Why you Need SHA1 for Forensic Investigation?
SHA-1(Secure Hash Algorithm 1) is a hash algorithm created by the National Security Agency in the US to check the integrity of the data. The SHA1 forensics hash algorithms take small input and generate a string of 160 bits output, also called a 20-byte hash. It is a modified version of MD4. The hash value is a hexadecimal number which is especially 40 digits long. Therefore, it is hard to break this value. Most of the organizations use the SHA1 hash algorithm for password verification.
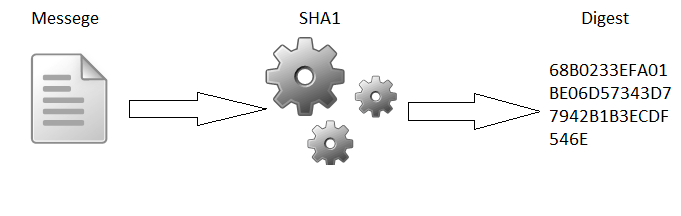
In digital forensic investigation, the hash values are used for recognition, verification and authentication of email messages or any digital data. The hash algorithm is the procedure of applying a numerical function to the digital data. In which, it will create a hash value that acts as the unique identity of the data. If any changes are done to the data, the hash value will also change. For example, the SHA1 hash algorithm is used in the login verification and file confirmation.
- Login Verification: When you create an account in the website, it will generate a unique identifier corresponding to the Username and Password that you have given. That is done with the assistance of SHA1 hash as it changes your information into a checksum. At whatever point you attempt to log in, it will verify the checksum by comparing it with the value stored in the database.
- File Verification: While downloading the file using the SHA1 checksum of the file, the client can easily check that the downloaded file is exactly the same without any changes in it.
In the investigation process, the SHA1 message digest is used as checksum value during the acquisition of electronic data. This value helps to check the integrity of the data that is whether the data is altered by anyone. On the other hand, if an attempt is being made to manipulate the data then automatically the SHA1 forensics hash values will also change. Therefore, the comparison of SHA1 values will help to detect data modification and it has become the most helpful tip for investigating officers.
SHA1 Algorithm Analysis with Forensics Software
Using MailXaminer, an email forensics software, SHA1 forensics hash algorithm implementation can be easily done. Moreover, it helps to examine and identify misrepresented emails by comparing the SHA1 value of each email. Furthermore, users can filter the suspected email from the bulk emails with the help of the SHA1 option. In order to avail SHA1 message digest, make sure to enable SHA1 option from the software panel. Following are the steps to analyze emails based on SHA1 forensic hash values.
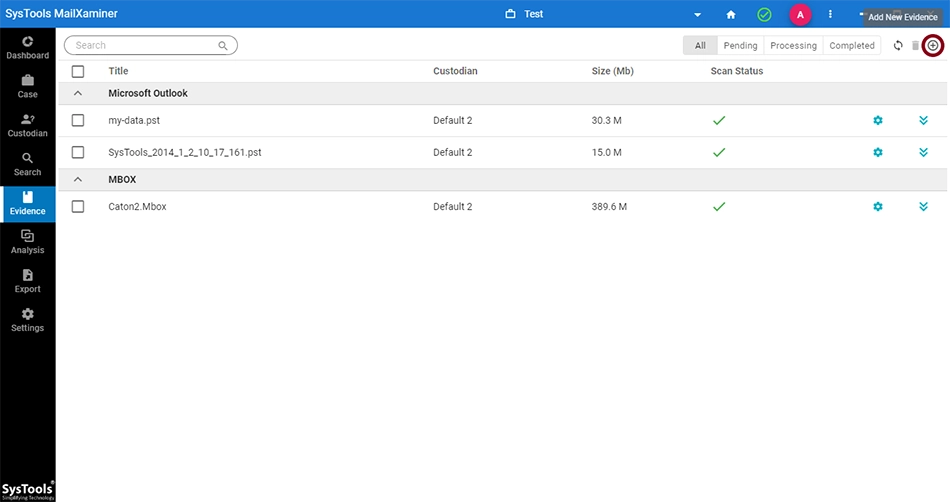
If the user has already created a case, then the user has to ad a new evidence file for analysis using the Add Evidence button.
