Top 6 Digital Forensic Investigation Techniques For Effortless Investigation
Digital forensics is the process of investigating digital data collected from multiple digital sources. During the investigation process, a step-by-step procedure is followed in which the collected data is preserved and analyzed by a cybercrime investigator. Digital forensics aims to reconstruct the sequence of events that took place at the crime scene. Also, digital data and media can be recovered from mobile phones, laptops, hard disks, pen drives, floppy disks, and many more. Further to this, it can be used as a potential source of evidence in a court of law. As cybercrime investigators are digital forensics experts so, they carry out the investigation process and perform analysis of digital data. Moreover, they ensure the authenticity of evidence is maintained.
In this blog, we will focus on the different approaches to investigating the gathered digital evidence during the process of digital forensics.
Why Digital Forensics Investigation of Emails Are Important?
During a digital forensics investigation, thorough analysis of email is essential since most of the digital evidence can be found in email. Through email analysis, an investigator can dig out who the culprit is and other illegal information stored in the email.
Technically speaking, you will be able to easily trace the criminal by looking at the email properties found in the analysis of the email. In addition, with the help of the MIME view of emails, you can discover non-text attachments as well as hidden evidence.
Moreover, with the investigation of emails, you, as an investigator, can view the recovered emails to know if someone has tried to destroy any evidence or made changes in a particular email. Above all, you can learn about the detailed path of emails and also the IP addresses of all servers.
And by the way, when forensics investigators have the support of investigation techniques and tools, the task of analyzing emails becomes easier.
So, let’s first discuss the techniques and then move to the tool that can be used for analyzing emails.
Also Read: – What are the Current Challenges in Digital Forensics Investigations?
Different Types of Digital Forensic Investigations
Before knowing the procedural steps of digital forensics, let’s go through the different investigation types of digital forensic investigation, as mentioned below.
There are mainly two types of investigations:
1. Public Investigation: This includes investigations that are conducted against the suspected people to detect the crime scene. Generally, government agencies handle such types of investigations that relate to the public sector. Moreover, public investigations are generally investigated under the process of criminal investigations as they are primarily dealt with like criminal cases.
2. Private Investigation: These investigations are carried out for crimes related to businesses, offices, and organizations. Any kind of violation of the terms and policies of the private sector will fall under this category of investigation. Private investigations are generally referred to as corporate investigations.
How Forensics is Used in Digital Investigation: Step-Wise Procedure
The investigation process in digital forensics is a step-by-step procedure carried out meticulously. It ensures that no original evidence is destroyed in the process while maintaining the chain of custody. There are sequential steps for the digital forensics investigation procedure that is as follows:
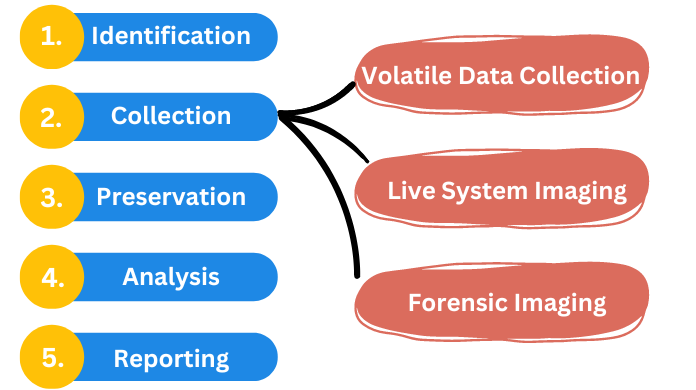
2. Collection: All the digital devices, which are potential sources of evidence are removed and properly collected from the crime scene. Collection of all the digital devices, in their true form, is ensured to maintain authenticity.
The Data Collection can be Further Divided into Four Main Types:
- (i) Volatile Data Collection: It includes the collection of all the executing data like user-logged-in details, date, time, and other RAM data. The system should remain turned ON during the investigation process.
- (ii) Live System Imaging: It includes the imaging action performed on data during the examination. During the investigation process, the system should remain turned ON.
- (iii) Forensic Imaging: A duplicate copy of the original device is created to perform imaging actions. An exact copy of the original device is created to perform manipulations. Hashing techniques are employed to ensure the privacy factor. The system should remain OFF during the investigation process.
- (iv) Seize Digital Devices Physically: When the above three methods fail, then this method comes to the rescue. Here, the digital devices are seized and then all the possible digital evidences are collected. The system may remain turned ON or OFF depending on the suitable circumstances.
3. Preservation: Preservation is an important step as it is necessary to preserve the place where the crime occurred. It is also important to preserve all the Electronically Stored Information (ESI) that could be obtained from the crime scene.
