Windows Live Mail Forensics- Analyze Email Evidence Faster
To begin any digital investigation involving Windows Live Mail, it’s crucial to understand how this email client stores its data within the Windows operating system. Especially when conducting EML file forensics to analyze and extract evidence.
Windows Live Mail (a component of the Windows Essentials Suite) is one of the most renowned freeware email client applications, with more than 280 million active accounts. WLM (Windows Live Mail) efficiently manages multiple email accounts, calendars, contacts, and other data items. Also, Windows Live Mail supports Post Office Protocol (POP3) and IMAP (Internet Message Access Protocol) as incoming server and Simple Mail Transfer Protocol (SMTP) as the outgoing server.
File Formats & Locations of WLM Data Files
With the discontinuation of Outlook Express in Windows Vista, Windows Live Mail became the default email client on many systems. On Windows 7 and later, email data is typically stored at:
C:\Users\[UserName]\AppData\Local\Microsoft\Windows Live Mail
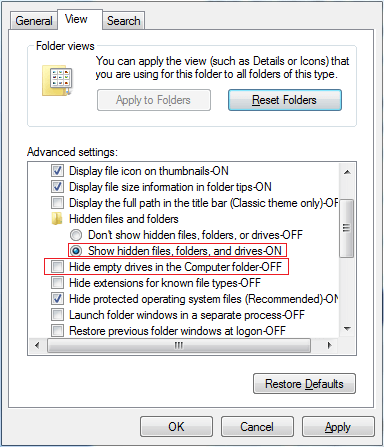
Each message is saved individually with metadata. It also contains the additional information that Windows Live Mail requires to display email data. One needs to apply the following options to view the hidden folders and file extensions:
- Control Panel > Folder Options > View > Show hidden files and folders
- Control Panel > Folder Options > View > Hide extensions for known file types (uncheck it)
These steps allow access to all relevant mail content and its associated properties.
Default Location of Windows Live Mail in different Windows OS Versions is as follows:
Windows XP: –
C:\Users\[UserName]\AppData\Local\Microsoft\Windows Live Mail
Vista or Windows 7: –
C:\Users\[UserName]\AppData\Local\Microsoft\Windows Live Mail
Windows 8: –
C:\Users\[UserName]\AppData\Local\Microsoft\Windows Live Mail
Modes of Operation for Contact Database in Windows Live Mail Forensics
In Windows Live Mail, investigative standpoint, technocrats must know that in Windows Live Mail forensics, the contact database is stored in contact.edb file, which behaves differently based on the mode of usage:
-
Offline Mode: When not signed in to a Microsoft account
-
Online Mode: When signed in using a Live ID
Each mode maintains a unique set of contact entries stored in separate paths.
Contact Database File in WLM
- Each mode in WLM should have a unique file (same name, different location).
- Each Live ID used in Live ID (Online) mode must have a unique file.
- The file for Default (Offline) mode is stored in a hidden subfolder called DBStore. To view the DBStore folder, users have to configure Windows Explorer to “Show hidden files/folders and protected operating system files”.
Common Paths of DBStore Folder to locate contact database files
WLM 2011 (Pre QFE3 Version) – Windows 7 or Vista
C:\Users\Windows\Username\AppData\Local\Microsoft\Windows\Live\Contacts\Default\15.4\DBStore
WLM 2011 (QFE3 Version) – Windows 7 or Vista
C:\Users\Windows\Username\AppData\Local\Microsoft\Windows\Live\Contacts\Default\15.5\DBStore
Note: – The Default DBStore folder is a hidden folder of the “15.5” folder.
The Location of DBStore folder in Live ID (Offline) Mode
WLM 2011 (Pre QFE3 Version) – Windows 7 or Vista
C:\Users\(username)\AppData\Local\Microsoft\Windows Live\Contacts\(Live ID)\15.4\DBStore C:\Users\(username)\AppData\Local\Microsoft\Windows Live\Contacts\(Live ID)\15.5\DBStore
Windows Live Mail Forensics to Investigate Corrupted or Deleted Files
Nowadays, instant messengers, social networking sites, and emails are the major carriers of information. It is mostly used by corporations for professional communication purposes. Thus, the elimination of such information accidentally or otherwise may cause inconvenience to the users. Finally, to balance such catastrophic situations, Windows Live Mail comes with a “Deleted Items” folder.
This folder is available to store the items deleted from any mail folder of the client. However, cases involving hard deletion of emails are not handled well by the client. Nevertheless, erasing or deleting email messages permanently does not mean that they’re gone forever; they can still be extracted forensically.
Forensic tracing of the email is used for retrieving information from mailbox files for analysis purposes. To do the same, we must first be aware of the file extension of emails and the technicalities related to it.
