What is Metadata? Understand the Data Behind Digital Evidence
What is metadata? Simply put, it’s data about data. It still sounds simple but incredibly powerful, especially in metadata forensics, where it can reveal the hidden truth behind digital evidence. Think of it as the label of the file format that does not hold the complete content, but tells you what’s inside, when it was created, who touched it last, and how it’s organized.
In today’s data-centric world, metadata can be crucial in digital evidence collection. Metadata forensics is the primary step in digital forensic investigation techniques that investigators prefer to perform. For everyday users, it’s what makes it easier to find, organize, and understand digital information.
Let’s say you’re looking at an email. The message is your data, but the metadata tells you when it was sent, who it was sent to, the subject line, the email server used, and more. This behind-the-scenes, detailed information is often more telling than the message itself. In short, it will allow you to check email properties like from web pages to images, videos, documents, and beyond. It plays a critical role in how digital content is stored, tracked, and used. Therefore, it can provide you with the context, accountability, and even the legal evidence.
So, without any further ado, let’s understand what metadata is in detail and how it works is key to navigating our digital world.
Introduction to Metadata
It is an information that describes and gives context to other data. A good analogy is a book. The data of the book is the content, while the metadata is the title, format, publication date, author, and book’s subject.
What is Metadata? Metadata is not only about the content itself. But it holds the entire structured background data. That tells us more about how, when, where, and by whom that content was created, assessed, or modified.
Let’s break that down. Imagine you open a PDF document for PDF file analysis. You read the words that are actual data. But the essential information hiding in the background is metadata. That consists of the author’s name, the creation date, the last modified time, the software used to create the file, and even the device it was created. All of that is metadata.
In email metadata analysis, metadata becomes even more critical. An email may look clean from the outside, but its metadata, such as sender IP address, SMTP server info, and timestamps. Message IDs and routing paths an exposed to email spoofing attempts, phishing campaigns, or even insider threats.
What is the Purpose of Metadata?
The primary purpose of metadata is to provide context, structure, and meaning to data so it can be easily found, understood, managed, and used effectively.
In simpler terms, metadata answers the questions What is this data? Where did it come from? When was it created? Who touched it? How should it be used?
Here’s a breakdown of the core purposes:
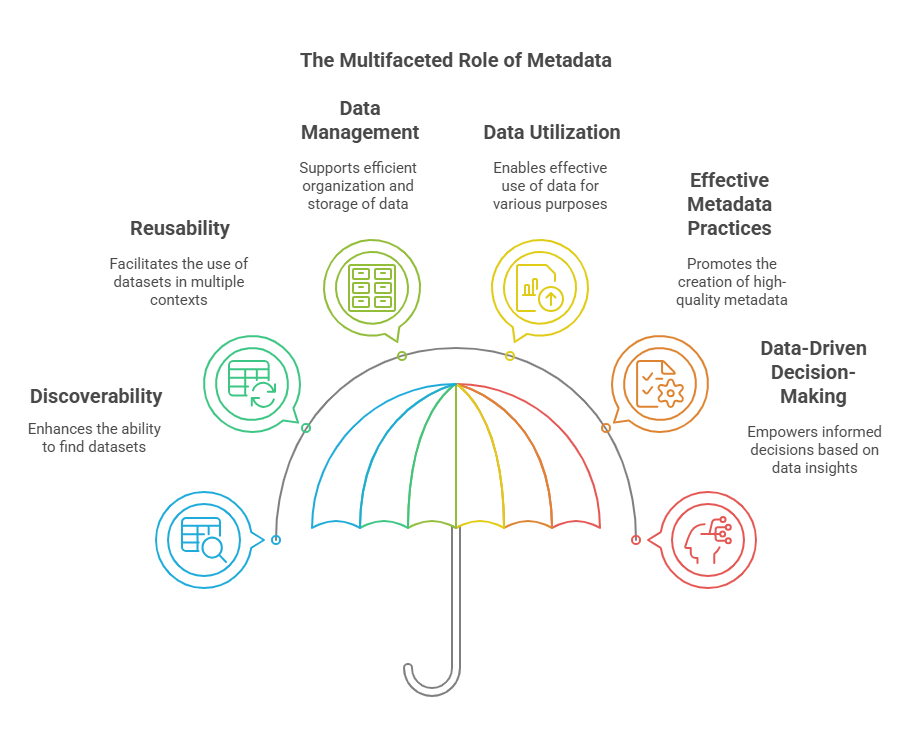
What are the Different Types of Metadata?