4. Analysis: Analysis involves an in-depth examination of all the digital evidence. Proper imaging is performed to ensure that the original evidence does not lose its authenticity. The examination and study of the criminal scenario help the investigator to conclude.
5. Reporting: This is the final step during the investigation process. Reports are a way of presenting all the facts and events systematically linked with the crime. These reports are then presented in the court of law as the source of evidence to solve the crime.
Digital Forensics Investigation Techniques You Must Know
Since most online fraud involves emails, it’s important to have a look at the different techniques to analyze them effectively.
- Bait Tactics
This digital forensic investigation process aims to extract and copy the IP address of the culprit. In the bait tactic scenario, an email with HTTP: “<img src=””>” tag will be sent to the email address which is under examination. The email with an image tag will have some image source on some computer that is supervised by the investigators. After that, when the email is opened, a log entry containing the IP address of the recipient is recorded on the HTTP Server hosting the image. This results in the tracking of the sender.
However, if the recipient is using a proxy server, then the IP address of the proxy server is recorded. The log on the proxy server can be used for forensic email tracking of the sender in digital forensic investigation methods. Due to some reasons, if the proxy server’s log is unavailable, then investigators may send the tactic email containing an embedded Java Applet that runs on the receiver’s computer or an HTML page with Active X Object. This will extract the IP address of the receiver’s computer and email it to the investigators. - Server Investigation
It is another procedure that is used to examine the copies of delivered emails and server logs to identify the source of an email message. The deleted or accidentally removed emails from the client’s mailbox can be extracted back from the servers. Most of the servers (Proxy or ISP) store a copy of all emails after their deliveries. Further, logs maintained by the servers can be analyzed to trace the system’s address, which is responsible for making email transactions. The server examination is very useful to identify the source of the email message.
However, copies of email and server logs are stored by the servers only for a limited period. Moreover, SMTP servers which store data like credit card numbers and other data about the owner of the mailbox can be used to identify the person behind an email address. - Network Device Investigation
This investigation involves all the logs maintained by the network devices. This includes routers, firewalls, and switches that are used to investigate the source of an email message. This type of digital forensic investigation technique is complex and used only when the logs of servers are not available due to some reasons. - Software Embedded Identifiers
Information associated with the email creators, attached files, or documents, is included in the email message. It can be used by the sender for composing the email. Now, this information can be present as a custom header or MIME content as a transport-neutral encapsulation Format (TNEF). Analyzing email for these details in email digital forensics may reveal some important information related to the sender’s email preferences and the options that could help client-side evidence gathering. This digital forensic investigation method can reveal PST file names, Mac addresses, Windows login usernames, etc. of the client’s computer, which is used to send an email message. - Sender Mailer Fingerprints
The information related to software that handles the email files at the server can be revealed from the Received header field. Additionally, the identification of software handling email at the client can be discovered by using various sets of the header like ‘X-Mailer’. These headers describe applications and their version used by the clients to send the email. This information about the sender’s client’s computer can be used to help investigators create an effective plan. - Email Header Forensics
This is one of the most common digital forensic investigation techniques used by investigators to identify the culprit. A normal email structure can be defined as an envelope and header with data. Envelop means the body content of the email with attachments. Moreover, the headers of the message body contain information related to the sender or the path along which the message has traveled, etc. Sometimes, criminals spoof the metadata information to conceal the sender’s identity. Thus, a detailed analysis of header data during email header forensics helps the investigator to find evidence.
How to Examine Email Message Header Data?
Here, we are going to perform an in-depth analysis of the email message header with the help of a table given below. This digital forensic investigation process will help you to understand more about the email header data.
