Top Digital Forensic Investigation Techniques – Complete 2025 Guide
Digital Forensic Investigation Techniques is the backbone of modern cybersecurity. Digital forensic investigations empower experts to uncover hidden and critical evidence essential for solving cybercrimes and legal disputes. Today, digital forensics plays a vital role in finding evidence, especially in analyzing various types of email threats that solve cybercrimes. This practice by experts ensures that justice is served with the use of advanced digital forensic investigation techniques.
Table of Contents
- What is Digital Forensics?
- Why Digital Forensics Investigation of Emails is Important?
- What are the Different Branches of Digital Forensics?
- Complete Process of Digital Forensics Investigations
- What are Digital Forensic Investigation Techniques
- Digital Forensics Tools
- Conclusion
- Frequently Asked Questions
Organizations and law enforcement agencies rely heavily on digital forensic investigation methods to retrieve, analyze, and present evidence in legal cases. There are various specialized tools available, which become important parts in digital investigations in computer forensics, mobile device forensics, and network traffic analysis.
Digital forensics involves various techniques that help, whether it’s investigating cyberattacks, recovering lost data, or tracing unauthorized access. Forensic experts use specialized techniques and tools to extract digital evidence while ensuring data integrity.
These techniques provide deep knowledge of digital crimes and security incidents. So, before moving forward into techniques, let’s first understand what Digital forensics is.
What is Digital Forensics?
Digital forensics is a centralized branch of forensics science, which primarily focuses on identifying, acquiring, analyzing, and reporting of electronic evidence. This process of investigating digital data collected from multiple digital sources. It is a critical discipline in cybersecurity, criminal investigations, and corporate security.
During the investigation process, a step-by-step procedure is followed, and the collected data is preserved and analyzed by a cybercrime investigator.
Digital forensics aims to reconstruct the sequence of events that took place at the crime scene. Also, digital data and media can be recovered from mobile phones, laptops, hard disks, pen drives, floppy disks, and many more. Forensic recovery of evidence makes the digital forensic investigations more efficient.
Further to this, it can be used as a potential source of evidence in a court of law. As cybercrime investigators are digital forensics experts, they carry out the investigation process and perform analysis of digital data. Moreover, they ensure the authenticity of evidence is maintained.
In this blog, we will focus on the different approaches to investigating the gathered digital evidence during the process of digital forensics.
Why Digital Forensics Investigation of Emails is Important?
In simpler terms, digital forensics is the art of investigating what happened on a device—whether it’s a computer, smartphone, cloud service, or even IoT devices—by analyzing the digital footprint left behind. This process often involves recovering deleted files, analyzing file metadata, tracking digital activities, and understanding how data was accessed, altered, or deleted.
During a digital forensics investigation, a thorough analysis of email is essential since most of the digital evidence can be found in email. Through email analysis, an investigator can dig out who the culprit is and other illegal information stored in the email.
Technically speaking, you will be able to easily trace the criminal by looking at the email properties found in the analysis of the email. In addition, with the help of the MIME header analyzer, you can discover non-text attachments as well as hidden evidence.
Moreover, with the investigation of emails, you, as an investigator, can view the recovered emails to know if someone has tried to destroy any evidence or made changes in a particular email. Above all, you can learn about the detailed path of emails and also trace email sender IP address.
And by the way, when forensics investigators have the support of investigation techniques and tools, the task of analyzing emails becomes easier.
What are the Different Branches of Digital Forensics?
Digital forensics is a broad field in itself that consists of several specialized branches. These branches focused on different types of digital evidence techniques. Let’s explore the primary branches of digital forensics and how each contributes to solving modern cybercrime and security incidents.
Computer Forensics Investigations
It is a known branch in digital forensics which mainly focuses on retrieving, analyzing data from computers, servers, and storage devices. These include hard drives, SSDs, flash drives, and other local storage systems.
Computer forensics experts examine file systems, recover deleted files, analyze system logs, and investigate operating system behaviors to know the truth behind the evidence.
The scope of computer forensics has expanded over the years with the increasing use of cloud storage, virtual machines, and remote working. Investigators must now also deal with system images and the forensic examination of cloud servers and storage platforms.
Mobile Device Forensics
It has become a critical branch of digital forensics with the proliferation of smartphones. Mobile devices—smartphones, tablets, and even wearables—store vast amounts of personal data, including communications, location history, photos, documents, and application data.
This involves extracting and analyzing data from these devices, including SMS and messaging app data, call logs, GPS locations to find location from a photo, and app history.
Network Forensics Analysis
This involves monitoring, recording, and analyzing network traffic to uncover evidence of criminal activity or security breaches. It is used to investigate attacks such as Denial-of-Service (DoS), unauthorized data transfers, and intrusions into networked systems.