Analysis of Windows Live Mail File Using Advanced Method
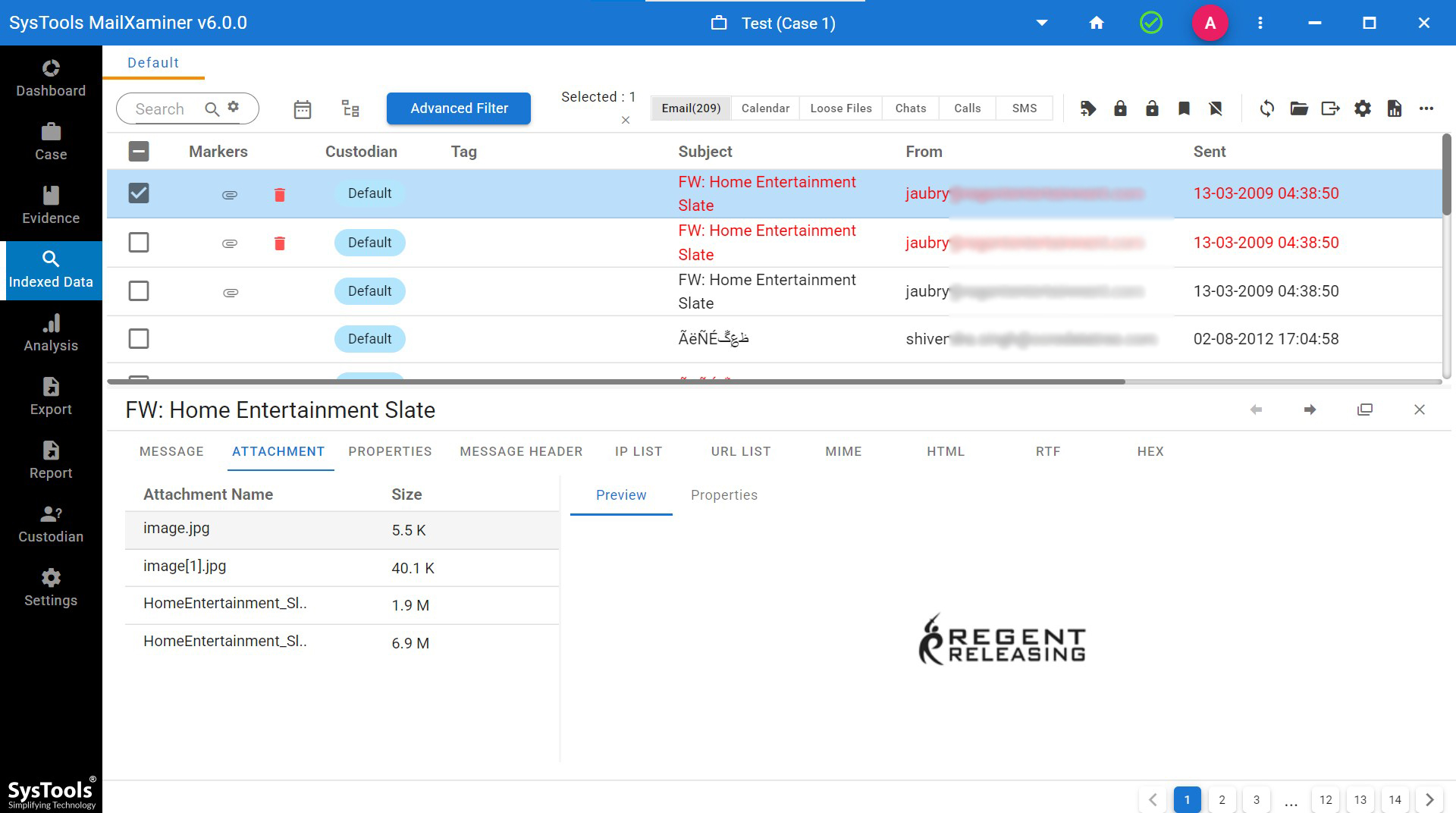
The best email Analysis tool can examine and analyze email files using its various attributes, such as Message view for normal email body examination, viewing the hexadecimal code with Hex View, Properties of email file, Message header analysis, Attachments IP list, URL list, MIME View, HTML View, RTF View. These multiple-mode features of this tool help to identify any kind of manipulation in the uploaded data file.
Attachments always deal with important digital artifacts. The user-friendly interface of the software enables a brief investigation of embedded attachments in Attachment View. With the help of MailXaminer, the investigator can easily dig deeper to find the potential evidence from the Email files.