Metadata isn’t one-size-fits-all. It’s incredibly versatile, taking on different forms depending on the data it’s describing and how it’s being used. Whether you’re managing data systems, conducting email forensics, or organizing a media library, understanding the different types of metadata can help you work smarter and more accurately.
- Descriptive Metadata
This is probably the type most people interact with. This includes things like the title of a document, the author’s name, tags, and even keywords. It’s used to identify and locate digital content. In digital forensics, it helps sort and filter through huge volumes of data by person, date, keyword, or location.
- Structural Metadata
This explains how pieces of data relate to one another. It’s often found in databases, XML files, and digital libraries. It’s also used to define chapters in an e-book or how pages are ordered in a scanned document.
- Administrative Metadata
It provides technical details about the file. This includes creation date, file type, size, and user permissions. It’s essential for managing access, storage, and rights. For forensic investigators, it can confirm if a document was modified, copied, or accessed.
It’s the kind of information that makes audits, compliance checks, and digital investigations possible.
- Provenance Metadata
It tracks the history and origin of the data. It answers the “where did this come from?” and “how did it get here?” questions. This type is especially vital in legal and regulatory environments where chain-of-custody and version history are important.
From metadata to database records, each type plays a role in making data traceable, usable, and reliable.
Why is Metadata Forensics Crucial in Digital Investigations?
In today’s digital forensics realm, metadata is not just informative, it’s evidence that has the supreme capability itself to uncover the truth behind different types of Email Threats. So, what is metadata in digital forensics? It is the medium that provides the digital footprints that tie everything together in different cases. This helps in cybercrime investigations, tracking the source of a data breach, or to investigate a suspicious email, etc.
The reasons why it is crucial in digital forensics:
- Knowing when a file was accessed, changed, or deleted helps build a timeline analysis of activities.
- Administrative message headers can reveal the username or device that interacted with the file, which helps with link analysis.
- Forensically sound metadata proves whether a document has been changed.
- Courts often accept metadata information as digital evidence if properly extracted and preserved.
- Each email holds a wealth of information in its headers, like sender and recipient addresses, time/date stamps, server hops (IP addresses and domains), or Message IDs or thread information.
- A core principle in forensics is maintaining the integrity of digital evidence. Any mishandling can compromise the case.
How to View Metadata with Advanced Forensic Software?
You can simply view with the best email forensic software, named MailXaminer. This is the advanced digital forensics software that is especially designed to perform an advanced way of performing investigations with this one-stop solution.
It smooths your process of digital evidence with the multiple salient features for metadata forensics, especially for digital forensic experts. It provides trusted results with accuracy and efficiency.
