Raw Image Digital Forensics – Fight Crimes, Unravel Incidents
User-Scenario: Mr. John Thomas, a digital forensic examiner is working with a forensic investigation team. He was called to examine a Cybercrime scene, in which he extracts several images of suspect’s digital devices containing raw data. As a forensic investigation expert, he needs to do raw image digital forensics, so he started analyzing all the files to fetch evidence with the help of advanced forensics tools. He also finds deleted data, missing file fragments from the file using the forensic software.
We have mentioned a scenario above on how a forensic investigator successfully finds out evidential facts from suspected raw data by using MailXaminer Email Examiner Software. In this blog, we’re going to focus on raw image file forensics, its types, and proper steps to analyze different image files using Email Forensics Software. Moreover, its advanced features are also here.
What is Forensic Image Analysis?
Whenever an investigator needs to investigate any digital device like – a computer, mobile, etc., then one needs to start the process with documentation of the suspected device. For the documentation, they create a 100% identical copy of the suspect’s device by following some strict set of procedural rules, which we call “Imaging”.
Investigators may use several ways to create a forensic copy of the digital device. During the imaging process, forensic examiners need to remember one thing which is common in all imaging processes. It’s that it must be write-protected. For this, they usually involve the “Write-Blocker” in the process. Write-Blocker is a device that allows investigators to read the device during forensic image analysis, but they cannot edit or modify the things. It is not legal to modify or change the content in a suspect’s data during the investigation.
Forensic Image File Types
There are basically two types of forensic images that an investigator creates during the raw image digital forensics process, i.e. Physical Image, and Logical Image.
(A) Physical Forensic Image
A physical image is an identical copy of the content of a digital device, with another name as “BitstreamCopy”. It consists of a bit-by-bit copy of all the areas within the storage device and also includes the unallocated space area of the device. This kind of image also provides data recovery that is not possible for the normal copy or cloning of the file.
(B) Logical Forensic Image
A logical image is normally a file system level image. When somehow, investigators fail to create the physical image, then they create a logical image. It helps in imaging a certain folder (like- a user directory, user mailbox, etc.) within the file system. It is not able to capture any of the unallocated data within the file. Logical image creation in raw image digital forensics is a way to capture data within the folder, and nothing more.
Note: There is no way to recover deleted data during the Logical Imaging. In raw image file forensics, when it is suspected that users might delete the data, investigators always prefer to create the Physical Image of the device.
Forensic Image File Formats
E01 –
Encase Evidence image file format, which is most commonly used in the imaging process. It creates a physical Bitstream or copy of the file with enriched metadata. The metadata includes Notes, Checksums, Case information, and the hash value of the file. E01 file forensics is better than other image file formats because it provides the option for compression and password protection.
DD –
It generally creates a bit-of-bit copy of the raw data file. The advantage with the .dd raw format image files is that they contain unmodified data of the source, and nothing else. These files are not stored in any of the metadata like – using software/hardware, destination and source details, hash values, etc.
LEF (l01) –
Encase Logical Evidence files (.l01) are usually created by the most efficient Encase forensic software. The LX01 file format in digital forensics is used to create an exact copy of the storage device without manipulating the original data. It maintains the integrity and consistency of the suspected data.
ZIP –
It is an archival forensic image file format that supports lossless data compression without losing the originality of the data. In other words, ZIP is a collection of one or more files and folders that are that stay into a single file in compressed form. It is easy to share and transport in the compressed form during the raw image digital forensics process.
DMG –
DMG files are disk image files with the origin of Apple Mac OS X. It is the digital reconstruction of the physical disk image file. DMG is the format of image files that create files with the extension .dmg. Users can use this to store software installers in a compressed form instead of a complete physical disc.
Raw Image Format Digital Forensics
One of the best Digital Forensic tools is mentioned in this article which provides advanced functionalities for the raw image digital forensics investigation process. Most of the corporate investigation agencies, law firms, and law enforcement agencies are using this raw image file forensics software to handle digital crime investigations. It provides an automated solution to non-forensic investigators to easily find evidence from the files during forensic image analysis.
Software Features for Raw Image Digital Forensics
- Access files from multiple sources.
- Analyze large-sized information case files.
- The fast process to access and examine all data.
- Easy recovery of deleted files, hidden system files, disc slacks, and unallocated clusters.
- Automated structure to investigate complex tasks.
- Generate detailed reports during the process.
- Supports 20+ file formats for examination.
Forensic Image Analysis Using Forensic Software
With the help of this forensic tool, experts can easily examine email files having different file formats. The software enhances the raw format image document support such as E01, LEF, DD, ZIP, and DMG. In raw image digital forensics, users can investigate these files and extract out the evidence from the files by using advanced features provided by the software.