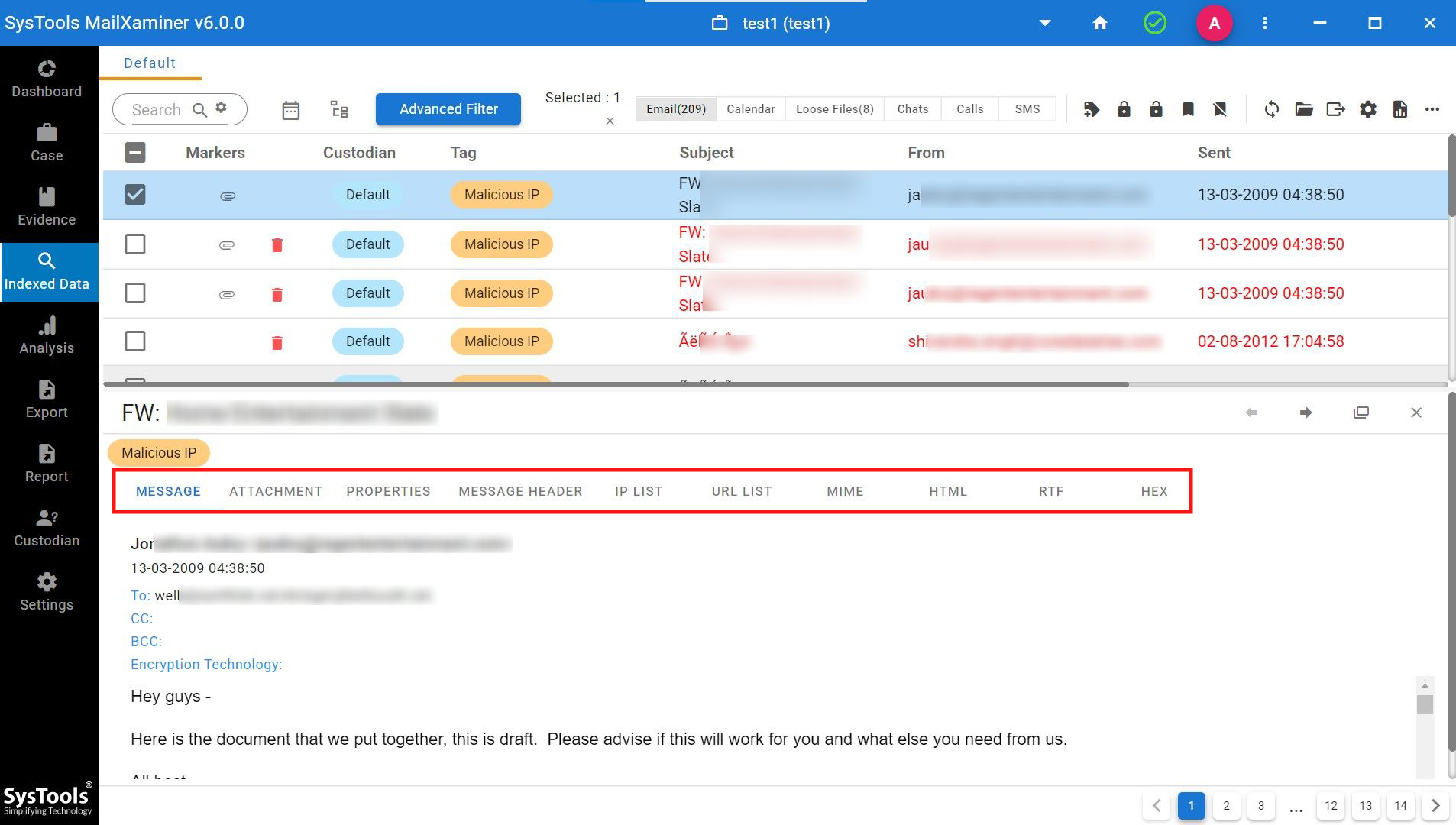
Mail View
In normal Mail View, the email header represents a traversed path, which includes From, To, Cc, Bcc, Subject, Tag, and Attachment(s) details. The email body part also shows text/images of the email.
