Gmail Email Investigation in Computer Forensics [Information]
Is your Gmail’s inbox loaded with spam emails? Are you scared about losing your sensitive data? Are you a victim of a phishing attack? Burry all these mind-scratching worries! Here, in this blog, we are going to understand the tips and tricks for Gmail email investigation in computer forensics that will help to detect spam emails.
Why Do Hackers Hack Emails?
As we all know, Gmail is one of the primary email communication platforms that is widely used for both personal as well as business level communication. Besides communicating with the end-users, it also allows sending documents, carrying out several types of transactions, and much more. One of the major reasons why users prefer using Gmail is that it is convenient to use anywhere with various digital devices. Users can access their Gmail accounts anywhere via the internet as it is a web-based email client. This also makes it easy for hackers to get access to an email account by finding loopholes and they misuse it for their advantage.
How a Hacker Grabs Crucial Gmail Data?
Email protocols like SMTP, POP3, etc. are secure and encrypted through various security extensions. However, cybercriminals are continuously finding ways to misuse it for illegal purposes. They indulge in these activities by sending spoofing emails, phishing emails, spam emails, etc. Besides, the hacker also tries to get access of the user’s system by propagating malware, worms, viruses, trojan horse, etc. They transfer these malicious programs into the system via emails and links in order to get the confidential information from the victim.
Nowadays, the dependency on the internet has grown way beyond what it was 5-20 years ago, which also gives rise to an increase in cyberattack instances. When we talk about email spoofing, it is a kind of terrorism that threatens a person or property to the level of creating fear and extorting money.
Let’s Check Out a Real-life Case Scenario Mentioned Below:
Poona Auto Ancillaries Pvt. Ltd., Pune Versus Punjab National Bank, HO New Delhi & Others
In 2013, it is one of the largest compensation which has been awarded after a legal verdict of a cybercrime. An IT secretary of Maharashtra, Rajesh Aggarwal ordered PNB to pay Rs 45 lakh to the complainant Manmohan Singh Matharu, MD of Pune-based firm ‘Poona Auto Ancillaries’. This is because Matharu responded to a phishing email after which fraudster had transferred Rs 80.10 lakh from Matharu’s account in PNB. However, the bank was found to be careless to carry out proper security checks against fraud accounts opened which led to defrauding the complainant.
To deal with these types of situations, the government of India also took steps by introducing the Information Technology Act, 2000 which deals with the disputes related to Cybercrimes and electronic crimes.
Under Section 43 of the Information Technology Act, 2000 users can claim compensation and penalty for unauthorized access and damage by introducing any computer virus or malicious software to a computer system and so on.
Before going further on how to recognize email scams during email investigation in computer forensics. Let’s have a glance at the email architecture in the below section.
Email Architecture in Computer Networks
An email never directly goes into the recipient’s mail server from the sender’s mail server. It passes through many servers. Multi-User Agent (MUA) is an email program which first read and compose an email from the sender’s client end. Then, Mail Transfer Agent (MTA) which receives the email from MUA decodes header information of the email. MTA is mainly responsible for the receiving and sending the email. Message Delivery Agent (MDA) receives an email from MTA and finally sends it to the receiver’s MUA. With this, the email message can be seen at the recipient end.
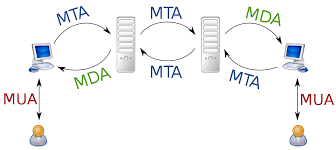
As a result, MTA gives the “Email Header” information which consists of multiple server information, with the IP addresses thereby helping to investigate spam emails in email forensics.
How to Analyze Email Header Information in Gmail Application?
Gmail Email Investigation in Computer Forensics is used to analyze and obtain hidden pieces of evidence by examining the content and source of email messages. It consists of three parts i.e., Envelops, Header, and Body. Among these, “Email Header Information” is one of the most important elements that help in the investigation of cybercrimes.
Why and How to Extract Information from Email Header?
Every email has its own header part, which cannot be seen by the user in normal mode. It is the key to find a spam email in Gmail. One can check the email header, by following these steps on Gmail email application:
- Open the email message
- Click on the down-arrow located next to the reply button
- Select “Show Original” option from the list to view email header.
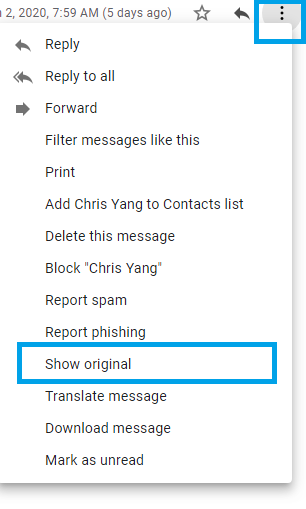
Email header plays a major role in email investigation in computer forensics for tracking the details of an email and its sensitive information. Thus, on the analysis of the email header, one can easily get information about the sender and several networks related components.