Now, from the Add Evidence screen, go to Hash Settings and tick the box corresponding to SHA1 option and provide the other required details.
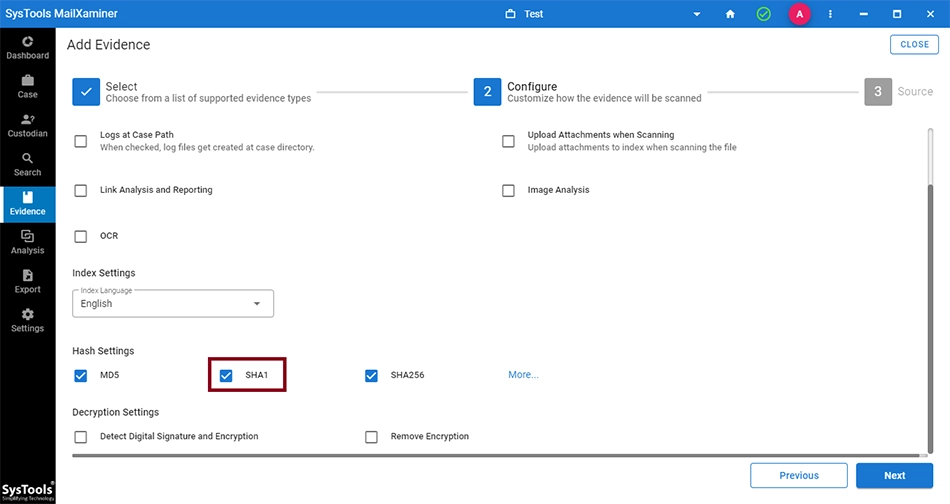
These settings can also be applied in the Settings tab under the Evidence screen.
If the SHA1 option is checked, the software will automatically scan the hash values of all the emails. Then, the user can preview the message digest of all the emails generated by the SHA1 forensics hash algorithm by going to the Properties section of the Email preview.
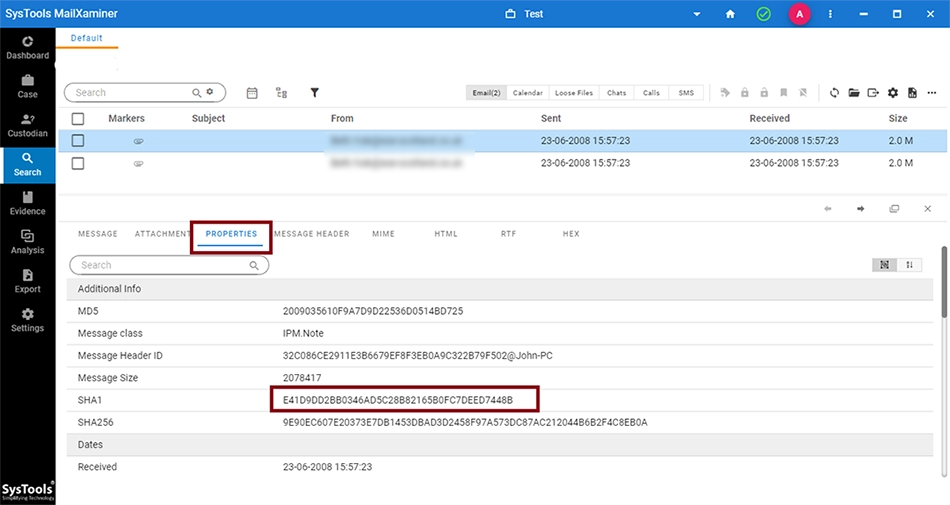
If the user has not selected the corresponding checkbox during the evidence scan process, the software will not generate any hash value.