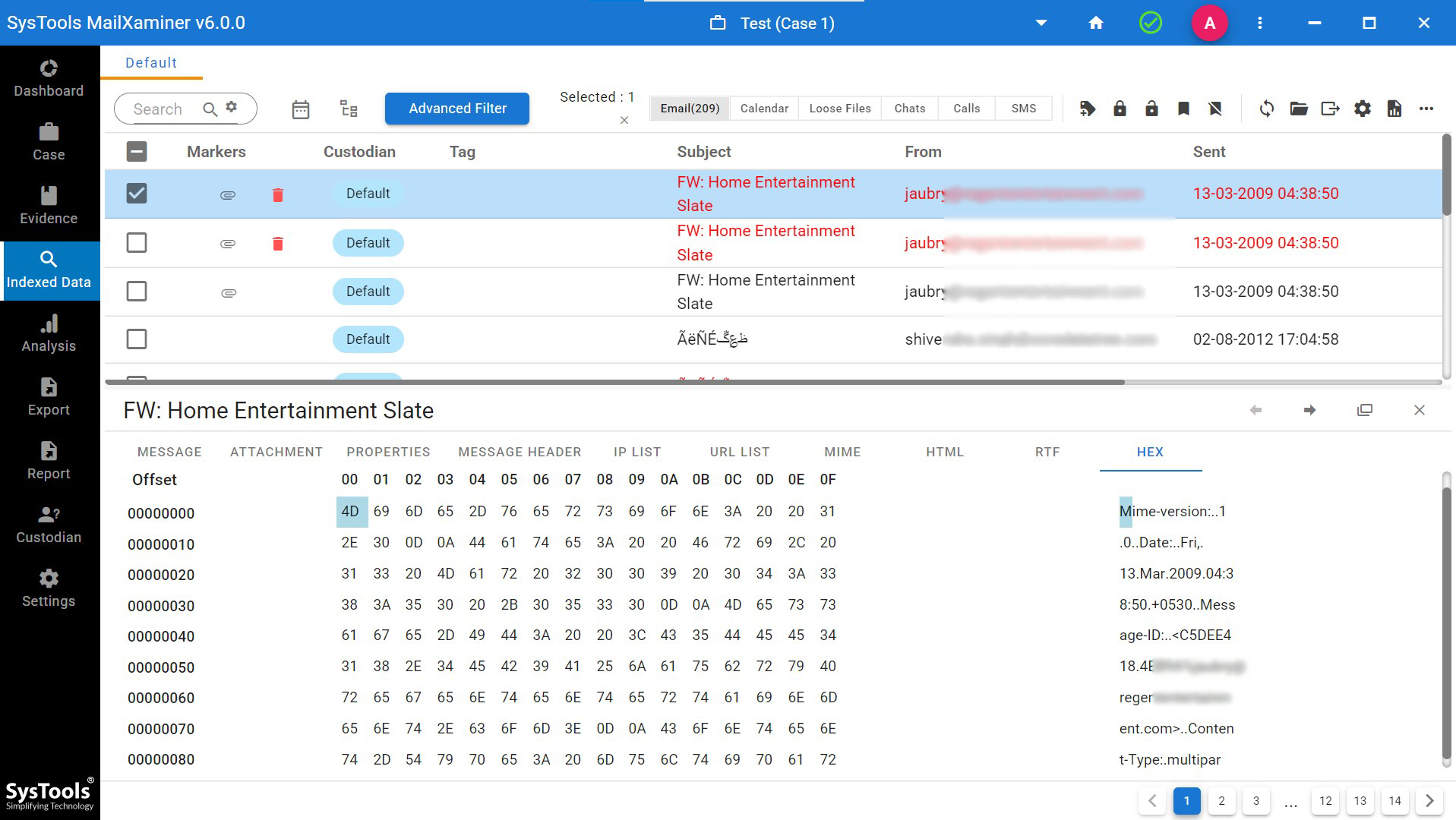
Hex Mode- Hexadecimal code examination in Hex View simplifies the structure of complicated binary values. These values make the investigation tasks easier to understand and assist in judging various crimes like email fraud.