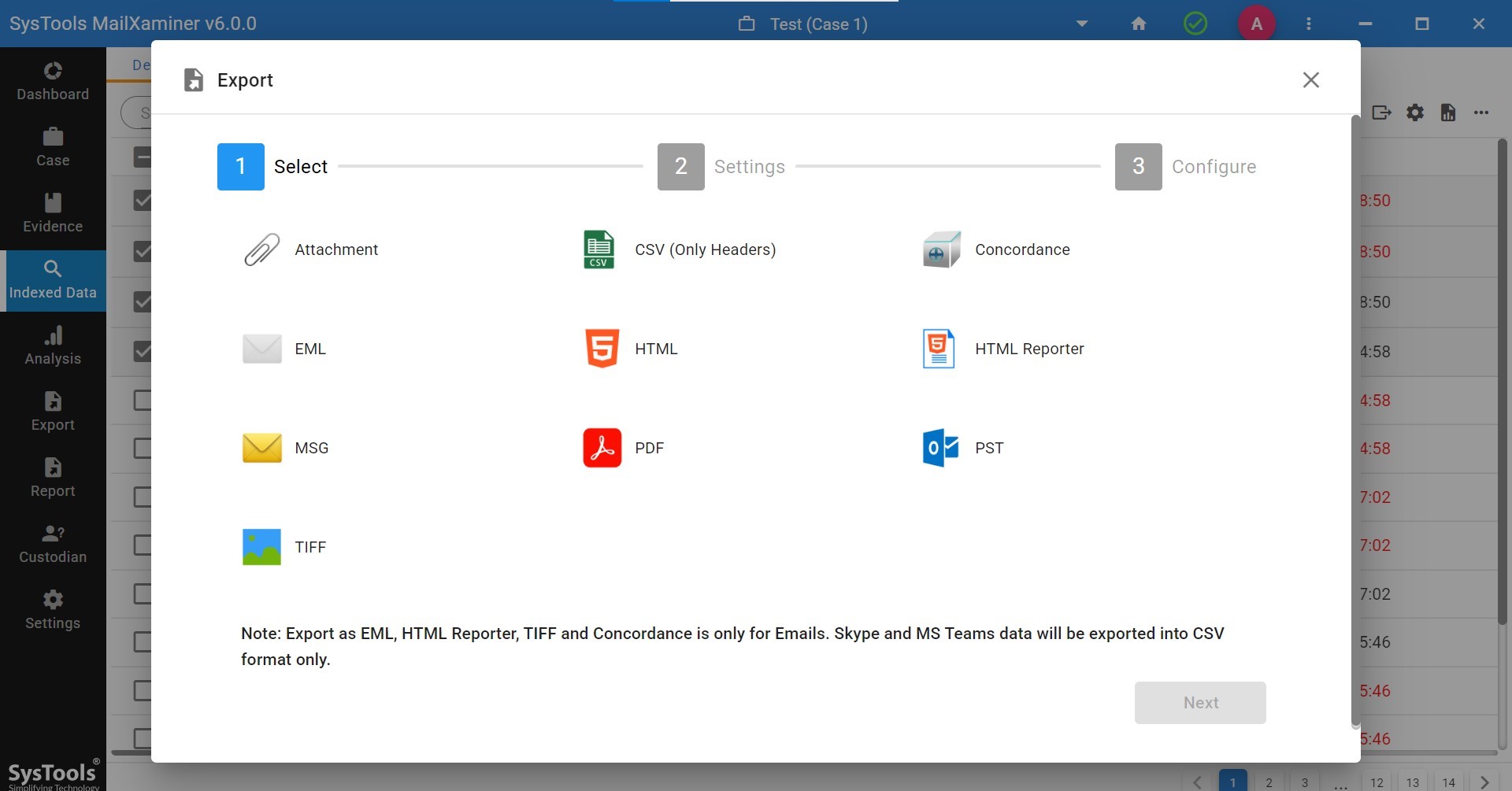
Let’s discuss the steps on how the software helps to view the header in emails:
Step 1. Set up the software on your system and add a new case.