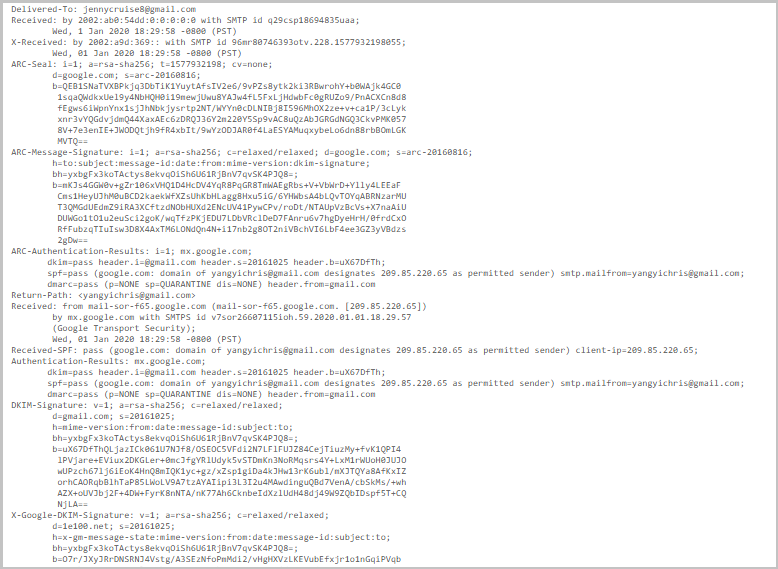
What All Information Can be Obtained by Analyzing Gmail’s Email Header?
Received Lines: Unlike other elements of the email header, “Received” lines cannot be forged. It helps to spot fake Gmail’s email address by displaying the sender’s and receiver’s computer address.
ARC Seal: ARC stands for Authenticated Received Chain. It is an email authentication system that works as an intermediate mail server and it is used to forward an email with original authentication results.
Return-Path: It is an email address specified by the sender. It can also be spoofed if no authentication mechanism is applied.
MIME-Version: MIME is Multipurpose Internet Mail Extensions. It extends the email format to support text and non-text email attachments such as images, audios, videos, etc.
Message-ID: It is a globally unique identifier used for emails. Every email message has a unique Message-ID. It is generated by MTA (Mail Transfer Agent) in a specific format.
DKIM Signatures: These are Domain Keys Identified Mail that confirms the authenticity of the sender by domain name connected with the email. It helps in reducing email spam and email phishing.
Received-SPF: It declares that the email is coming from a domain having some SPF record.
Email header plays a very crucial role in the process of email investigation in computer forensics for Gmail. But it is not that easy to detect as it seems. It needs in-depth knowledge about the components and requires strong skills to analyze the components.
So, are you still facing difficulty in examining the Gmail email header information to detect email spoofing in your Gmail inbox? No need to worry! To make this easy, we recommend you to use a trustworthy advanced Email Examiner Software.
Use Smart Utility to Identify Phishing Email in an Efficient Way
It is advanced software, which efficiently helps forensics users to find out sensitive information from the emails. With the help of this tool, one can easily understand the significance of each parameter individually and can easily detect manipulated emails.
MailXaminer is an all-rounder utility that comes with a result-oriented approach to implement email investigation in computer forensics. It provides a range of facilities to obtain evidence through email messages in a perfect way.
What are the Highlighted Features?
Some of the remarkable features of the software are as follows:
- Compatible with 20+ email file formats like PST, OST, MSG, MBOX, EDB, etc.
- Supports 750+ MIME (Multipurpose Internet Mail Extension) types.
- Capable to examine email data of 80+ Email Client applications.
- Email analysis of web-based as well as desktop-based email services.
- Supports various format image files such as DD, EO1, ZIP, DMG, LEF.
- Examine emails & attachments in different preview modes.
- Video analysis mode to analyze video attachments having obscene content.
- OCR technique is available which allows the software to search suspected keywords in an email’s attachments as well.
- “Bookmark” and “Tagging” option allows marking important emails to get back to them later.
- Export and save case reports in different file formats like PDF, HTML, and CSV.
- View and filter out emails with hash values SHA1, MD5, SHA256.
Let’s Conclude
Most of the users fail to carry out the basic steps of analyzing email headers for Gmail email investigation in computer forensics. By reading this blog, it will get easy for the users to identify spoofed emails. Furthermore, users can take the help of the professional tool that will help them to fetch in-depth information of the Gmail’s email header without any hassle.