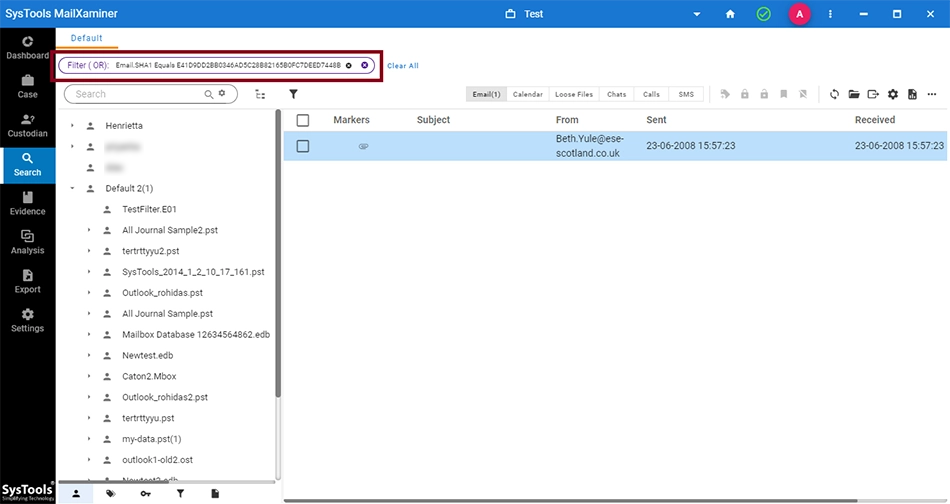
User can search any email using its Hash value. To do this, open the Filter screen in the Search tab. Once the window opens up, choose the relevant field and provide the operator for search. Now, enter the Hash value for search. After providing all necessary information, click on View Results.
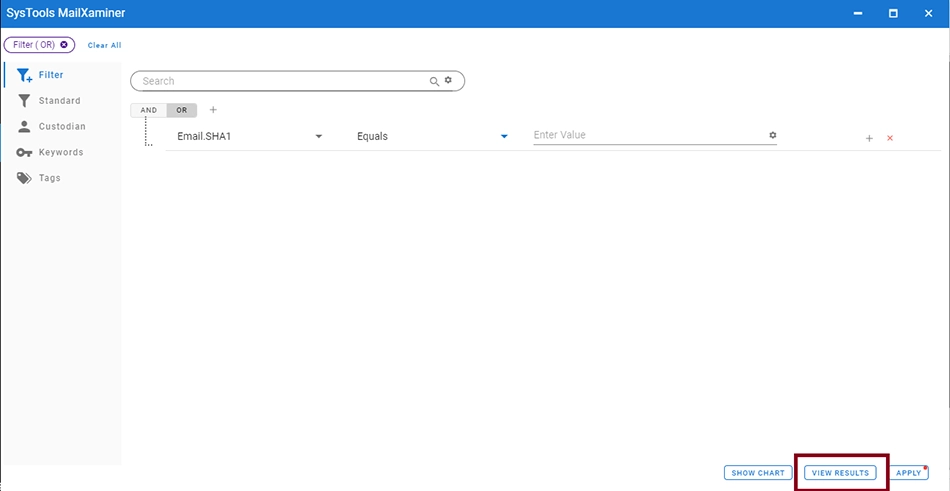
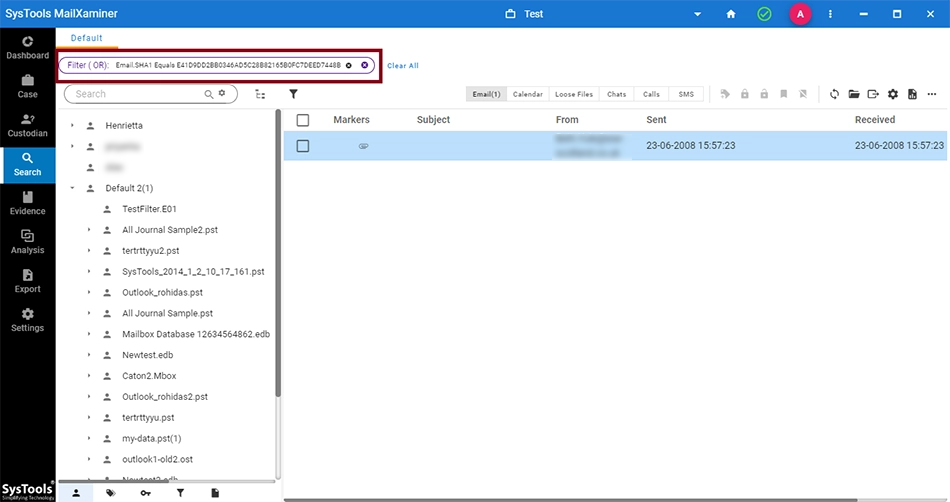
The results for the SHA1 hash value search are displayed. The filter query entered for the search is displayed on top of the screen.