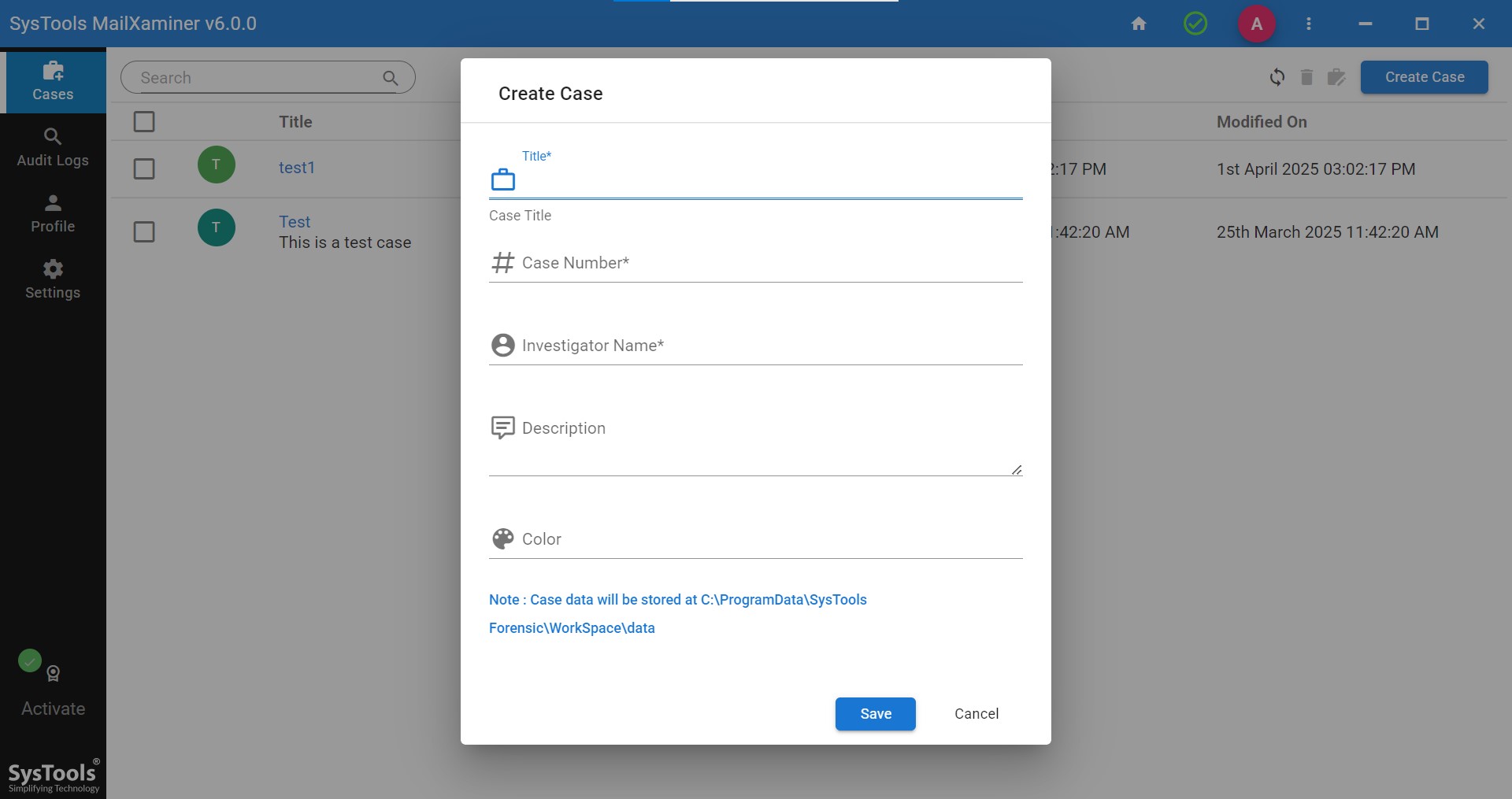
Step 2. After adding the case, add the evidence.
Note- the software will provide you with an option of email client, cloud image, and messenger option to add as evidence.

