What is Timeline Analysis in Digital Forensics & How to Perform It?
Till now we have discussed so many digital forensic investigation techniques. Timeline analysis is another significant process of reconstructing and analyzing chronological events. These events can be analyzed within a digital system to reveal security incidents, unauthorized access, malware, emails, suspicious attachments, or any such activities.
This method tracks down malicious activities in a digital environment only. Since this timeline analysis method was added in digital forensics, it has started playing a crucial role in forensic investigations by providing a structured view of digital events. This helps experts determine what happened when it happened, and who was responsible.
However, while using timeline analysis, investigators mainly use various purposes in the investigation, which mainly involve collecting information within a particular time frame. This helps in identifying the key events that may indicate an intrusion, suspect activity, unauthorized access, or data exfiltration.
Let us discuss timeline analysis in detail and understand how, while facing the current digital forensics challenge, this key aspect helps in digital forensics investigations. Let’s start understanding more about the timeline investigation method and how to make this practice more advanced.
What is Timeline Analysis & Why Does it Matter in Digital Investigations?
The word timeline indicates displaying a list of events in a particular order. Timeline analysis is mainly used for various purposes in the investigation, which mainly involves collecting information within a particular time frame. It is a great technique to determine the activity that occurred on a system at a certain time. It helps to make inferences very fast and in an easy manner.
Normal timeline analysis for computer forensic investigation can be performed on different types of contexts, like text timeline, number timeline, graphical timeline, etc. Each timeline model provides different views of the data accordingly. Through the timeline analysis, an analyst can easily find out when a particular event or transaction happened. It also helps to figure out the other events that took place during the same time interval, along with their interconnection to one another.
While performing digital evidence collection, investigators mainly use this technique to answer questions related to the date and time. Every system that is involved in digital work generates certain logs that track the attention of users’ actions, system processes, and interactions with files. These files or logs play an important role in the proper tagging and labeling of the collection of digital forensics evidence.
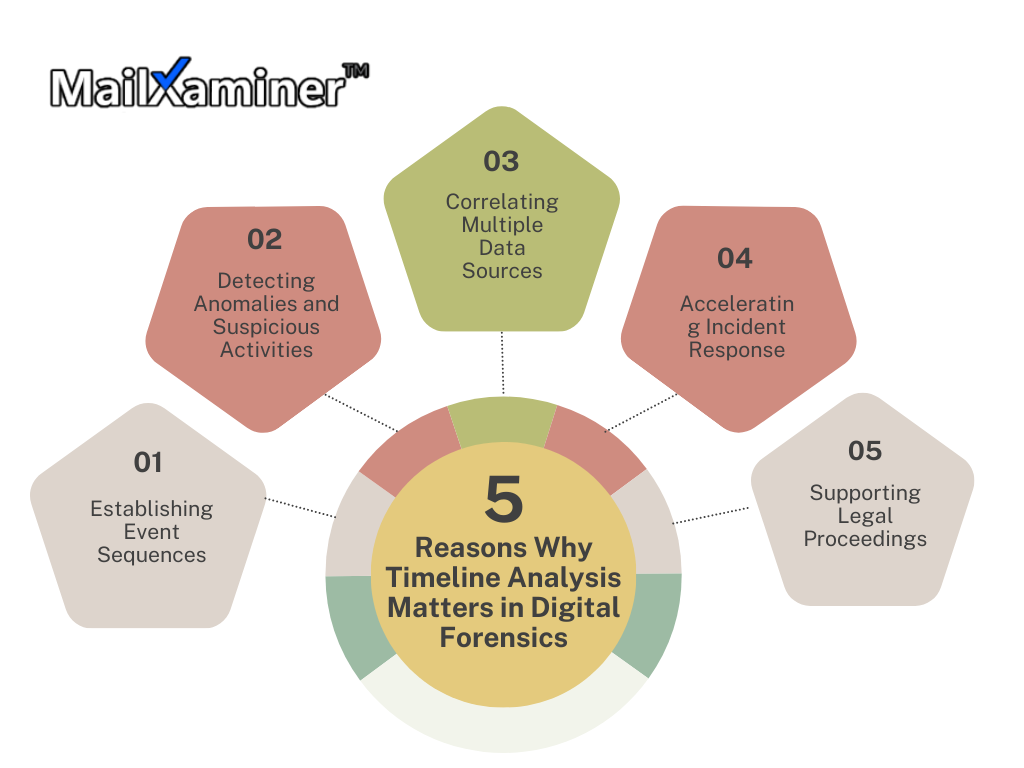
What are the Types of Events Tracked in a Forensic Timeline?