MD5 Hash Algorithm in Forensic Investigation
MD5 (Message Digest Algorithm 5) is the widely using hash algorithm, initially created as a cryptographic hash function. It is also known as the one way cryptographic hash function because it accepts the message of arbitrary length. Moreover, it generates MD5 hash digest of 128 bit to authenticate the original message.
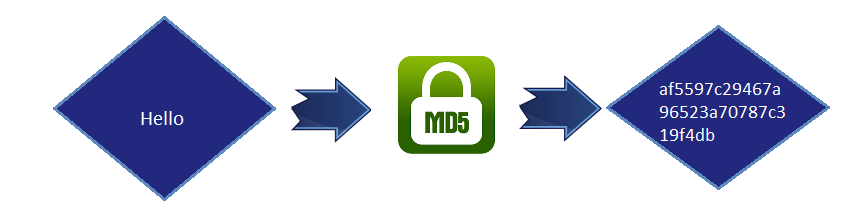
MD5 hashing algorithm converts a message into a 128-bit message digest. It takes the plain text of 512-bit blocks and divides it into 16 blocks, each of 32 bits and gives the output of 128 bit which is a set of 4 blocks.
MD5 is structured by Ronald Rivest as an improvement for the MD4 algorithm. MD5 message digest algorithm intended for digital signature applications wherein large files need to be compressed before the encryption. The MD5 hash values are used as a checksum for checking the message integrity and identifying the modified emails by comparing the hash values. Furthermore, it is also used for non-cryptographic usage such as to find the partition on a specific key.
Characteristics of MD5 Hash Algorithm
- It is also known as the one-way hash function.
- Accept arbitrary message and generate a fixed-length message digest.
- It is the extension of the MD4 algorithm.
MD5 forensics hash algorithms are commonly used for two functions such as “Data Integrity Check and Validation of Emails”.
- Data Integrity check: MD5 forensics hash values help the investigators to verify that the data or the evidence collected is not altered by anyone. The comparison of MD5 hash digest helps to find the change that has been occurred on the original data. Besides this, it also helps to check the misplaced byte during the transfer of important files.
- Validation of Emails: Another important aspect of MD5 is that it allows to verify that the correct email data has been received on the receiver side. For this, the sender will generate an MD5 message digest using the private key and send it to the receiver. On the receiver side, the user will verify the data by regenerating the digest using the public key and compare with the received hash value.
MD5 Algorithm Analysis with Forensics Software
MD5 forensics hash algorithms lets the investigating officers to compare and verify the integrity of the digital evidence during the cybercrime investigation. The inbuilt feature of the computer forensics tool automatically calculates the MD5 forensics hash values. This makes the analysis process easy by saving processing time. The upcoming section will help to understand how the forensics hash analysis can be performed using the remarkable MailXaminer email forensics software.
To add a new evidence into the software, the user can use the Add Evidence button in the Evidence tab. The MD5 checkbox has to be selected at the time of adding the evidence to get the hash values generated.