Network forensics experts focus on capturing packets, analyzing network logs, and identifying anomalies or suspicious activities within a network. Investigators may also reconstruct network events from log files and packets to identify the source of an attack or breach that offers a deep analysis of how a cyber crime has been carried out.
Cloud Forensics Investigations
As more data is stored in the cloud, cloud forensics has become an increasingly vital branch. This field deals with the complexities of retrieving evidence from cloud-based environments like AWS, Google Cloud, and Microsoft Azure.
Database Forensics
It involves the analysis of databases and database management systems to reveal the evidence of criminal activity or breaches. This is especially relevant in cases where sensitive data, such as financial information, personal records, or trade secrets, has been compromised or altered.
Related content: Read our guide related to ediscovery vs digital forensics.
The Complete Process of Digital Forensics Investigations
The investigation process in digital forensics is a step-by-step procedure carried out meticulously. It ensures that no original evidence is destroyed in the process while maintaining the chain of custody. There are sequential steps for the digital forensics investigation procedure that are as follows:
1. Identification- It is the foremost step carried out during any kind of investigation process. It involves the identification of all potential digital sources that are capable of storing digital information, including media. Further, it can be used as a source of evidence. Primarily, it is mandatory to be aware of the devices which can be useful in the investigation procedure.
2. Collection- All the digital devices, which are potential sources of evidence, are removed and properly collected from the crime scene. Collection of all the digital devices, in their true form, is ensured to maintain authenticity.
3. Examination- The Data Collection can be Further Divided into Four Main Types:
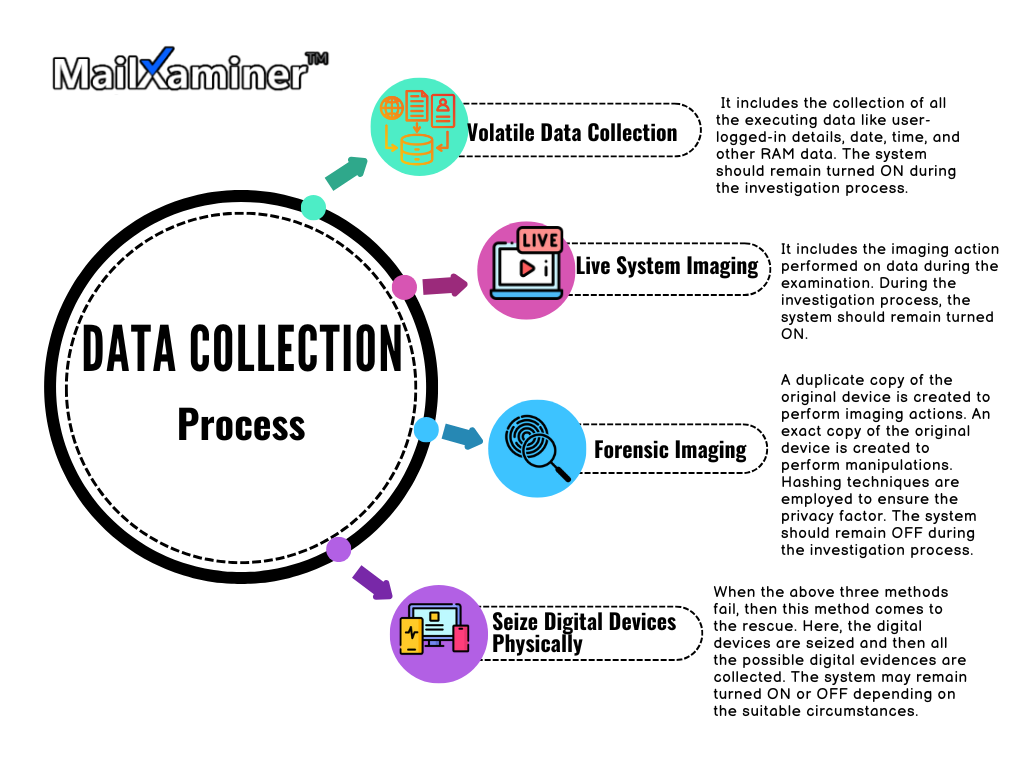
3. Preservation- Preservation is an important step as it is necessary to preserve the integrity of that evidence. It is also important to preserve all the Electronically Stored Information (ESI) that could be obtained from the crime scene. This involves creating forensic copies of the data, also known as disk images. Chain of custody is essential to ensuring the evidence is accepted in court.
4. Analysis- Analysis involves an in-depth examination of all the digital evidence. Proper imaging is performed to ensure that the original evidence does not lose its authenticity. The examination and study of the criminal scenario help the investigator to conclude.
5. Reporting- This is the final step during the investigation process. Reports are a way of presenting all the facts and events systematically linked with the crime. These reports are then presented in the court of law as the source of evidence to solve the crime.