Follow these simple steps to analyze different kinds of image files using forensic software:
Step-1. To start the examination process, add the file for scanning into the software. For this, click on the Add New Evidence button.
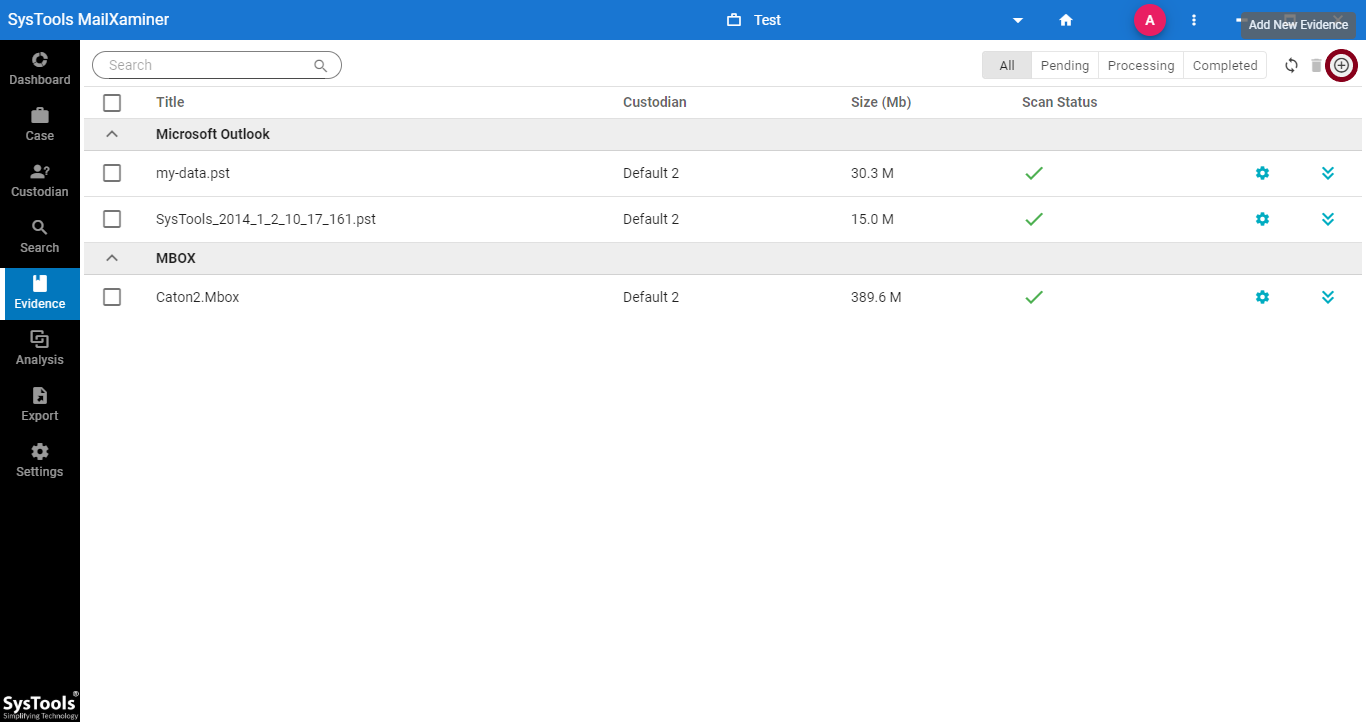
Step-2. An Add Evidence pop-up window will open. The tool supports various image file formats such as DD, DMG, E01, LEF, and ZIP. Now, select file type under the Image tab and add the corresponding file.