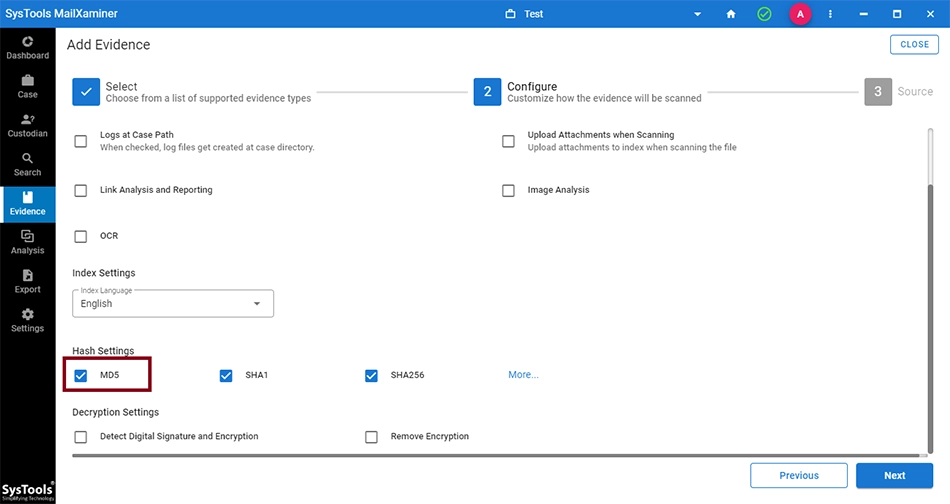
Hash settings are also a part of the Global Settings provided for the case. User can also use these options in the settings tab.
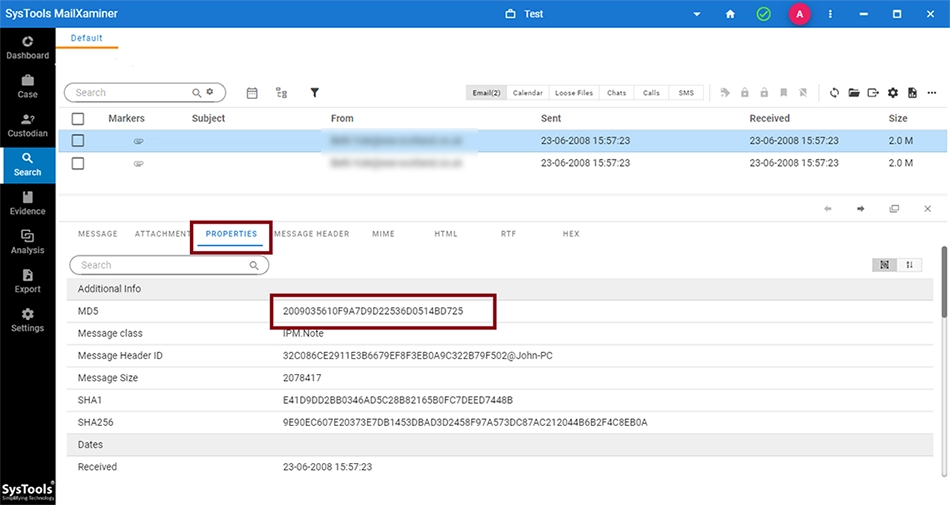
After the evidence is imported into the software using the above mentioned settings, the user can preview any Emails to find the MD5 hash value of a particular email.
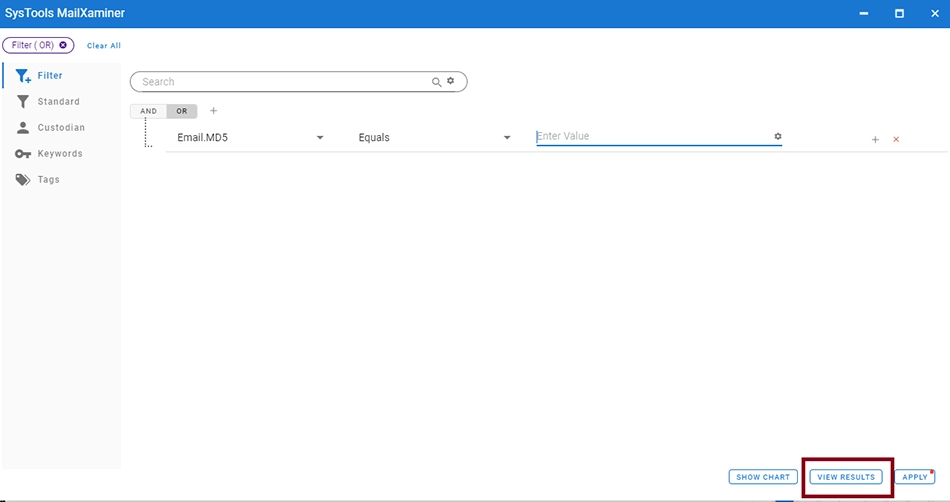
Users can search any email using its Hash value. To do this, open the Filter screen in the Search tab. Once the window opens up, choose the relevant field(in this case - Email.MD5) and provide the operator for search. Now, enter the Hash value for search. After providing all necessary information, click on View Results.
