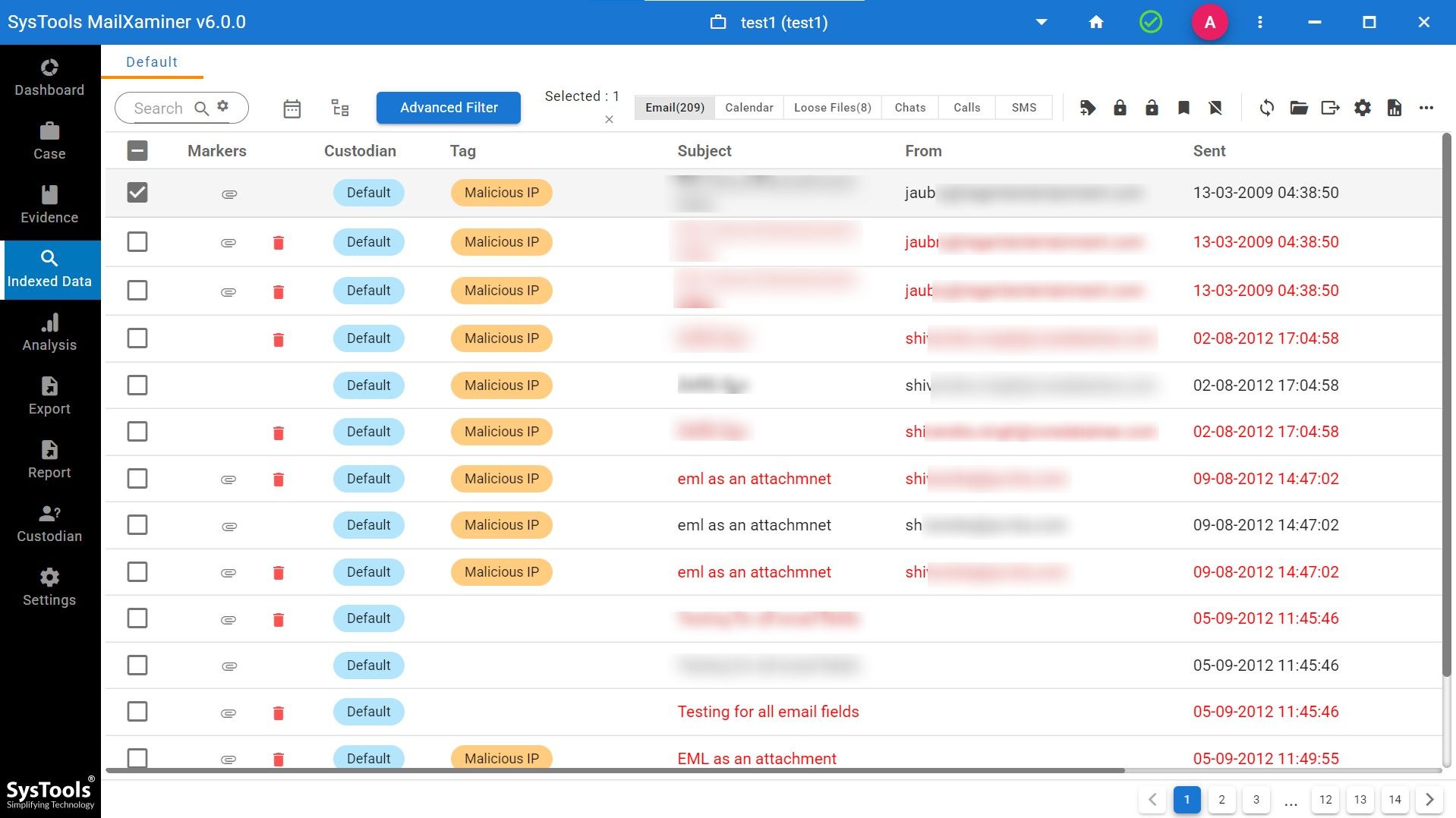
Step 4. Now check your added emails with all details available like sender’s address, time, date, size and whether the email is attached with attachments or not. Not only does this software dashboard specifically mention the tag of whether an attachment is malicious or not.