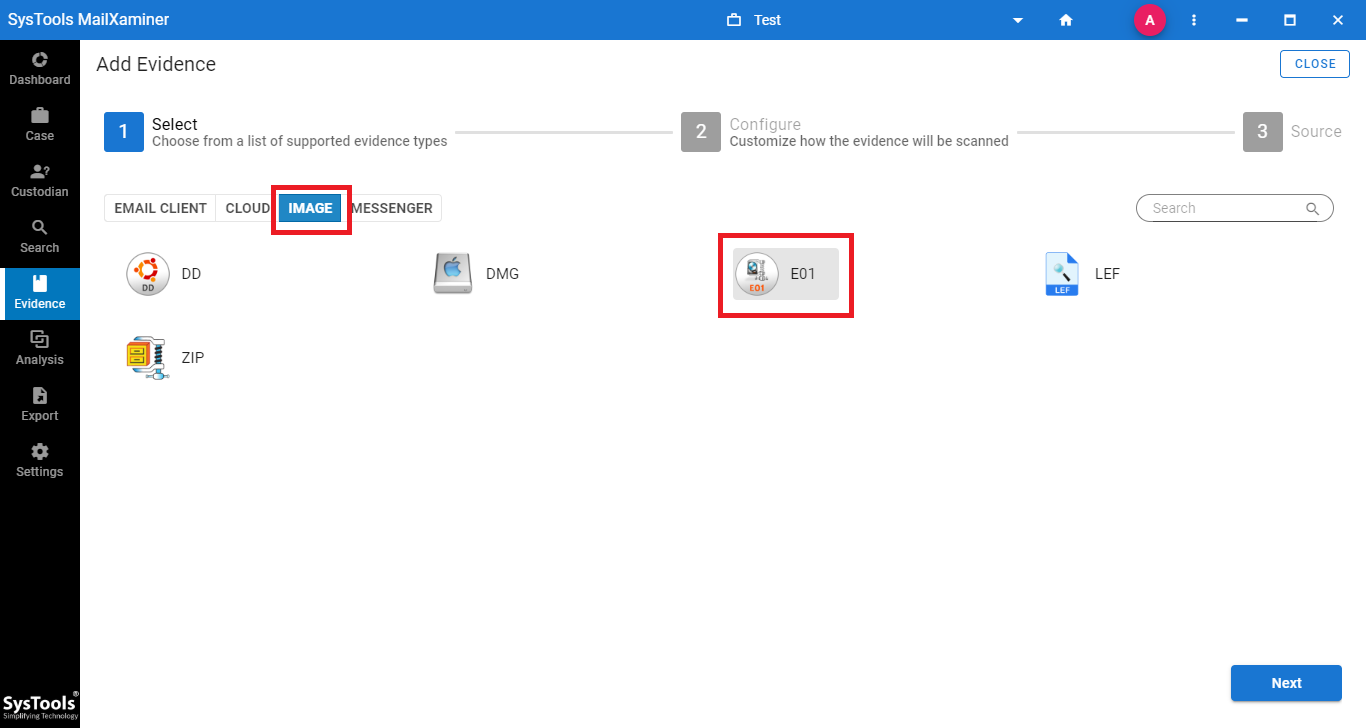
Step-3. Before adding the file by clicking on the Add File button, just save the required settings. So, mark the checkbox corresponding to Only Loose Files option under the General Settings section and click Next.
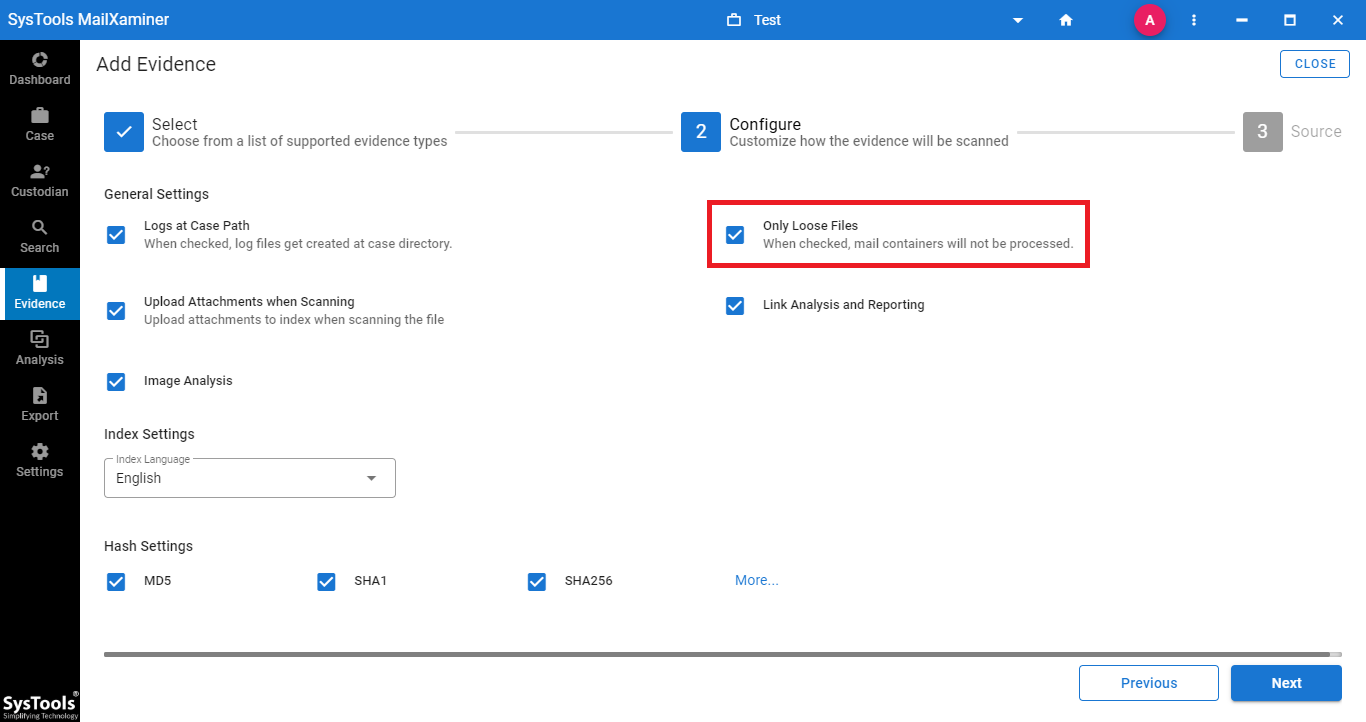
Step-4. After successfully adding files into the software, the screen will show the entire data file details stored in the scanned raw image data file. Now, investigators can perform required operations into the email files for investigation. By right-clicking on email, it will provide many options as shown below.