Properties of the email files can be viewed clearly in this preview mode. It helps investigators to extract the hidden information of the email files, such as Message-ID, Body Details, Message Flags, etc.
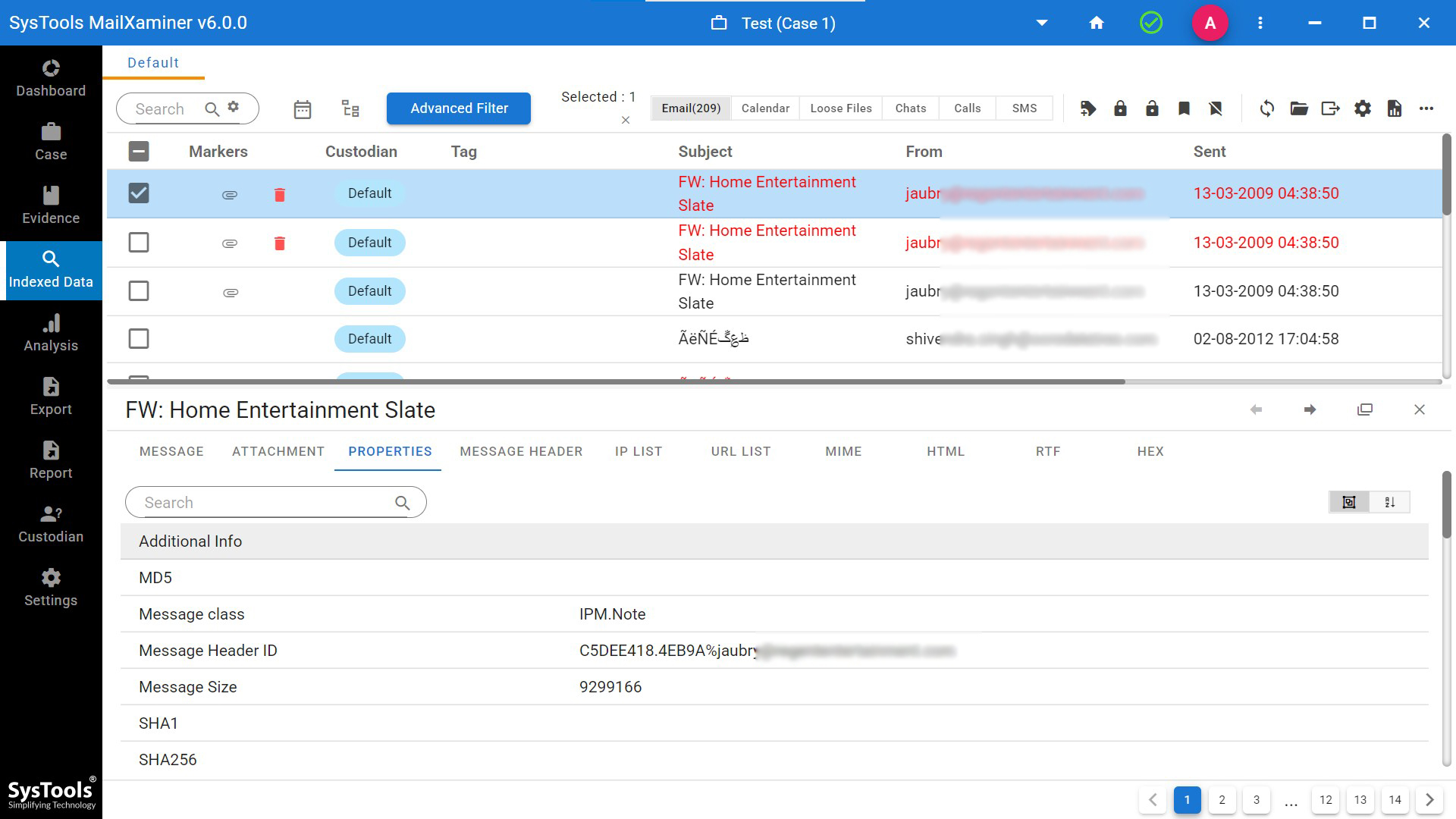
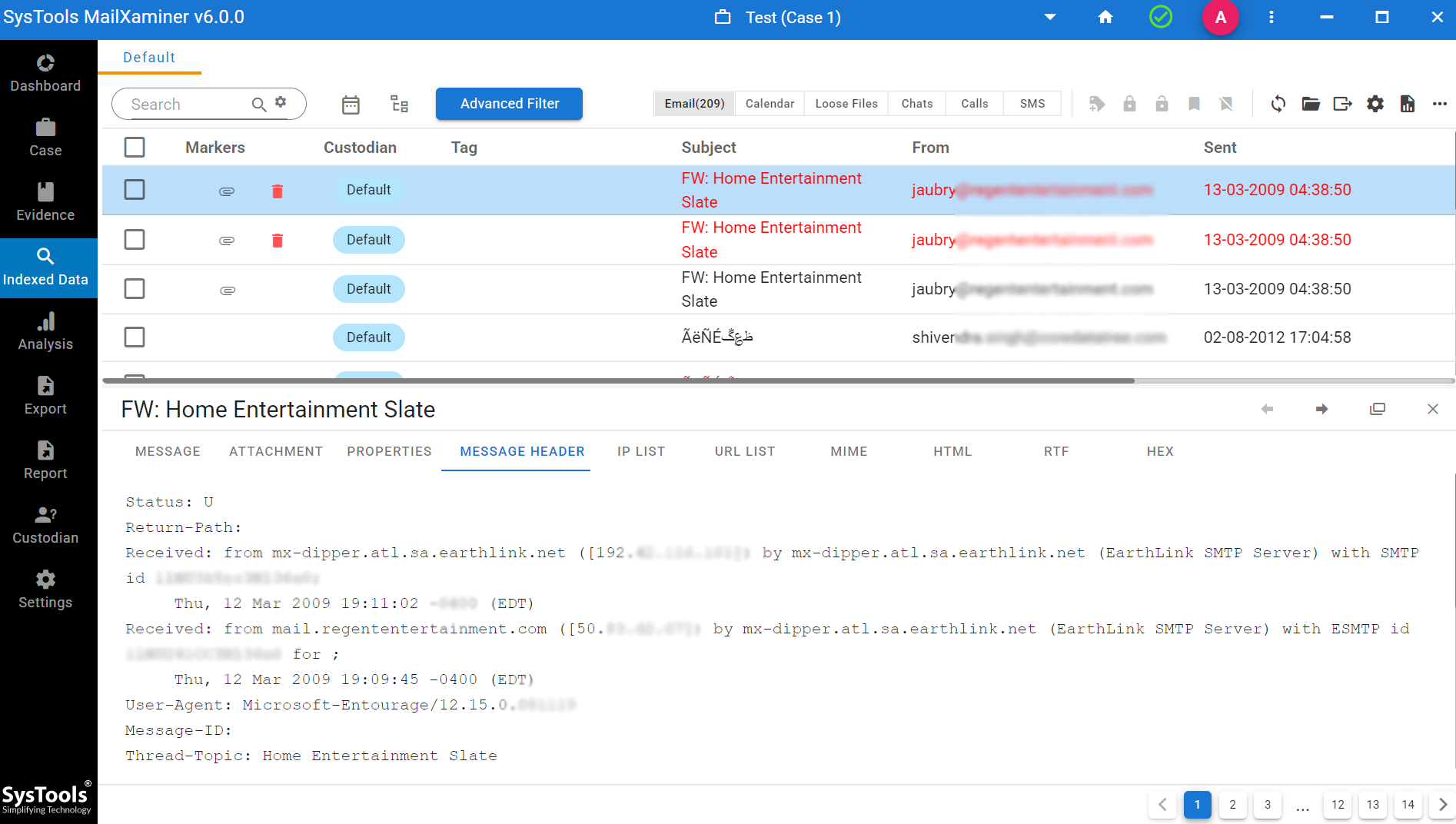
Massage Header View: It gives the information to track emails. It also helps to find the original sender’s IP Address, MIME version, X-Priority, Message-IDs, Content-Type, etc.