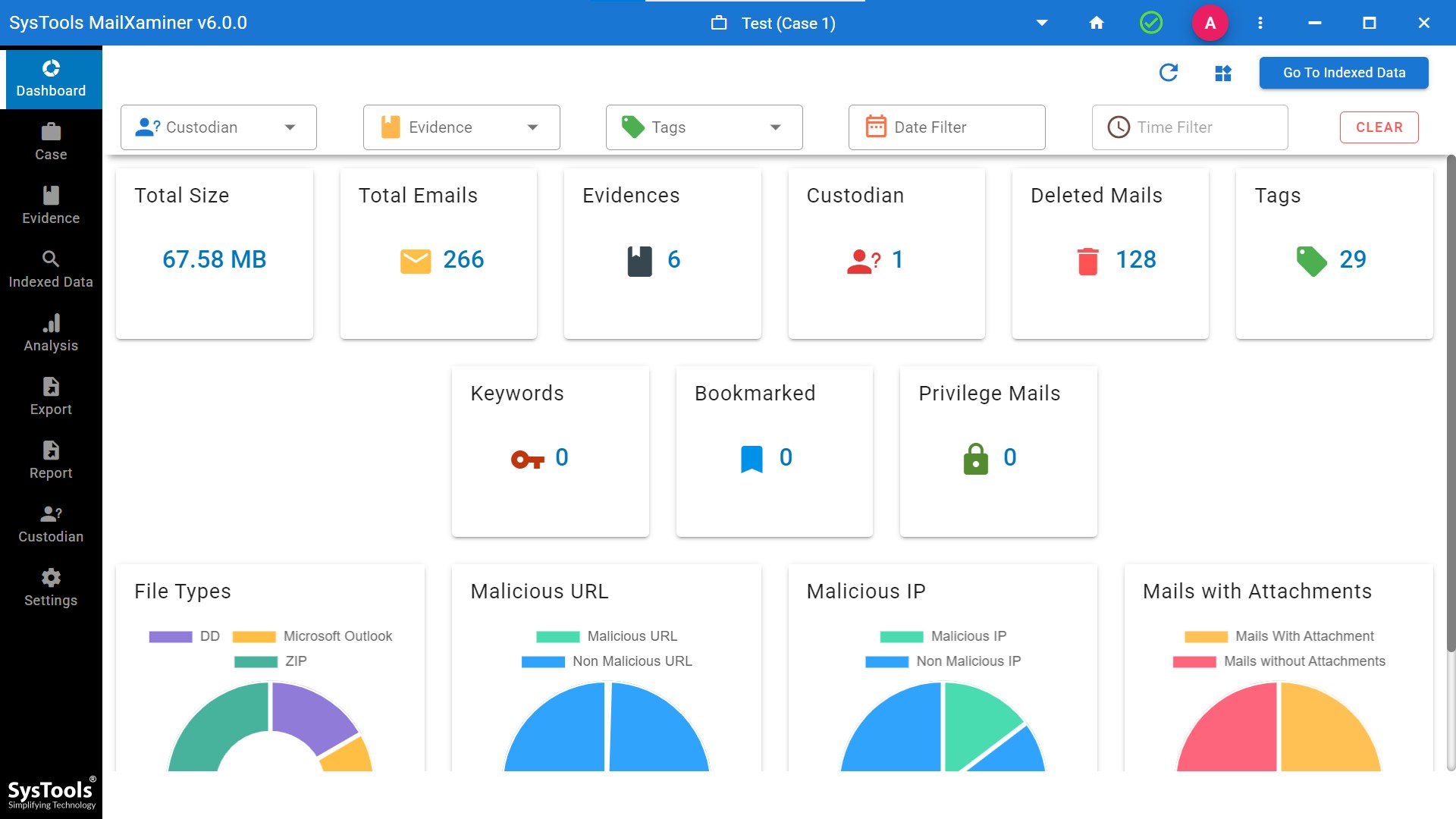
Step 3. After adding the file as evidence into the software, the complete dashboard is visible on the screen, what the file consist of.