| S No. | Header | Value |
| 1 | X-Apparently-To: | bob@bob.com via a4.b4.c4.d4; Tue, 30 Nov 2010 07:36:34 -0800 |
| 2 | Return-Path: | < alice@alice.com > |
| 3 | Received-SPF: | none (mta1294.mail.mud.bob.com: domain of alice@alice.com does not designate permitted sender hosts) |
| 4 | X-Spam-Ratio: | 3.2 |
| 5 | X-Originating-IP | [a2.b2.c2.d2] |
| 6 | X-Sieve: | CMU Sieve 2.3 |
| 7 | X-Spam-Charsets: | Plain=’utf-8’ html=’utf-8’ |
| 8 | X-Resolved-To: | bob@bob.com |
| 9 | X-Delivered-To: | bob@bob.com |
| 10 | X-Mail-From: | alice@alice.com |
| 11 | AuthenticationResults: | mta1294.mail.mud.bob.com from=alice.com; domainkeys=neutral (no sig); from=alice.com; dkim=neutral (no sig) |
| 12 | Received: | from 127.0.0.1 (EHLO mailbox-us-s-7b.tariq.com) (a2.b2.c2.d2) by mta1294.mail.mud.bob.com with SMTP; Tue, 30 Nov 2010 07:36:34 -0800 |
| 13 | Received: | from MTBLAPTOP (unknown [a1.b1.c1.d1]) (Authenticated sender: tariq@tariq.com) by mailbox-us-s-7b.tariq.com (Postfix) with ESMTPA id 8F0AE139002E for ; Tue, 30 Nov 2010 15:36:23 +0000 (GMT) |
| 14 | From: | “Allice” <Alice@a.com> |
| 15 | Subject: | A Sample Mail Message |
| 16 | To: | “Bob Jones”<bob@bob.com> |
| 17 | Content-Type: | multipart/alternative; charset=”utf-8″; boundary=”KnRl8MgwQQWMSCW6Q5=_HgI2hw Adah5NLY |
| 18 | MIME-Version: | 1.0 |
| 19 | Content-TransferEncoding: | 8bit |
| 10 | Content-Length: | 511 |
| 21 | Reply-To: | “Smith” <smith@smith.com> |
| 22 | Organization: | Alices Organization |
| 23 | Date: | Tue, 28 Nov 2010 21:06:22 +0530 |
| 24 | Return-Receipt To: |
smith@smith.com |
| 25 | DispositionNotification-To | jones@jones.com |
| 26 | Message-Id: | <20101130153623.8F0AE139002E@mailbox-us-s7b.tariq.com> |
A sample header set of an email message, which is sent by tariq@traiq.com pretending to be alice@alice.com and sent to bob@bob.com is shown in the table mentioned above. In this email sender’s address, date, reply, and various other fields have been spoofed. On examination of identities such as domain name, IP address, etc. it was revealed that servers used in the email sending process have been edited. The following header set shows the information present in the various headers of the message.
- Header X- Apparently-To: It is relevant when the email has been sent as a “BCC” or to recipients of some mailing list. In most cases, this field contains the address as in the “To” field. However, when the email has been sent to a “BCC” recipient or mailing list, then X-Apparently-To is different from the “To” field.
Thus, X-Apparently-To always shows the email address of the recipient, irrespective of whether the mail has been sent using To, Bcc, or Cc addresses or by using some mailing list. - Received -SPF: It is the value that specifies that the email has arrived from a domain that either does not have an SPF record or is not yet a designated permitted sender.
- Return- Path Header: It is the email address of the mailbox specified by the sender in the MailForm command. If no authentication mechanism is in place at the sending server then this address can also be spoofed.
- X-Spam-Ratio: MUA is contained in the X-Spam-Ratio field or the spam score is calculated by the spam filtering software of the receiving server. Email is classified as spam when the ratio exceeds a certain pre-defined threshold.
- X- Originating-IP: This reflects the IP address of the last MTA of the sending SMTP server, which has delivered email to the server of bob@bob.com.
- X- Sieve Header: It defines the name and version of the message filtering system. It refers to the scripting language used to specify conditions for message filtering and handling.
- X-Spam-Charsets: This field specifies the character set used for filtering the messages.
- X- Resolved-To: It is the email address of the mailbox to which the email has been delivered by MDA of bob’s server.
- X- Mail- From Header: The field specifies the email address of the mailbox specified by the sender in the MailFrom command.
- Authentication-Results Header: It shows that mta1294.mail.mud.bob.com received mail from the alice.com domain which does not have DomainKeys signature and DKIM signature.
- Received Header Field (12): This field contains the trace information which indicates 127.0.0.1 as the IP address of the machine that sends the message.
- Received Header Field (13): It represents the trace information indicating MTBLAPTOP as the name of the machine that sends the message.
- From, Subject and To: These fields reflect the email address of the author, message subject and the email address of the recipient.
- Content-Type, MIME-Version, Content-Transfer-Encoding, and Content-Length: The MIME header describes the type of MIME content, transfer encoding, its version, and length.
- Reply-To: It is an arbitrary address that is associated with some random user who may not be related to the sender in any way.
- Organization Header: This field is an information field that shows the sender’s organization.
- Date Header: It shows the date on which the email was composed and submitted for delivery.
- Return-Receipt-To: This indicates the email address, MSA, MTA, and MDS which is used for sending delivery notifications.
- Disposition-Notification-To: This field reflects the email address and MUA used while submitting a message indicating that the message has been displayed.
- Message ID: It is formed when a domain name is appended with a unique number by the sending server.
Follow the digital forensics investigation procedure discussed in the above section to implement the investigation process in an effective yet smart way.
Now, let’s take a look at the professional tool that you can use for an error-free analysis of emails.
