MailEnable Email Server Forensics
MailEnable primarily developed for Microsoft Windows Platform, is a powerful hosted messaging platform. Focused over email server hosting, the client is known for its stability, flexibility, and prime focused features. It provisions unified management interface, enabling administrators to take a proficient system overview. This eases out the investigator’s work in examining the whole server administration and working. The mail server keeps up with the common protocols such as; POP, IMAP, and SMTP to exchange emails and also offers webmail services.
Investigations demand knowledge about how secure the mail server was and its open vulnerabilities before further examining the email artifacts. MailEnable however, scores its way up towards making things secure by provisioning IP blocking functions, relay, and filter properties. Several authentication methods and third party anti-spam utilities such as spam assassin can be deployed easily with the server configuration. MailEnable also features support for other protocols such as; MAPI connectivity, HTTPMail, Mobile device Sync, LDAP Service, etc. for other license variants of the server deployment.
Understanding MailEnable Storage Mechanism

MailEnable offers an Admin module which enables a bird’s eye view of the Messaging management, Server Configuration, & current status. The server maintains Post Offices which consist of the domains, user mailboxes, groups, and lists. Information useful during investigation could be unveiled after analyzing the mailboxes and the logs. Irrespective of the server availability, if we have an acquired logical image of the server deployment, then the artifacts could be found residing in the file structure.
The server stores most of the information at the installation location: “root: \Program Files\Mail Enable”. It consists of the individual post offices deployed under the server which requires further recursion to unveil information. Each of the domains maintains a MAILROOT directory which consists of the personal mailboxes created under the domain. Mails originated via Webmail or other email clients are synchronized at the server side simultaneously, as soon as any message is sent/ received or deleted.
File Extensions
MailEnable Server Forensics begins with understanding its configuration and working, but primarily the data file in which it stores data should be given the top priority while investigating. MailEnable Server maintains .MAI file format to store email messages and maintains individual message storage in singular files. Outbound, Incoming or Draft folders store the email messages separately, thus easing out collecting information by navigating to specific folders. Contacts, Calendars, Journals, etc., are stored in a way similar to that of the emails, and in the commonly utilized file formats. DAT and XML Files also maintain the user mailbox or folder information respectively.
Exploring Email Server Backups
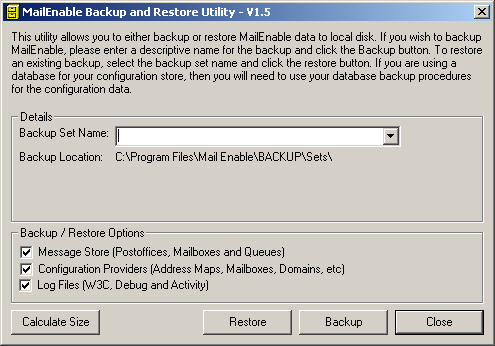
Like every mail server, MailEnable also offers a complete Post office backup of the domain. It gets updated manually by the user defined interval and is quite useful in case of server failure or malicious purge of information. The following snapshot from MailEnable Server’s Backup and Restore utility is shown where the user backs his Message Store, Configuration Files and Log Files. Which completely sums up the whole information to be used while restoring the server after an attack.
Usually the hackers or crackers test the server functionality in a controlled environment and try to attack the machine using vivid mechanism such as; DDOS, Trojan, or Malware. As soon as the server crashes, hackers debug the point of failure and use the knowledge to deploy applications that does so. A compromised server image kept chained and preserved by the custodian requires re-affirmation of the residual information collected from the server and the preserved backups.
Most of the phases in an investigation are reshaped by analyzing mail server backups as; often email evidence are tampered to cover traces. MailEnable’s logging ensures that the data could be tallied to figure out what’s right and what’s wrong. Further securing the information organizes & maintains logging as per the protocols utilized by the users.
Conclusion
Forensic analysis of MailEnable email server requires complete knowledge about the information storage mechanism followed by the server. Server side examination becomes easy due to MailEnable’s distinguished and easy to manage architecture. The server side email artifacts consist huge amount of information to be revealed and analyzed which gets stored in .MAI File format which can be analyzed using email forensic utility such as MailXaminer. Every email gets stored in a separate MAI file which requires an email examination tool to comprehend the message information. If clients using MailEnable server use webmail as their email client, then the client machine plays no role other than browser logs to investigate. In that context server examination should be preferred to unveil artifacts. Further, if the suspect had a desktop based email client configured, then the data file should be inspected thoroughly.