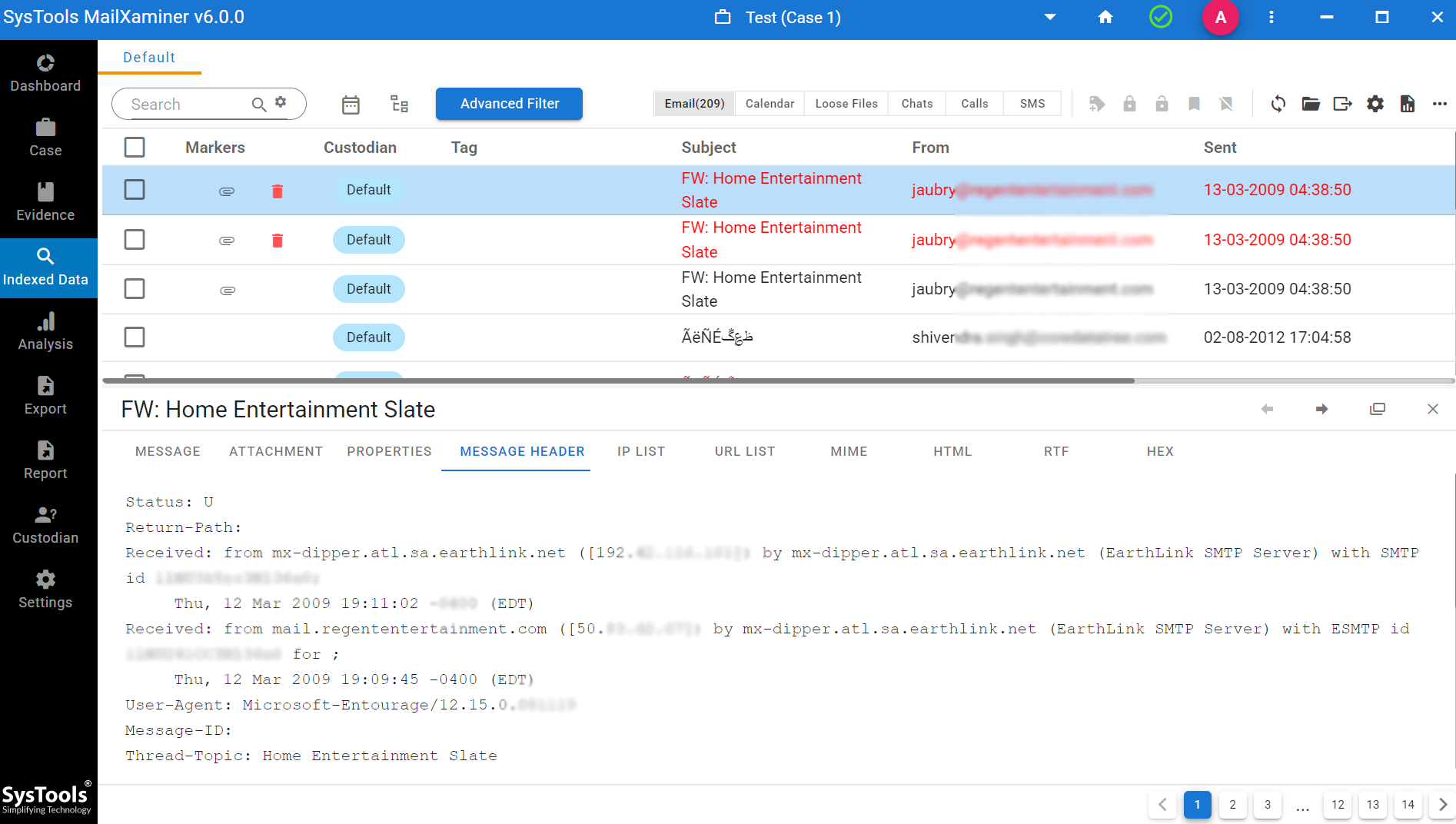
Step 4. Then go to the indexed data and select the specific email for email header analysis.
Step 5. Lastly, software will provide you with an option to export the selected file as evidence to make it safe for you in your offline mode as well.
Conclusion
Metadata is the foundation that adds meaning, structure, and context to digital information. It plays a critical role across fields like digital forensics and cybersecurity for data management. From tracking who accessed a file to verifying the origin of an email, it serves as a silent yet powerful source of truth.
Understanding and managing it is essential for maintaining integrity, security, and efficiency because data continues to grow. Whether you’re a forensic expert or a business professional, analyzing metadata effectively ensures smarter decisions, accurate analysis, and stronger control over your digital environment.

