Guide
Master Your Investigation Journey
Navigate with Confidence through MailXaminer's Comprehensive Guide
Guide
Navigate with Confidence through MailXaminer's Comprehensive Guide
TABLE OF CONTENT FOR FORENSIC EVIDENCE COLLECTION TOOL
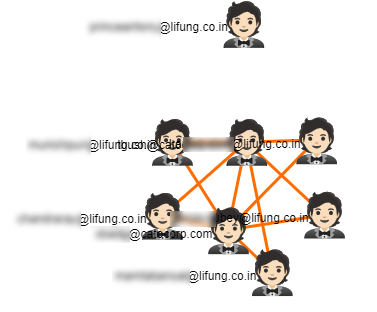
Advance Link Analysis Intelligence
Visualize, analyze, and investigate the nefarious communication between any number of suspects with the advance link analysis mechanism integrated in the tool. Easily interpret the link between the suspects as well as investigate the emails and information exchanged. Find relationship between multiple users with Advanced Search Operators. Examine and visualize the exchanged email communication between them using the suspected keywords.
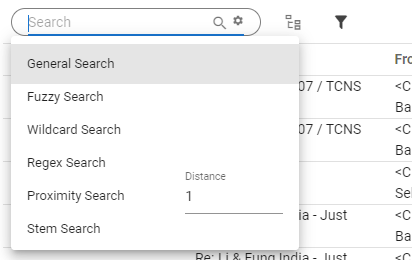
Hi-Tech Search With Operators
After Forensics Recovery & Analyzing process, you can search for evidence in email & contacts body (To, Cc, Bcc, Subject, First name, Last Name, Sender Name etc.) using different operators. Also search evidence from attachments & remove duplicate searched email evidence.