Best Software for Digital Forensic Investigation
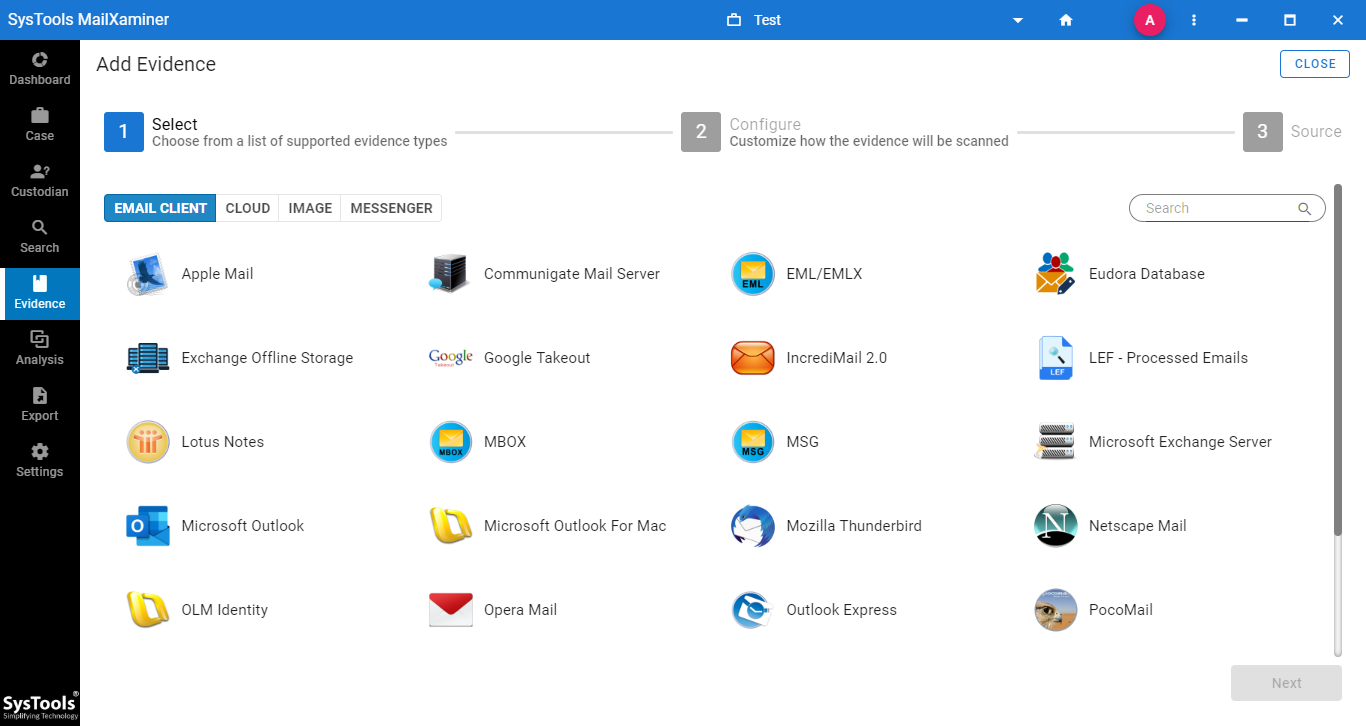
To aid in the recovery and preservation of digital evidence, a professional Email Investigation Tool is required. , MailXaminer proved to be the best software in the market that most Law enforcement agencies depend on to examine emails.
The software enables an investigating officer to perform email analysis with speed, ease, and accuracy. It is integrated with amazing features that help to examine the email file in different preview modes.
Also, investigators can effortlessly implement digital forensic investigation techniques such as email header forensics with the help of this feature-rich tool. This tool is proven to be a smart utility that helps forensics examiners, who handle and work with their cases, seamlessly.
It is an efficient digital forensics tool. It helps in analyzing emails providing precise results. Using this, investigators carry out digital forensic processes. It further guides them on how to use this tool efficiently. For your information, this software supports 20+ file formats, as well as supports a wide variety of web-based applications. Certainly, one can rely on this impeccable tool for investigations related to digital forensics.
Closing Remarks
Typically, the police or other authorities are tasked with apprehending an assailant, and digital forensics is used to gather proof. This is necessary for identifying the offender and, more crucially, for bringing charges against them. Digital forensics is crucial, which explains why the area has grown to be quite well-known over time. The more quickly and thoroughly a digital forensics investigation is conducted, the better the odds are of the hacker being apprehended and any damages being corrected. And, with the right digital forensics investigation techniques and tools, the entire process seems a piece of cake. Thus, here we discussed different techniques and put some light on the best forensics tool for your reference.