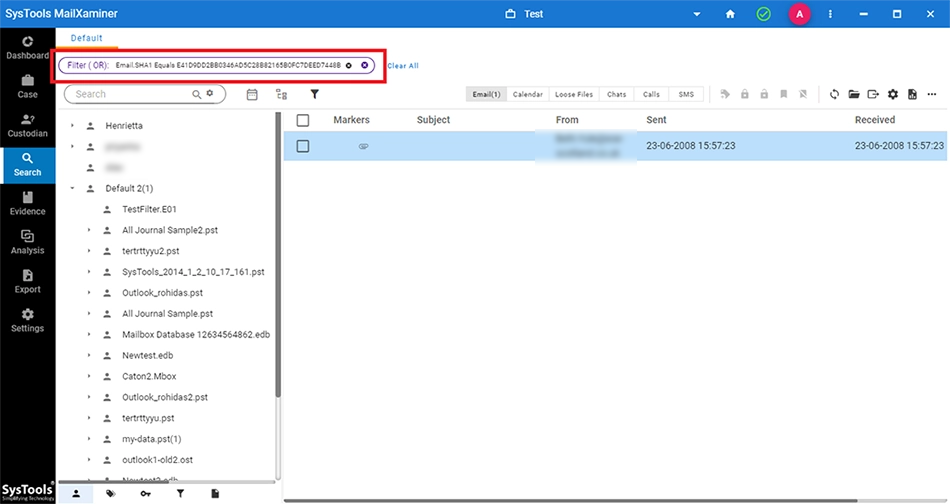
The search result for the MD5 hash value are displayed in the format shown below. The software also shows the Filter Query at the top of the screen.
SHA256 Forensics Hash Algorithm
SHA256 (Secure Hash Algorithm 256) is a hash algorithm with the digest length 256 bit. This algorithm forms two hash functions of different word sizes, also known as SHA-512 and SHA-256. The SHA-256 consists of a range of 32-bit word value whereas SHA-512 consists of a range of 64-bit word value.
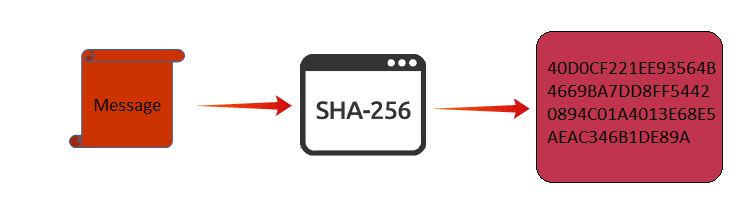
SHA256 forensics hash values are commonly used for authentication, verifying the transactions and calculating the proof of work. In the digital forensic investigation, the SHA256 hash digest is used to verify the integrity of the evidential data. Moreover, it helps to ensure that the collected digital evidence is original and it is not modified.
SHA256 Hash Analysis with Proven Email Forensics Software
SHA256 hash algorithm permits investigators to compare and verify the digital evidence during forensic investigation seamlessly. The forensic tool has the ability to calculate the SHA256 hash value. This feature makes the analysis process easy for the investigators by saving time and effort. In this section, we will discuss how a forensic tool helps in the forensic hash analysis.