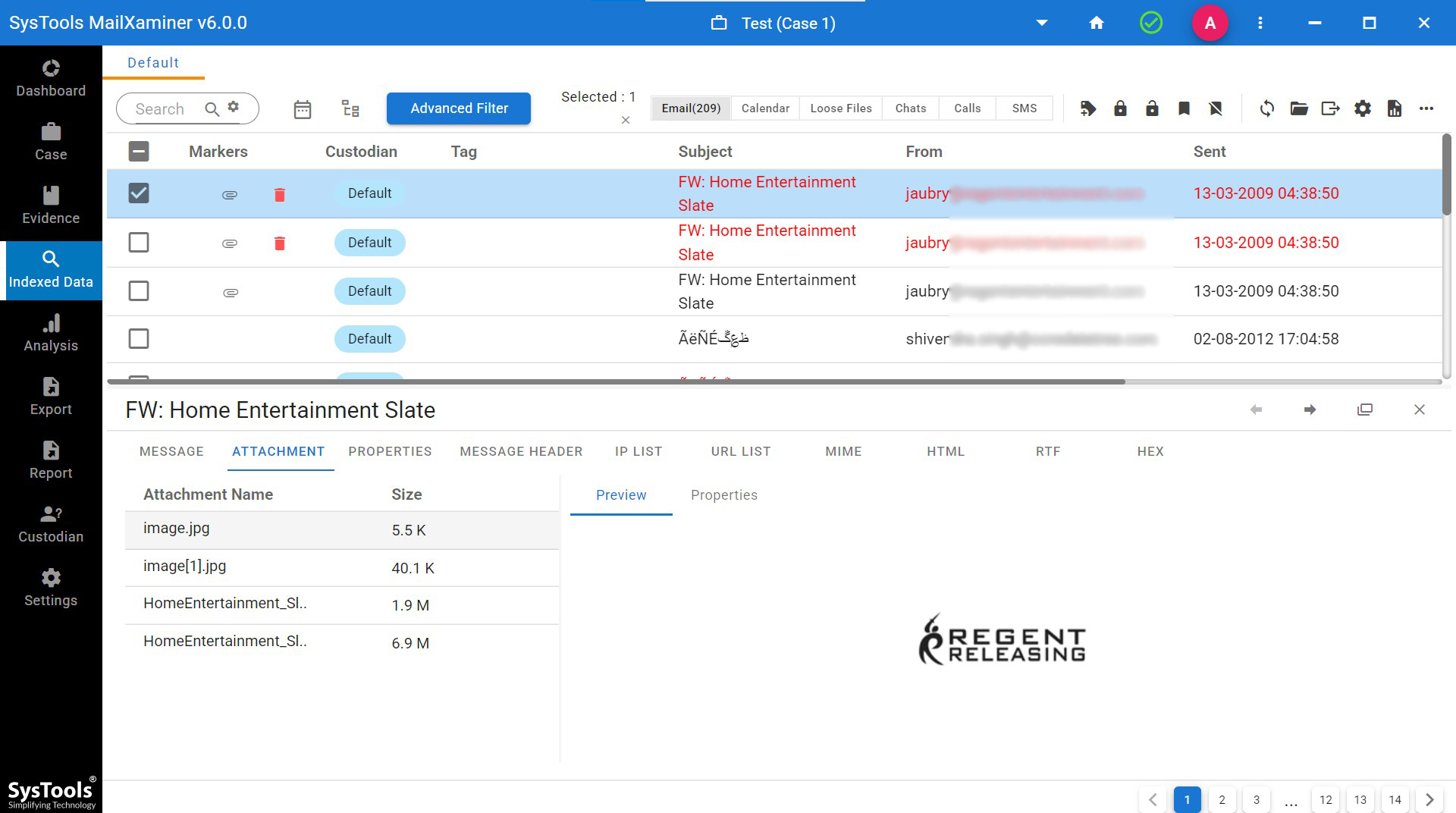
Step 5. Your email attachment name, size, and preview options will show what attachments consist of.