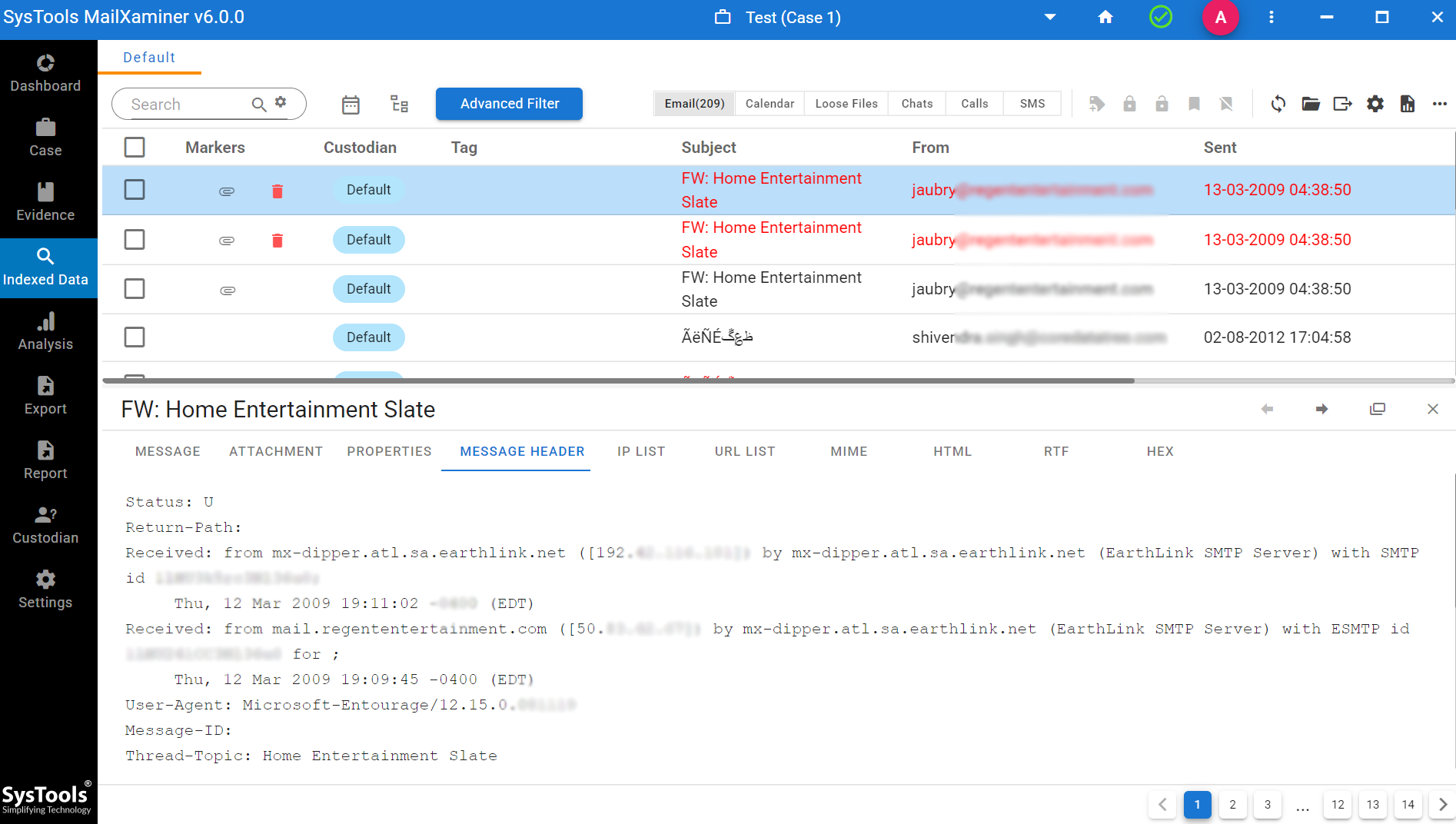
Some Extra Features for Windows Live Forensics Tool
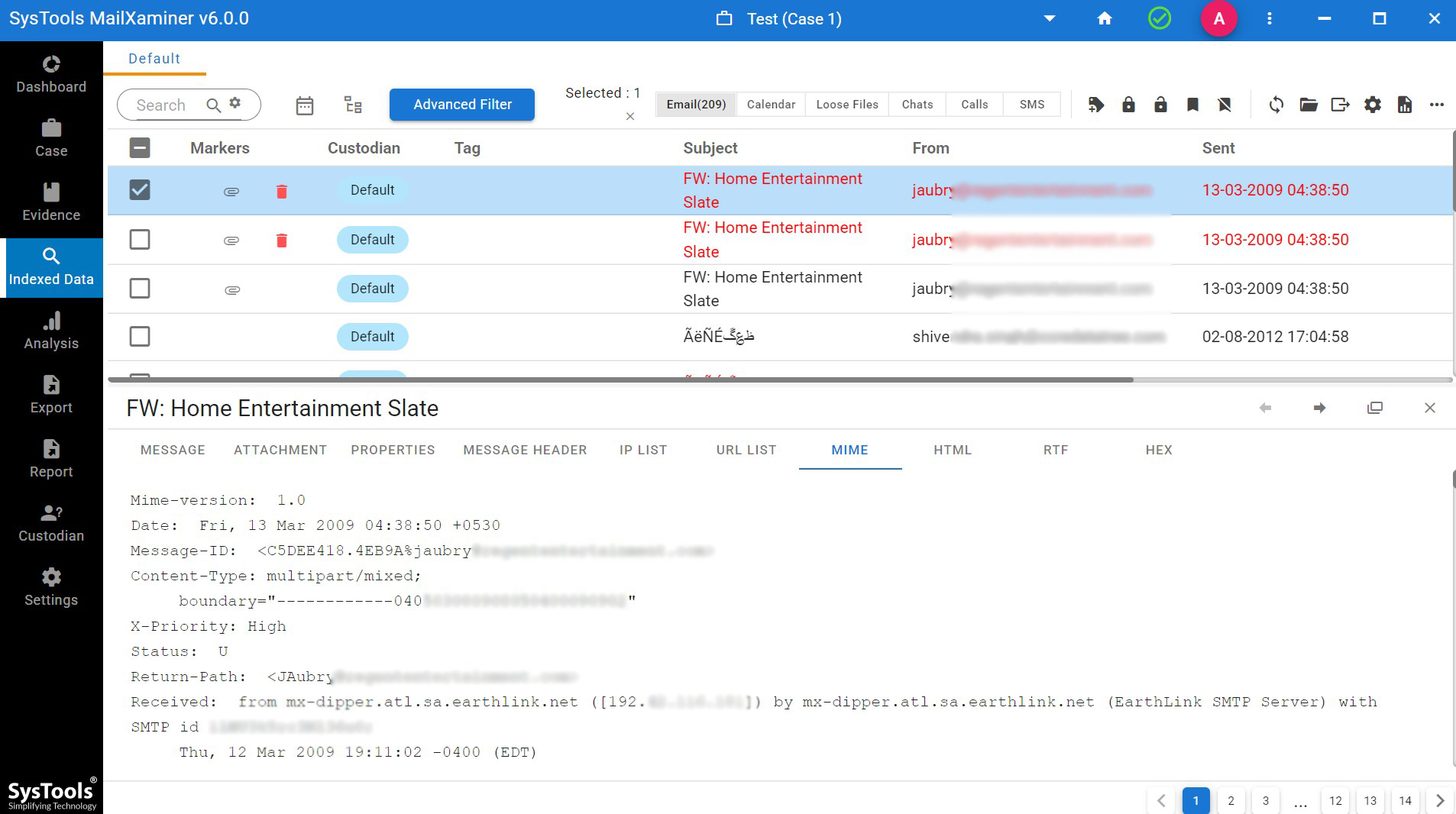
MIME View represents any SMTP mail’s inner details. In this view, the user can easily check the suspected email artefacts.