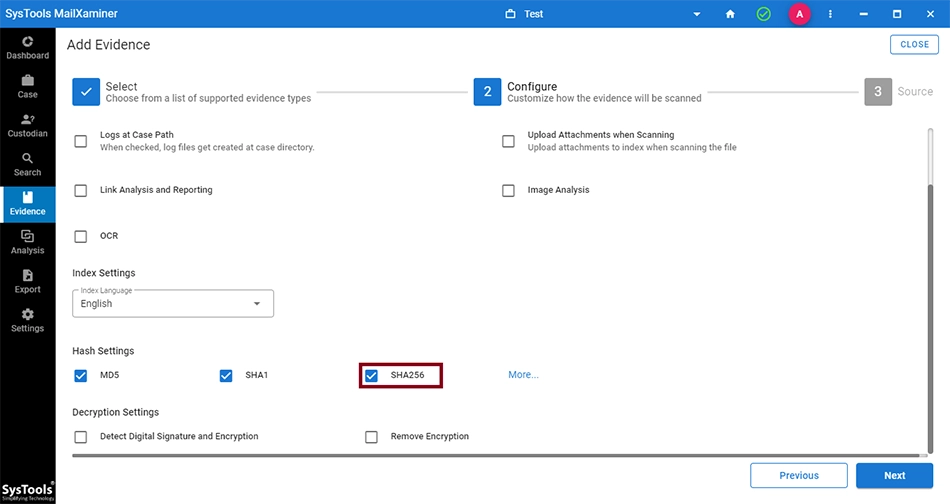
To examine emails with SHA256 hash value, first you have to enable SHA256 option before adding the file. Now, to enable the SHA256 option, simply click on the SHA256 option under Hash Settings while providing other options for evidence scan.
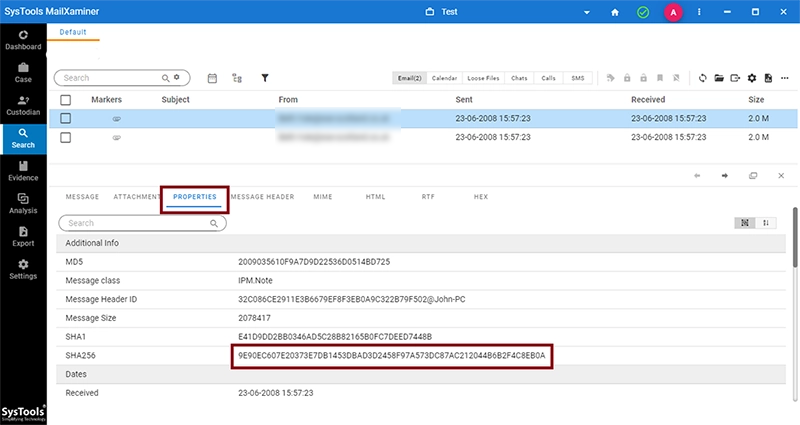
The SHA256 hash value for any mail can be viewed in the mail preview screen under Properties tab.
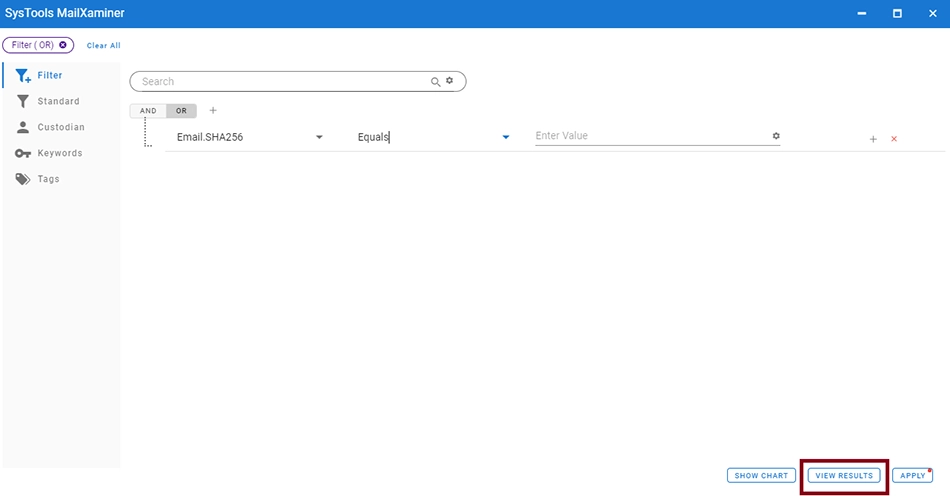
User can search any email using its Hash value. To do this, open the Filter screen in the Search tab. Once the window opens up, choose the relevant field and provide the operator for search. Now, enter the Hash value for search. After providing all necessary information, click on View Results.
The results of the SHA1 hash value search are displayed. The filter query entered for the search is displayed on top of the screen.