Now let’s come to one of the important sections, what are all the digital forensics techniques that are involved in digital forensics
What are Digital Forensic Investigation Techniques?
Digital forensic investigation techniques are methods used by experts to collect, analyze, and preserve digital evidence. These include disk imaging, email header analysis, deleted file recovery, reverse steganography, timeline reconstruction, and mobile forensics. These techniques ensure legal admissibility and help uncover cybercrimes.
Here are some of the most commonly used digital forensic techniques in investigations today.
Reverse Steganography
This is the type of technique used to uncover the information that has been concealed within other data such as images, audio files, or video files. While steganography is the process of embedding secret information into a file, reverse steganography is the process of extracting and revealing that hidden information.
Disk Imaging
This is the type of foundational technique in digital forensics. refers to creating a bit-for-bit copy of a storage device, such as a hard drive, memory card, or USB stick. This copy (known as a forensic image) preserves every bit of data and ensures that the original evidence remains untouched, making it admissible in court. Imaging is particularly crucial for preserving volatile data (like RAM) that can be lost if the device is powered down.
Network Device Investigation
This investigation involves all the logs maintained by the network devices. This includes routers, firewalls, and switches that are used to investigate the source of an email message. This technique of link analysis in criminal investigation is complex and used only when the logs of servers are not available for some reason.
Sender Mailer Fingerprints
You can find information about the software that manages email files on the server in the Received header field. Similarly, you can identify the software handling email on the client side by checking headers like ‘X-Mailer’. These headers describe applications and their version used by the clients to send the email. This information about the sender’s client’s computer can be used to help investigators create an effective plan.
Time Gap Analysis
Timeline analysis is a technique used to create a chronological sequence of events from digital evidence. It analyzes files, system logs, application logs, and other data sources, investigators can build a timeline of actions that occurred during an event, such as a data breach, cyberattack, or theft.
Mobile Device Forensics
As mobile devices play an increasingly prominent role in digital investigations, mobile device forensics has become a crucial field. Investigators use specific techniques to recover data from smartphones, tablets, and other mobile devices, even if the data has been deleted or the device is locked.
Deleted File Recovery
Deleted file recovery focuses on retrieving files that were deleted intentionally or unintentionally. Even after a file is deleted, parts of it often remain on the device until they are overwritten by new data. Through specialized tools and techniques, investigators can recover these deleted files, which may contain valuable evidence. To aid in the recovery and preservation of digital evidence, a professional Email Investigation Tool is required. MailXaminer proved to be the best software in the market that most Law enforcement agencies depend on to examine emails. It can provide you with the complete recovery of your data.
Digital Forensics Tools
The software enables an investigating officer to perform email analysis with speed, ease, and accuracy. It is integrated with amazing features that help to examine the email file in different preview modes.
Also, investigators can effortlessly implement digital forensic investigation techniques such as email header analysis with the help of this feature-rich tool. Experts have proven that this tool is a smart utility that helps forensic examiners handle and manage their cases smoothly.
It is an efficient digital forensics tool. It helps in analyzing emails providing precise results. Using this, investigators carry out digital forensic processes. It further guides them on how to use this tool efficiently. For your information, this software supports 20+ file formats, as well as supports a wide variety of web-based applications. Certainly, one can rely on this impeccable tool for investigations related to digital forensics.
Closing Thoughts
Typically, the police or other authorities task themselves with apprehending an assailant, and investigators use digital forensics to gather proof. This is necessary for identifying the offender and, more crucially, for bringing charges against them. Digital forensics is crucial, which explains why the area has grown to be quite well-known over time.
Conducting a digital forensics investigation quickly and thoroughly increases the odds of apprehending the hacker and correcting any damages. And, with the right digital forensics investigation techniques and tools, the entire process seems a piece of cake. Thus, here we discussed different techniques and shed some light on the best forensics tool for your reference.
Frequently Asked Questions
Q. What methods are used to examine electronic traces in investigations?
Digital forensic investigators mainly rely on various digital strategies to extract and assess data from electronic devices. This includes creating backup, examining system logs, recovering deleted information, and inspecting metadata. These procedures helps to reconstruct case without hampering the original source.
Q. Which Tool is best for forensic email investigation?
One of the best tools for email forensic investigation is MailXmainer. It supports over 25+ email formats and cloud platforms. It provides you advanced level of analysis of headers and also the IP analysis. Additionally, Law enforcement agencies use this utility for its 100% accuracy results, different analysis features, and user-friendly interface.
Q. What is the first step in a digital forensic investigation?
The first step in any digital forensic investigation is Identification. Investigators identify and locate potential digital evidence sources such as hard drives, mobile devices, cloud storage, and network logs. This step is crucial for defining the scope of the investigation and preserving critical data before it is altered or lost.