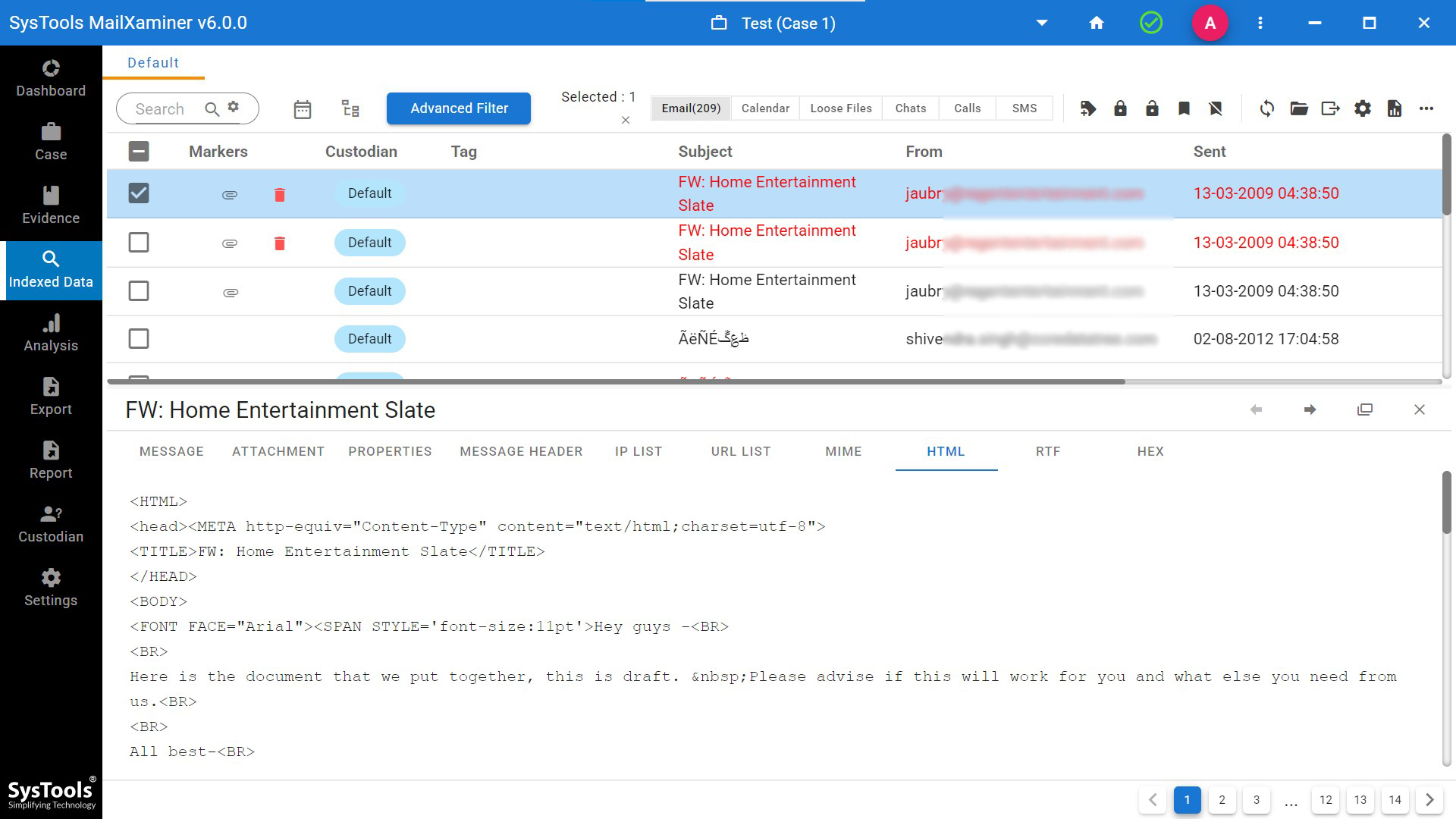
HTML View- In this view, it helps the examiners to perform content analysis by analyzing the internal script or HTML code of the email data file.