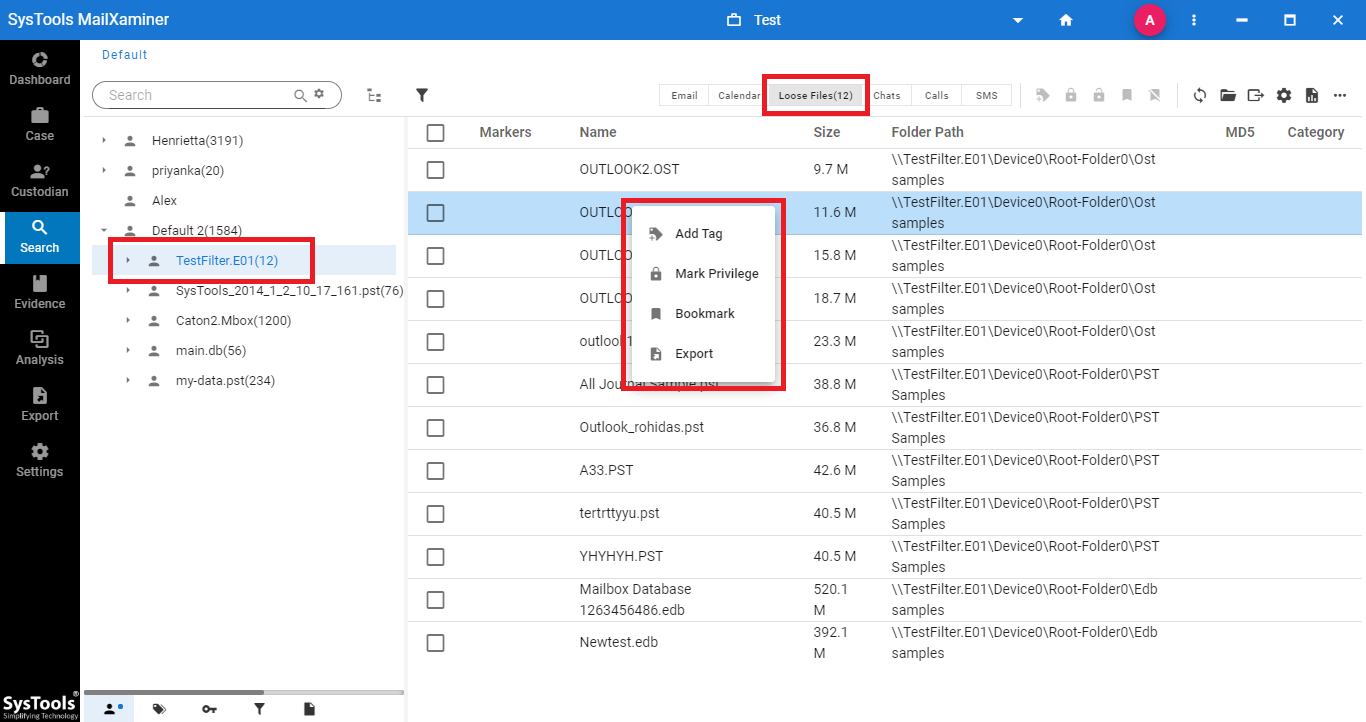
During the forensic image analysis, users can preview the email with different views, mark or remove email as a privilege for future purposes. The export option is also available to export the required data in different file formats, bookmark option to categorize specific files, etc.
Final Words
In this write-up, our aim is to make users aware of raw image digital forensics practices & how to analyze these raw format image files. The improper creation & analysis of a forensic image might create disastrous consequences during the court proceeding. So, with this point, investigators should use trusted and reliable software for the raw image file forensics process.