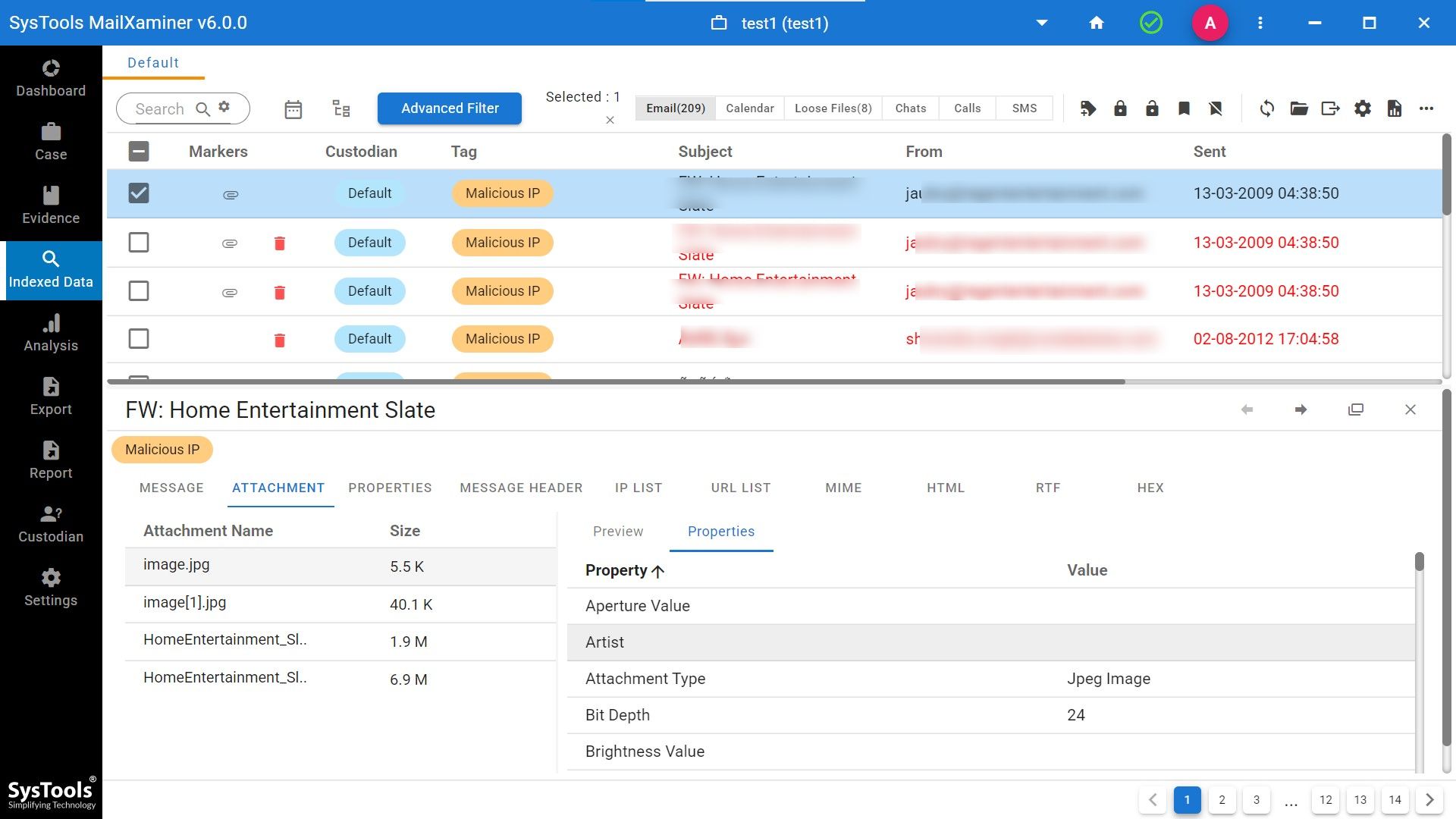
Step 6. This attachment properties option is also visible, and you will see the complete report about the attachments.
Step 7. Lastly, choose the suspicious email attachments and export the full report with multiple export options available.
You can use a variety of search options to filter out the common terminology used in emails and perform OCR Analysis to reveal the text information inside image attachments.
The tool can digest attachments while it’s processing the mail content. There you can put in the suspicious zip files, PDFs, and other data found as attachments. With over 80+ acceptable source types the tool is ready for any scenario to assist you in your digital investigation of suspicious email attachments.
Conclusion
Now you are well-versed on how to check suspicious email attachments in any form and also aware on the procedure to deal with a fake email attachment. By understanding the risks involved and taking all the safety precautions, no malicious attachment will ever harm your system. Moreover, forensics analysts can do an in-depth analysis on patterns used by the attackers and of the attachments themselves with the email forensic utility we mentioned earlier.