This forensic timeline analysis tracks various events to reconstruct digital activities. These event types include:
- File system events- While performing timeline investigations in search of evidence, file systems track file creations, modifications, deletions, and access timestamps. These details help if the file helps investigators in message-ID forensics.
- Network Activities- This is a type of event that tracks logging network link analysis of traffic data transfers, remote access connections, and suspicious communication attempts.
- System Changes- This type of tracking involves the software installations, updates, patches, and configuration modifications. This helps in tracking the system’s alterations.
- User Activities- With the help of this type of analysis of evidence, through records of user logins, failed attempts, account lockouts, and credential changes, to identify unauthorized access attempts.
These are some of the major events that help investigation experts establish a comprehensive digital timeline. This makes it easier to detect malware in emails and reconstruct security incidents.
Timeline analysis in digital forensics gives clear information through the specific year, month, and date views. The main purpose of using it for investigation is to obtain a graphical view of the transaction. Hence, it makes it easy for the examiners to evaluate and make decisions based on timeline analysis.
Now let’s understand how to use this feature:
How to Conduct a Timeline Investigation Technique to Investigate the Cases?
This is the helpful content for the examiner if this method performs accurately. So it is better to avoid errors and look for the best Email Forensics Software. While using this for timeline investigations, you will only get accurate data with the total number of emails involved, but also get the exact time of emails exchanged.
For easy understanding you will get the easiest graphical representations of the data of the specific date filter you have selected. Date filter makes the task simpler and less time-consuming. Simply just filter the time and analyze the exchange of the emails for examinations.
Using the timeline analysis software MailXaminer feature, a forensic investigator or examiner can view email conversation details between the Sender and Receiver according to specific Year, Month, and Date.