RTF View– It helps the investigator to view the data in the original text format. Therefore, it allows the investigator to examine the email data clearly with the actual fonts and formatting used in the RTF Editor. Moreover, when someone composes emails using the RTF Editor consists of a different encoding type, they can view them using this view mode.
Attachment View- Evidently, in this mode, a user does not need to open the entire message to view the attached file. Hence, this view provides direct access to the attachment of selected email files without opening emails individually.
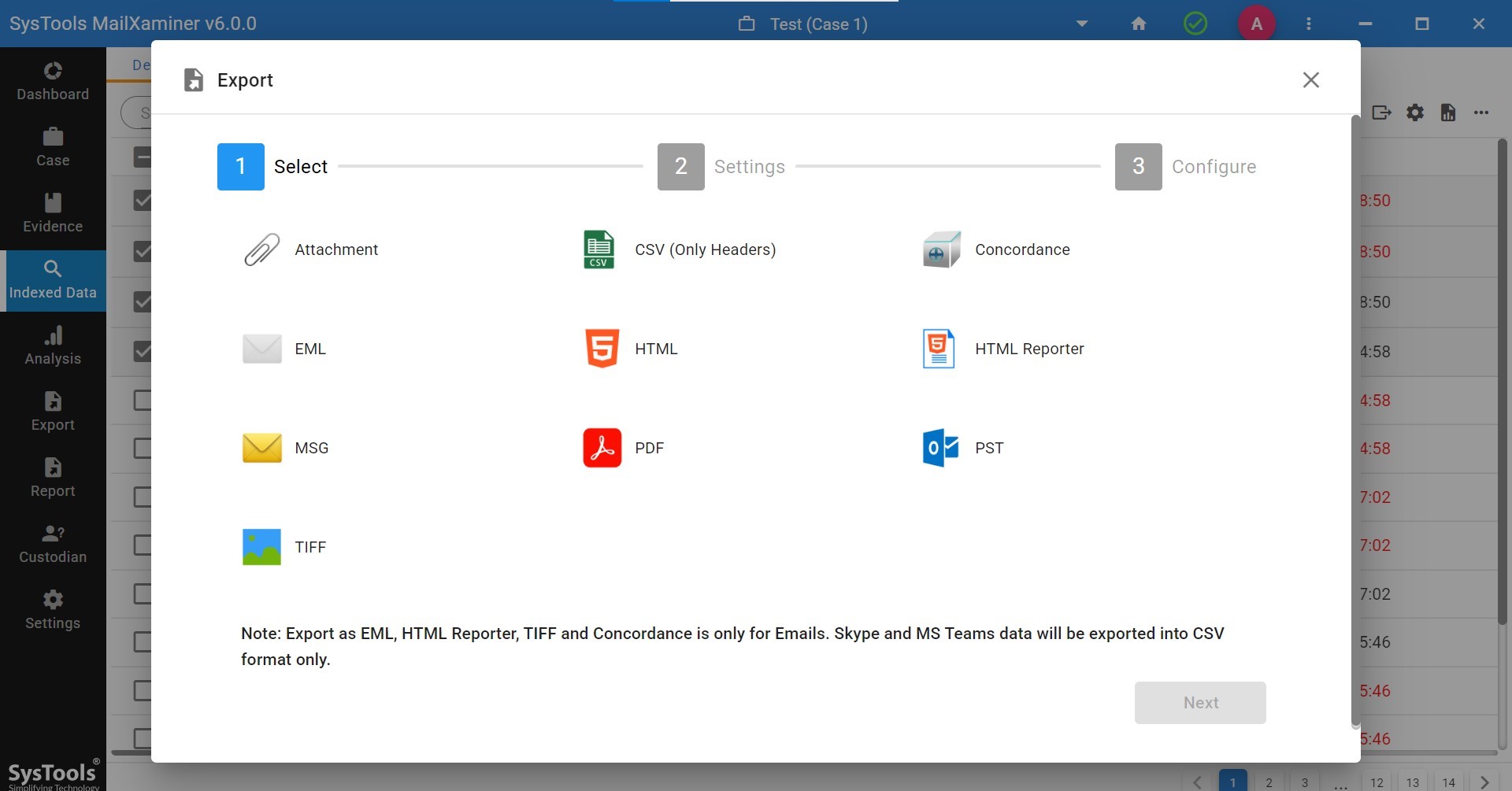
Export and Save Evidence
A forensic analyst should always maintain the stages or steps of investigations involved to find the relevant evidence related to the crime scene. Moreover, it helps the examiners to show the digital evidence collection process regarding the case more accurately in front of judicial authorities. After searching the evidence within, the last stage of the email investigation process is “Reporting”. To make this happen, export the case data and evidence from the examined files into legal file formats like MSG, PDF, Concordance, etc, which benefits the judicial proceedings.
Also, this software allows exporting the evidence report in multiple file formats. Users can select and export the evidence report into any of the available file formats. It also provides the option to save the evidence report at any existing desired destination location into the system.
Conclusion
Now, in this write-up, we have discussed Windows Live Mail forensics, its supported file formats and locations. Here, we also recommend an email forensic tool that can examine the Windows Live Mail files in different views for better analysis. The goal of this software is to fetch sufficient evidence that may allow investigators to successfully prosecute the criminal perpetrator. This software is a fast, accurate, and easy-to-use email forensic software solution.