Let us know the steps and how the software helps in performing timeline analysis in digital forensics.
Steps to Perform Timeline Analysis in Digital Forensics Using an Indigenous Tool
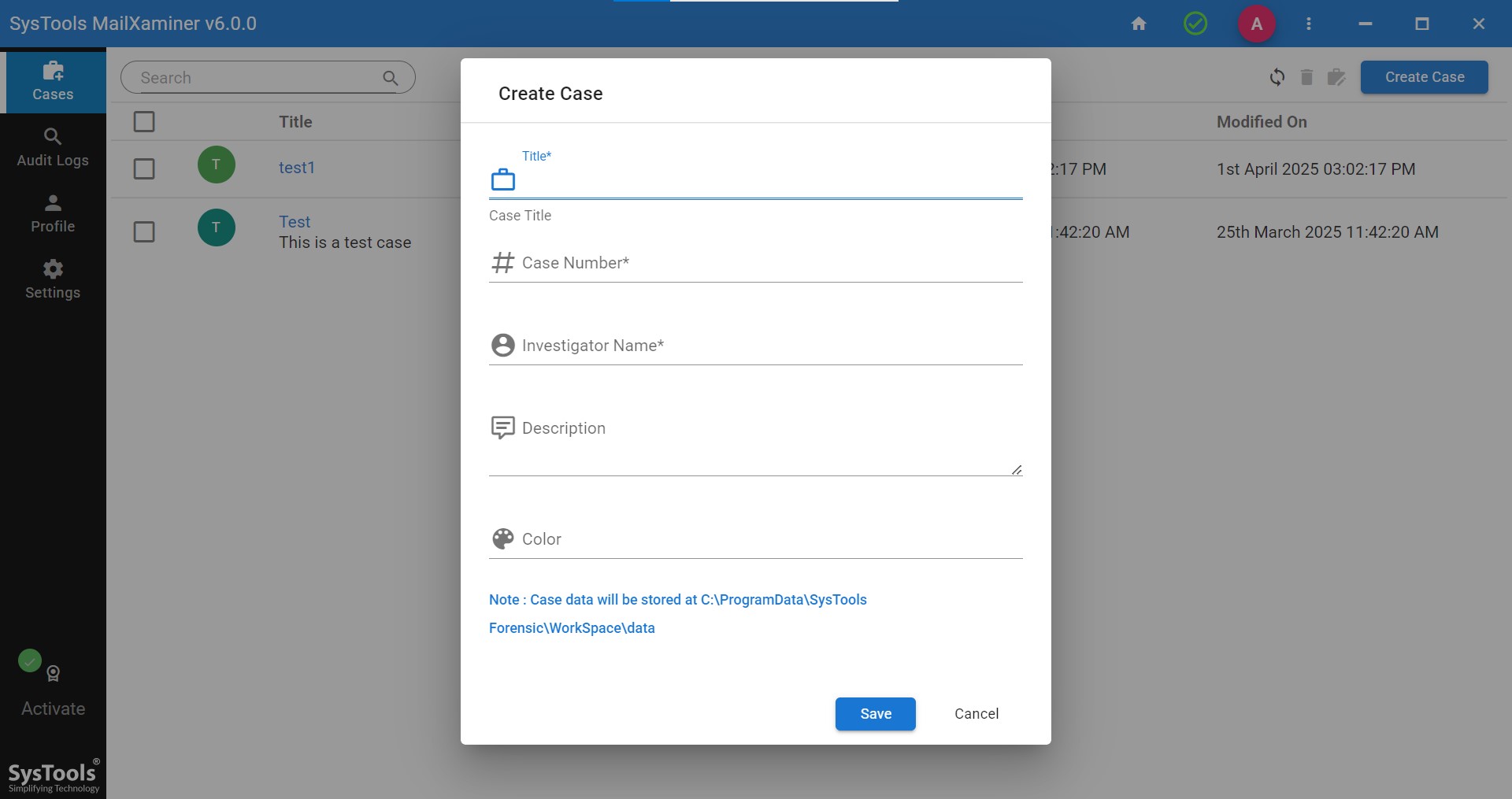
Step 1. Set up the software in the system and create a new case.
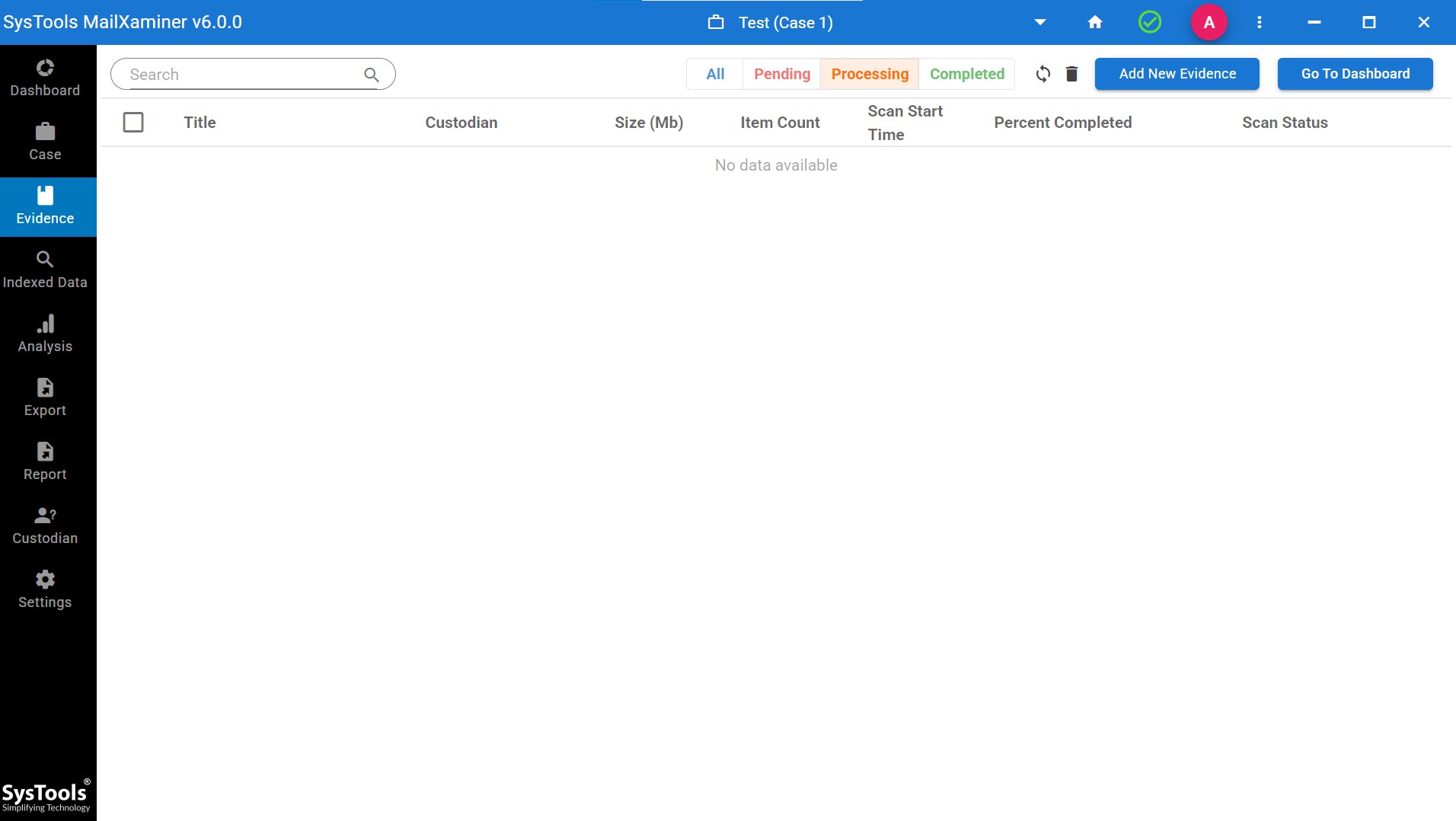
Step 2. Now, add the file as evidence to analyze the emails.
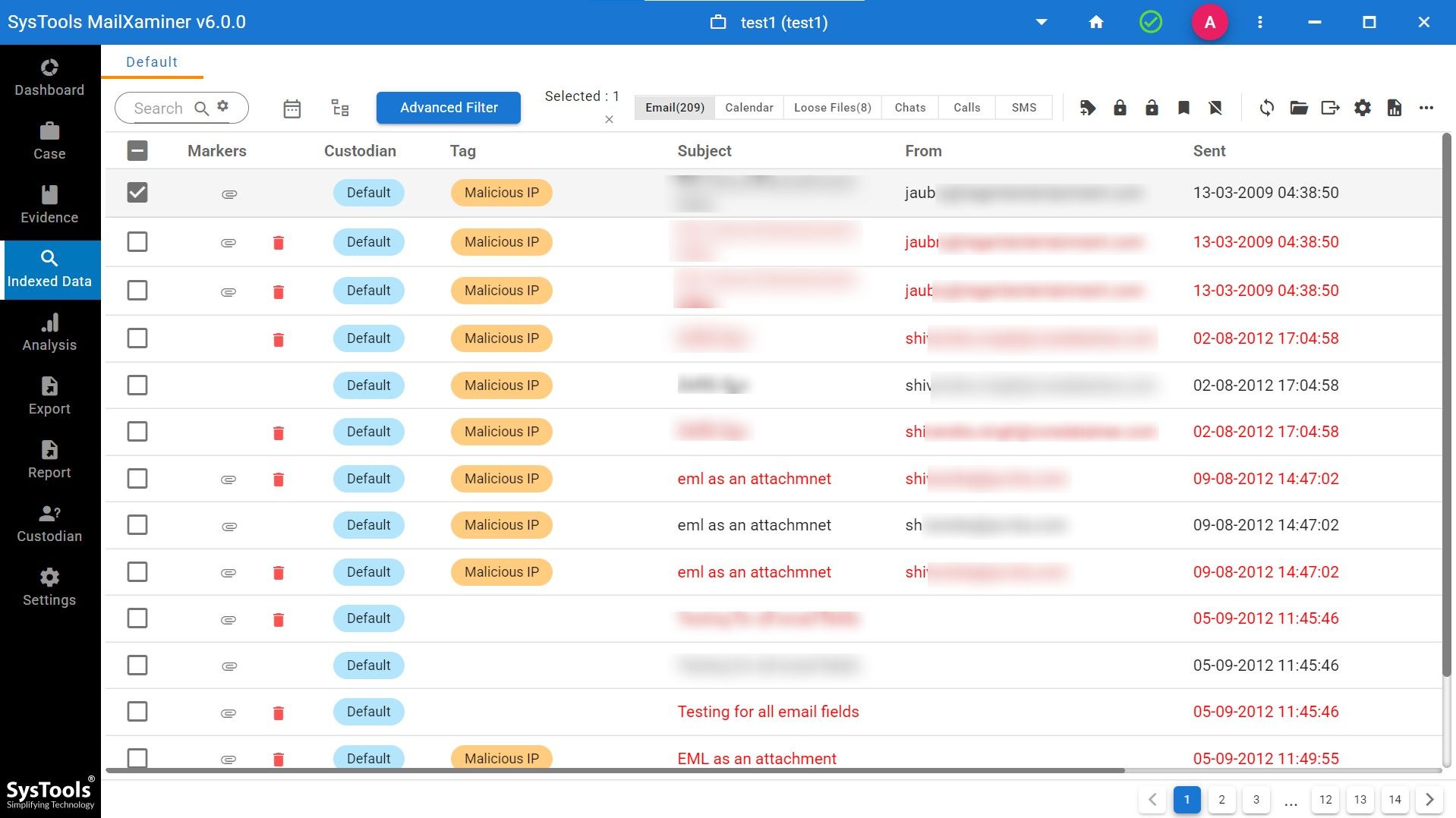
Step 3. After adding the file, the software will provide you with the complete indexed data of all the emails.
Step 4. Not only this, you will be provided with different analysis options. Timeline analysis is one of them.
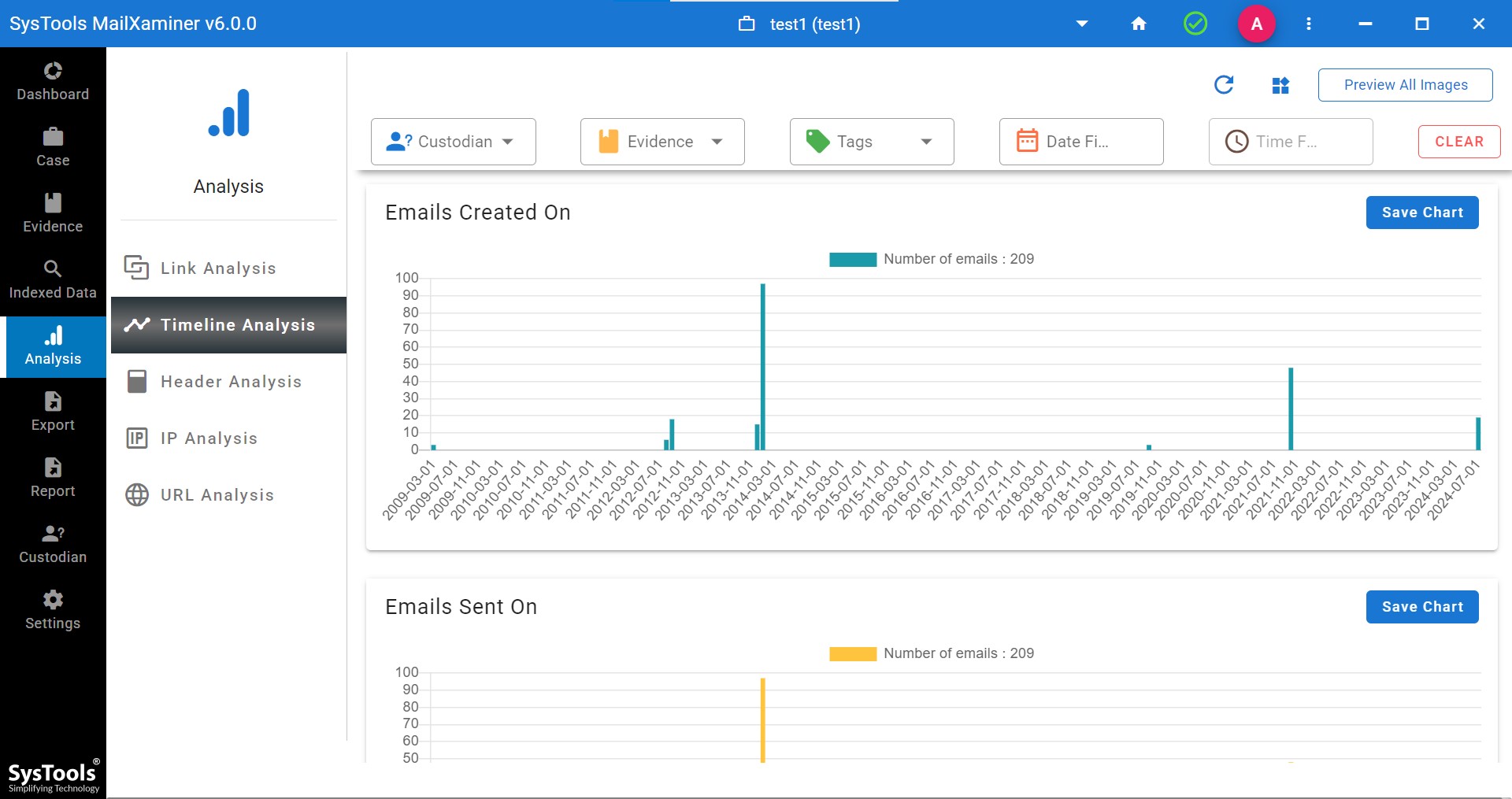
Step 5. Users can view and analyze the email data exchange between the selected date, month, and year.
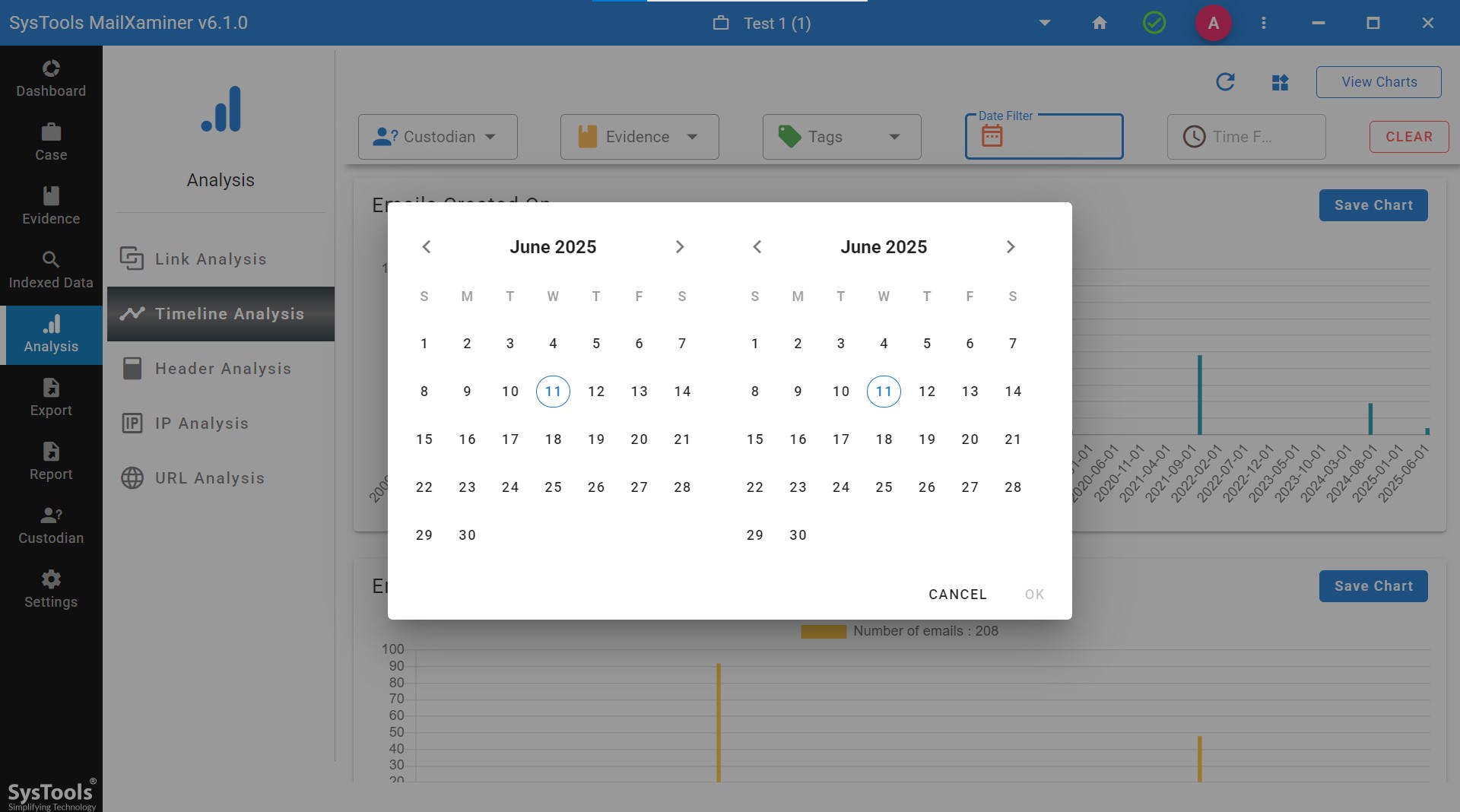
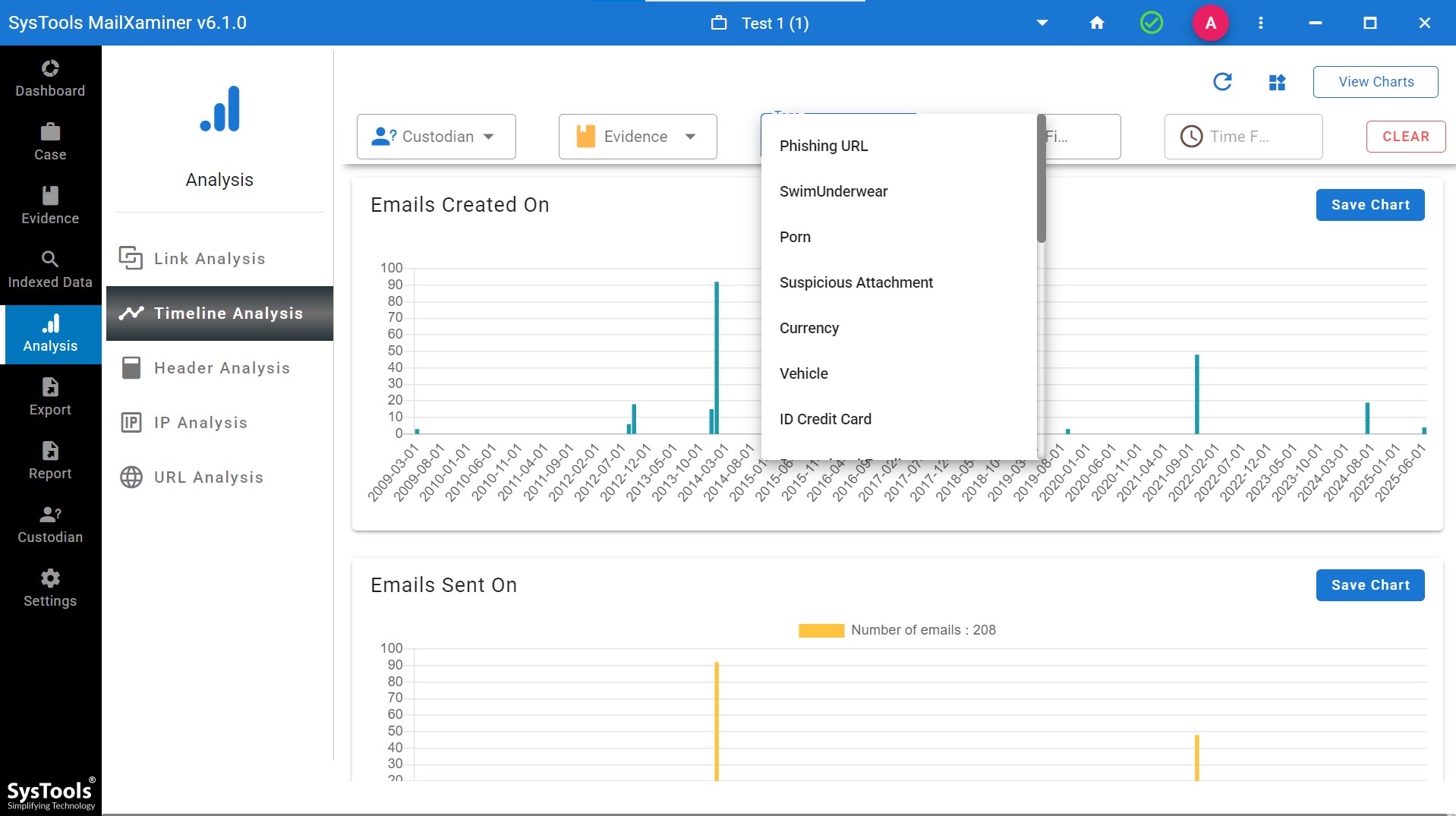
Step 6. Users will get the options to choose the emails as per the tags which is set as per the rules.
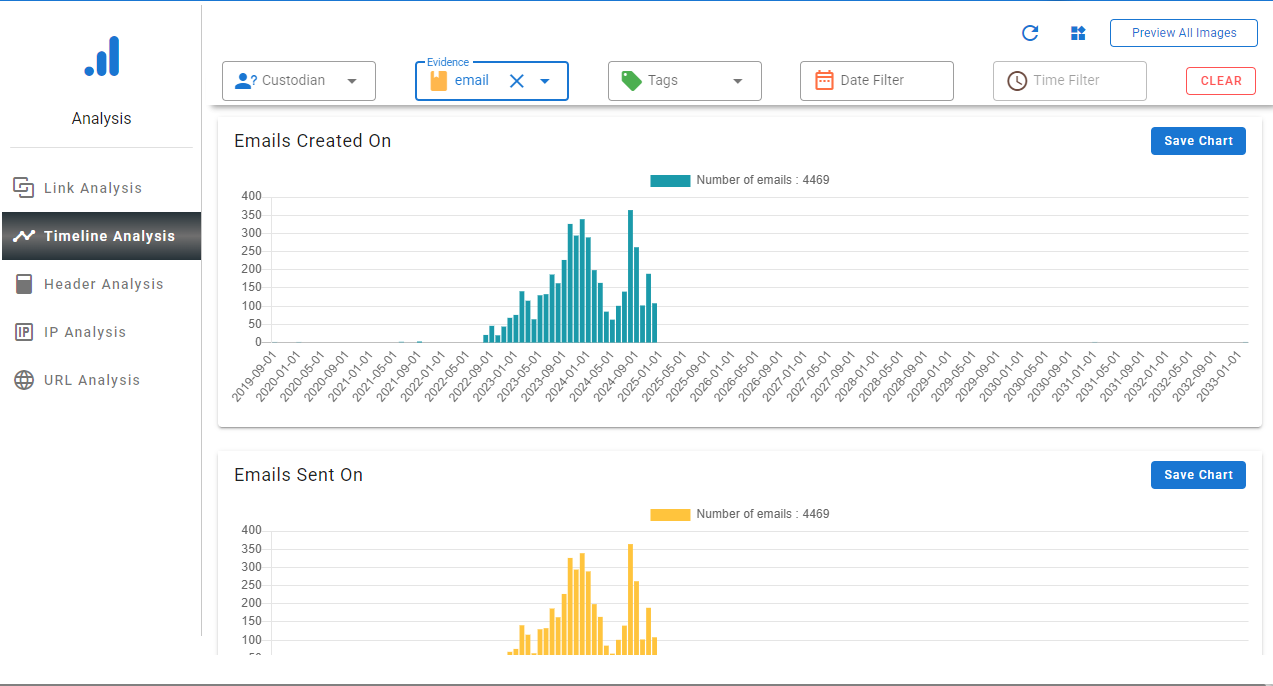
Step 7. After the analysis of the data through timeline investigations, you will get the option of saving the data chart, which shows the complete data.
Conclusion
Timeline analysis is a critical technique in digital forensics, allowing investigators to reconstruct events and identify security threats. By making the best utilization og digital forensic tools and visualization techniques, analysts can efficiently interpret digital timelines. Digital evidence analysis in forensic investigation is the focus of all investigators. But what if Examiners had the option to filter the data of a specific period? This will surely enhance the productivity and make it easy to process the data as evidence.
The above mentioned software makes it easy to investigate the email data. This makes email investigations more simplified for digital forensics investigators. This enhances the process by providing a comprehensive and efficient forensic solution for professionals. The tool provides both the features at a single platform that will help the investigators to visualize and obtain the information promptly. It also helps to create an effective report using the obtained information.

